Sensitive label track data publishing method using graph difference privacy model
A trajectory data and differential privacy technology, applied in the field of information security, can solve problems such as user personal information privacy leakage, and achieve the effect of solving privacy leakage, ensuring usability, and good user service
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to express the purpose, technical solutions and advantages of the present invention more clearly, the present invention will be further described in detail through the following examples and accompanying drawings.
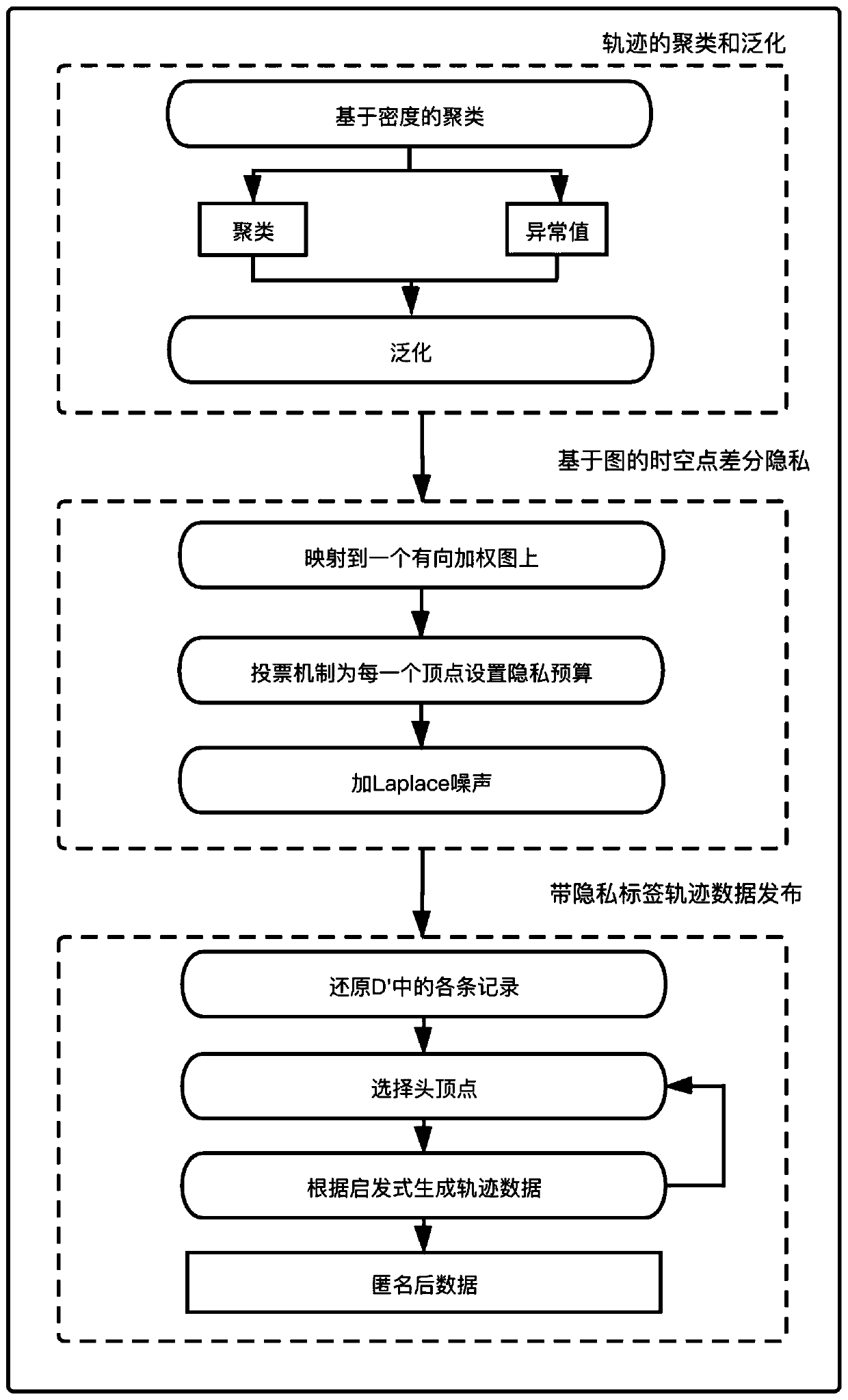
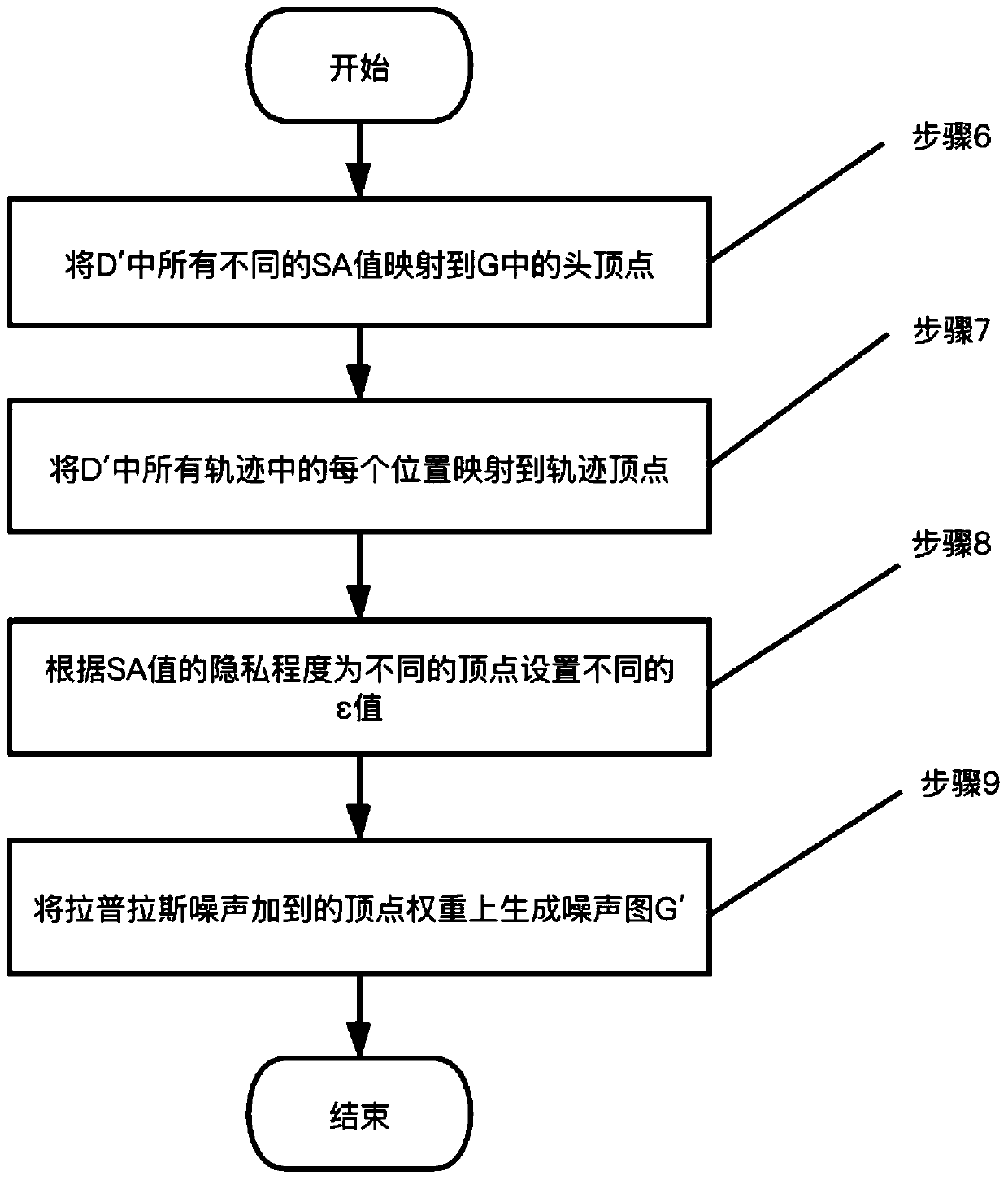
[0036]A sensitive label trajectory data publishing method based on the graph differential privacy model, including trajectory clustering and generalization, graph-based spatiotemporal point differential privacy, and three-stage processing of publishing trajectory data with privacy labels;
[0037] first stage, see figure 2 , the specific operation process of trajectory clustering and generalization is as follows:
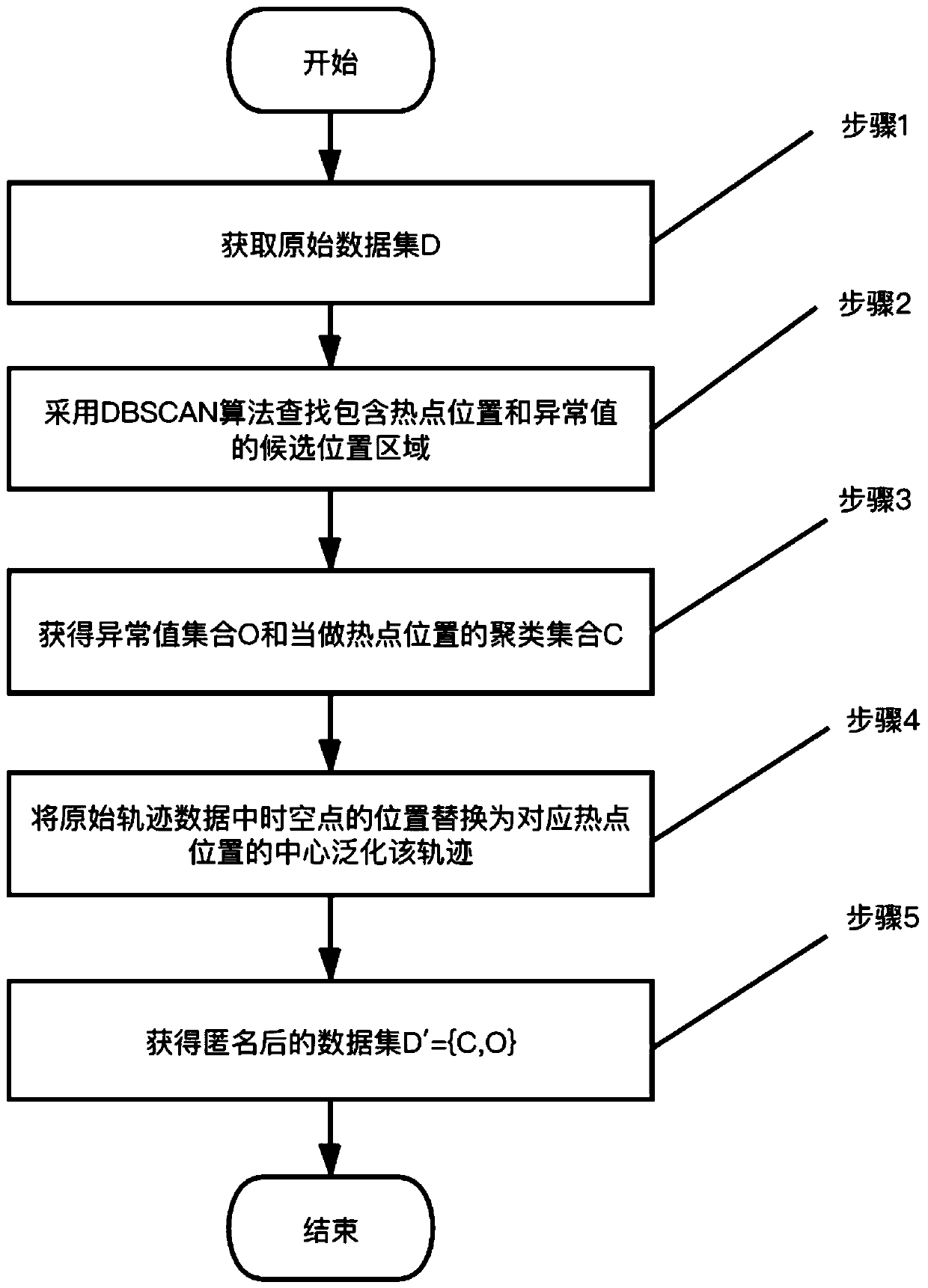
[0038] Step 1. Obtain the original trajectory data set D.
[0039] Step 2. Use the DBSCAN algorithm to find candidate location areas containing hotspot locations and outliers. A hotspot location is an area where spatio-temporal points are relatively dense, such as buildings (shopping malls, hospitals, etc.) or road intersections and ot...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com