Machine learning-based attack detection method for non-analyzable network data feature selection
An attack detection and machine learning technology, applied in machine learning, instruments, computer components, etc., can solve the problems of poor model robustness, variable attack forms, lack of research on encrypted and unanalyzed network data attack detection, etc. To achieve the effect of reducing the occurrence of safety accidents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the above objects, features and advantages of the present invention more comprehensible, specific implementations of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0030] In the following description, a lot of specific details are set forth in order to fully understand the present invention, but the present invention can also be implemented in other ways different from those described here, and those skilled in the art can do it without departing from the meaning of the present invention. By analogy, the present invention is therefore not limited to the specific examples disclosed below.
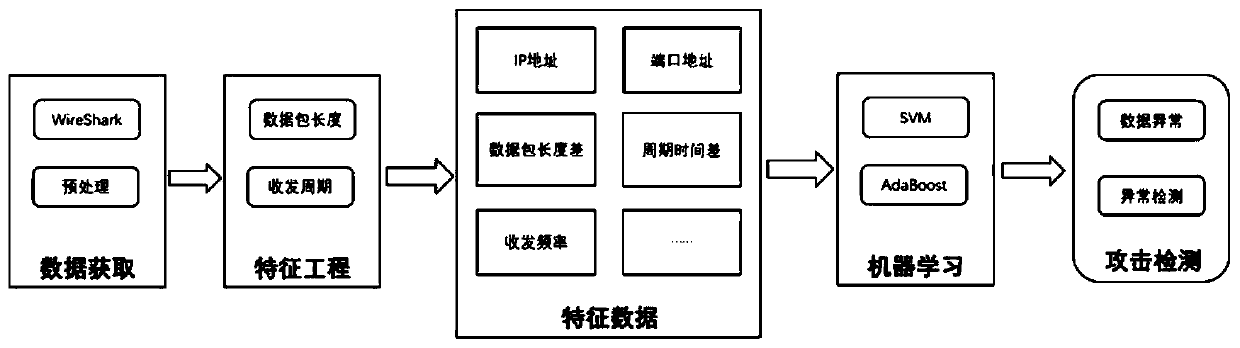
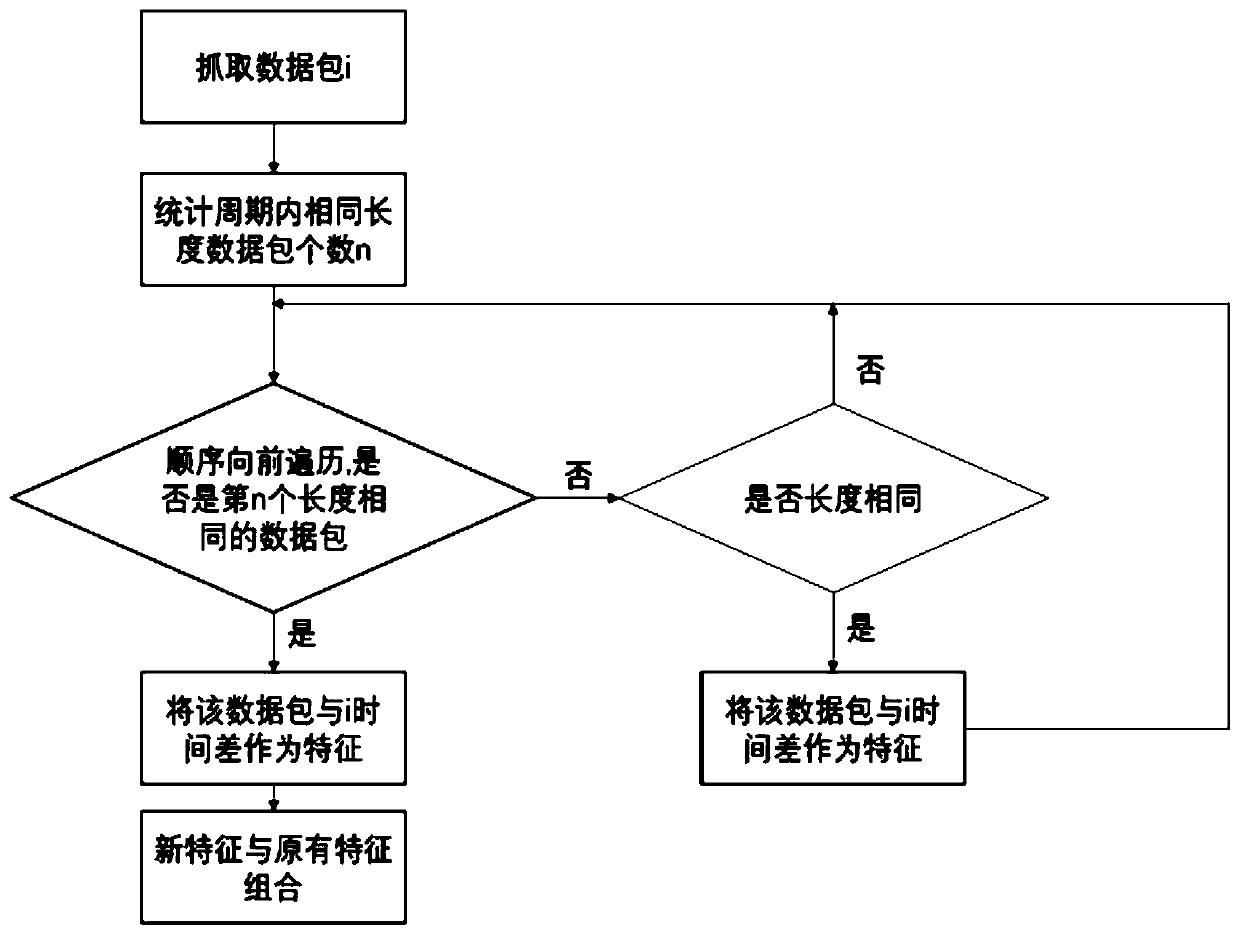
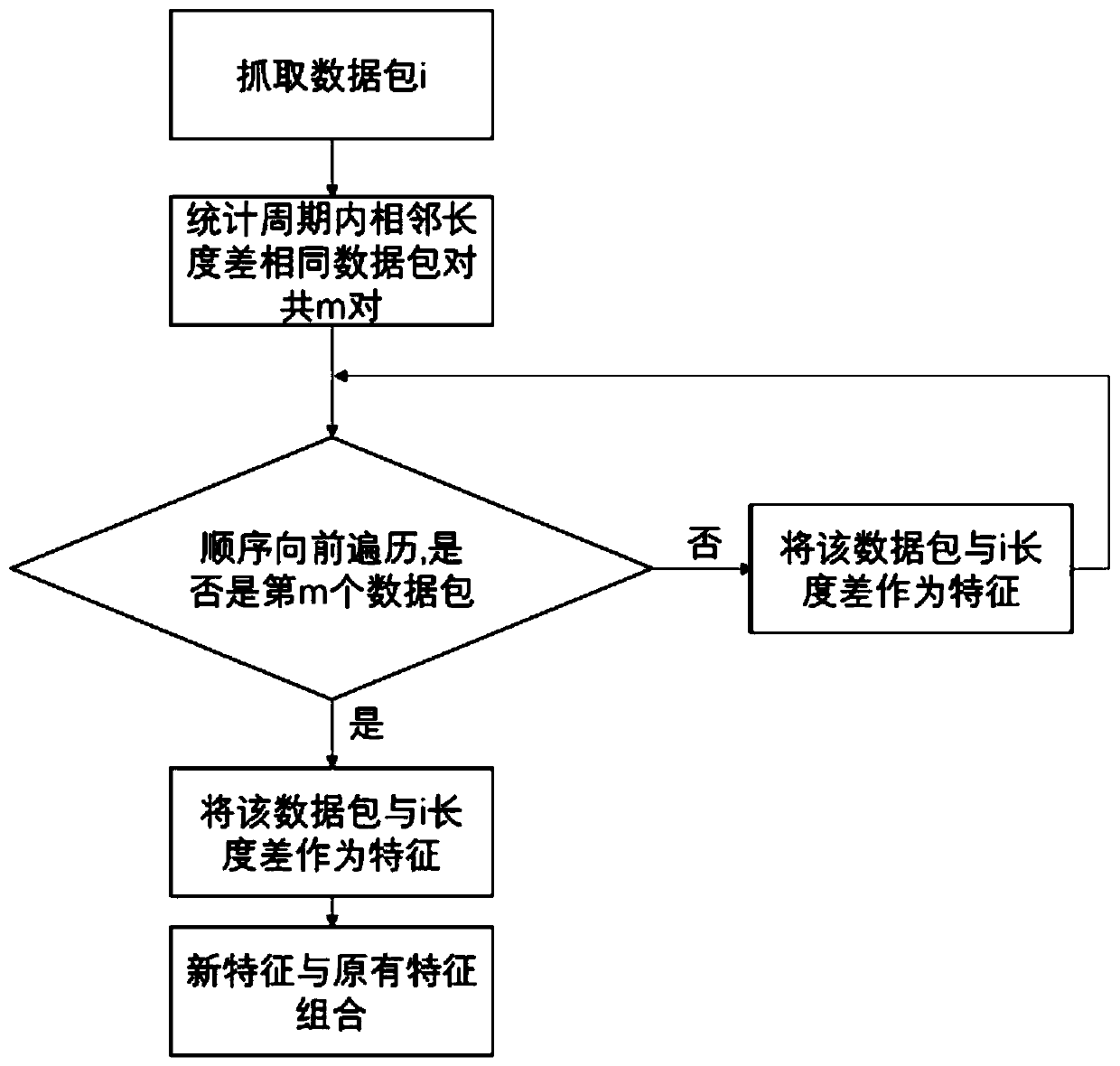
[0031] Using a typical industrial control network security test platform, the on-site control layer adopts the domestic SUPCON ECS700 controller, and the on-site device layer uses cascaded water tanks as the control object. The industrial control network attack detection process is given, including the following...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com