Quantum trust model construction method and computer-readable storage medium
A trust model and construction method technology, applied to secure communication devices and key distribution, can solve problems such as weak anti-channel interference, collapse, and quantum resource degradation, so as to achieve good particle usage efficiency, resist noise interference, and save quantum resources Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
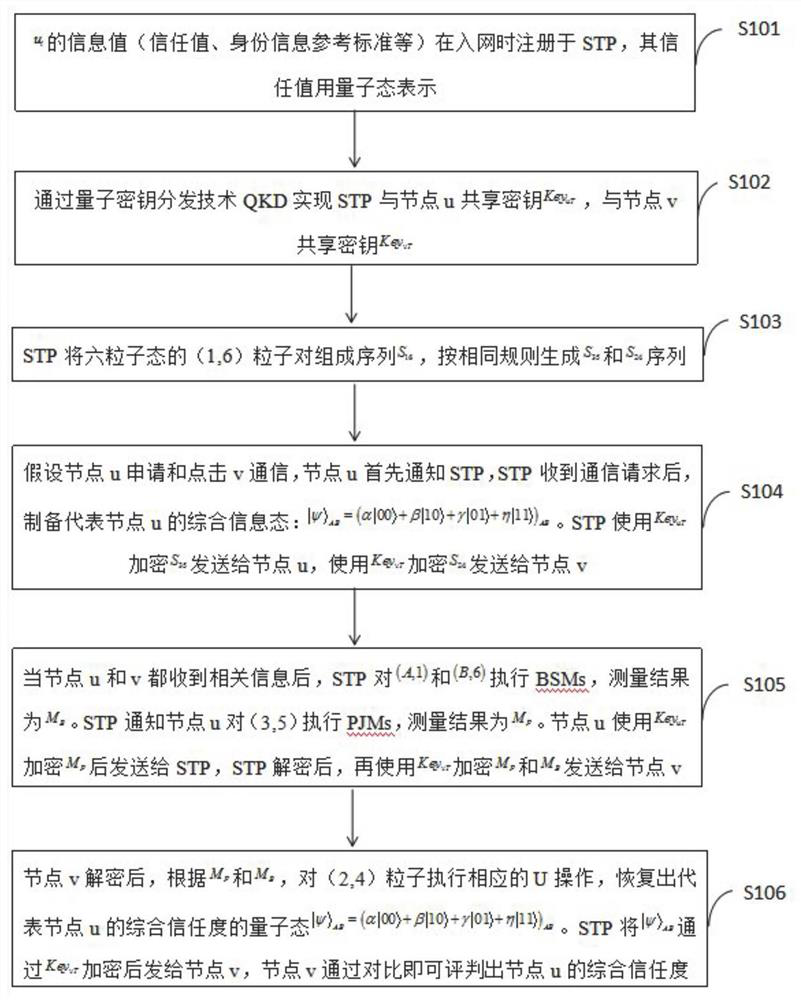
[0088] 1. Program theory knowledge
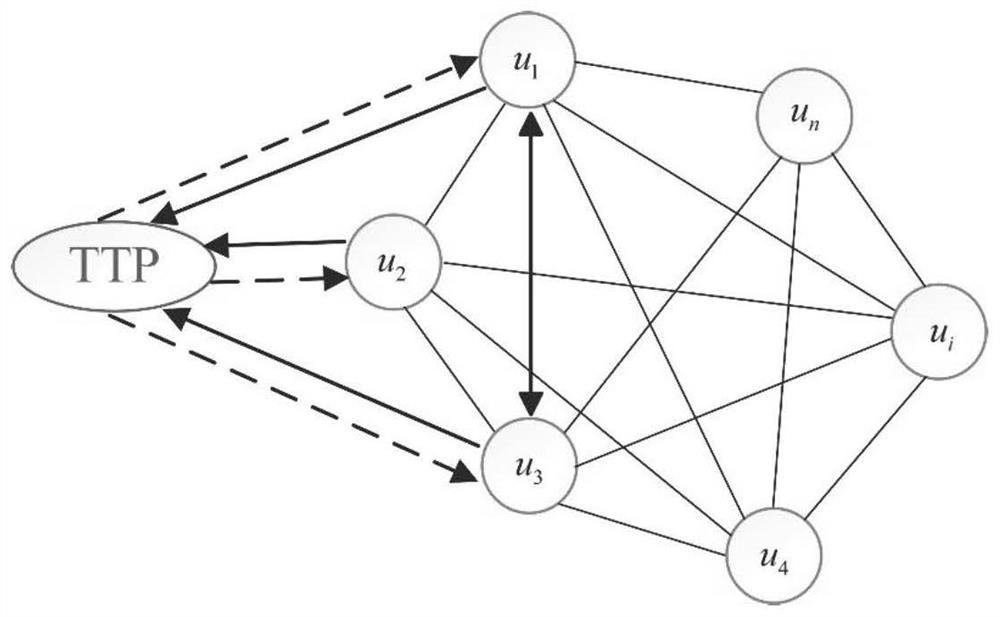
[0089] 1.1 Quantum trust model based on node trust evaluation
[0090] In the quantum communication network trust, the present invention mainly analyzes two interrelated trust relationships:
[0091] (1) Target trust (trust of target nodes) is evidence-based trust, which can be accurately described, inferred and verified.
[0092] (2) Subjective trust (the trust of the subject node, that is, the mixture of individuals, groups or people and object nodes), as a cognitive phenomenon, is the subjective judgment and subjective belief of specific characteristics or behaviors on the subject node. This subjective judgment is independent of the monitoring of the subject's personality and behavior. Subjective trust is the premise of objective trust, and objective trust is based on trust with great uncertainty (expressed as randomness, ambiguity and diversity). It is difficult to accurately describe and verify. Therefore, the difficulty in formali...
Embodiment 2
[0134] Example 2: Protocol Analysis
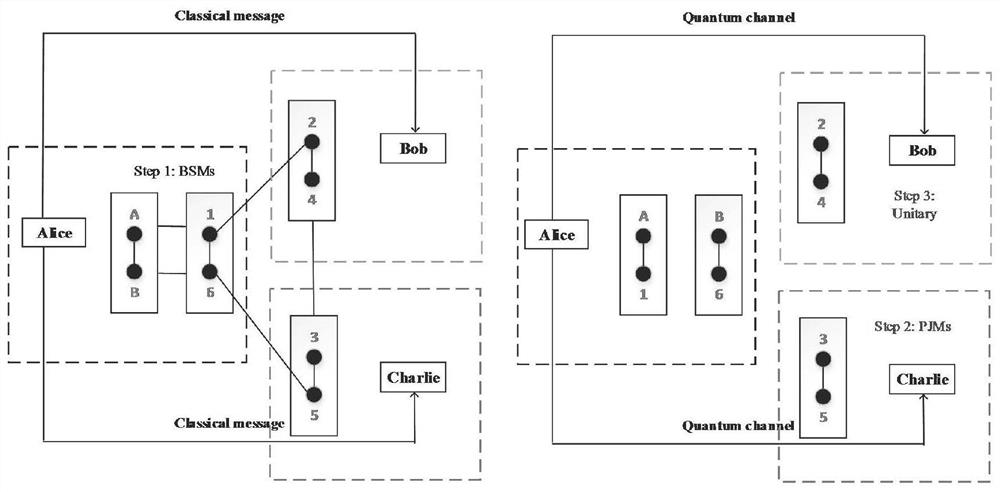
[0135] 1), internal attack
[0136] Suppose node u cooperates with attacker Eve to deceive node v, and Eve intercepts the particle pair sent by STP to node v. However, neither node u nor Eve can successfully restore the proper particle state required by Quantum Teleportation. Moreover, both STP and node v can judge node u by calculating its trust value when it is registered, so internal attacks will not be able to obtain any useful information and will definitely be detected.
[0137] 2), external attack
[0138] Analyzing the protocol steps shows that if the external attacker Eve wants to forge the trust value |ψ> AB , then Eve must obtain the key Key uT and Key vT Information. However, QKD and the one-time pad (QOTP) cipher book guarantee the absolute security of the key. Assume that Eve has obtained the information of the two keys, but without the assistance of STP, Eve still cannot obtain any useful information about the six-par...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com