Implementation method of SM4-like cryptographic algorithm
A technology of cryptographic algorithm and implementation method, which is applied in computing, computer security devices, encryption devices with shift registers/memory, etc., and can solve problems such as low-round SM4 algorithm security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] In order to further illustrate the features of the present invention, please refer to the following detailed description and accompanying drawings of the present invention. The accompanying drawings are for reference and description only, and are not intended to limit the protection scope of the present invention.
[0023] Such as figure 1 As shown, this embodiment discloses a method for implementing a class SM4 cryptographic algorithm, including the following steps S1 to S5:
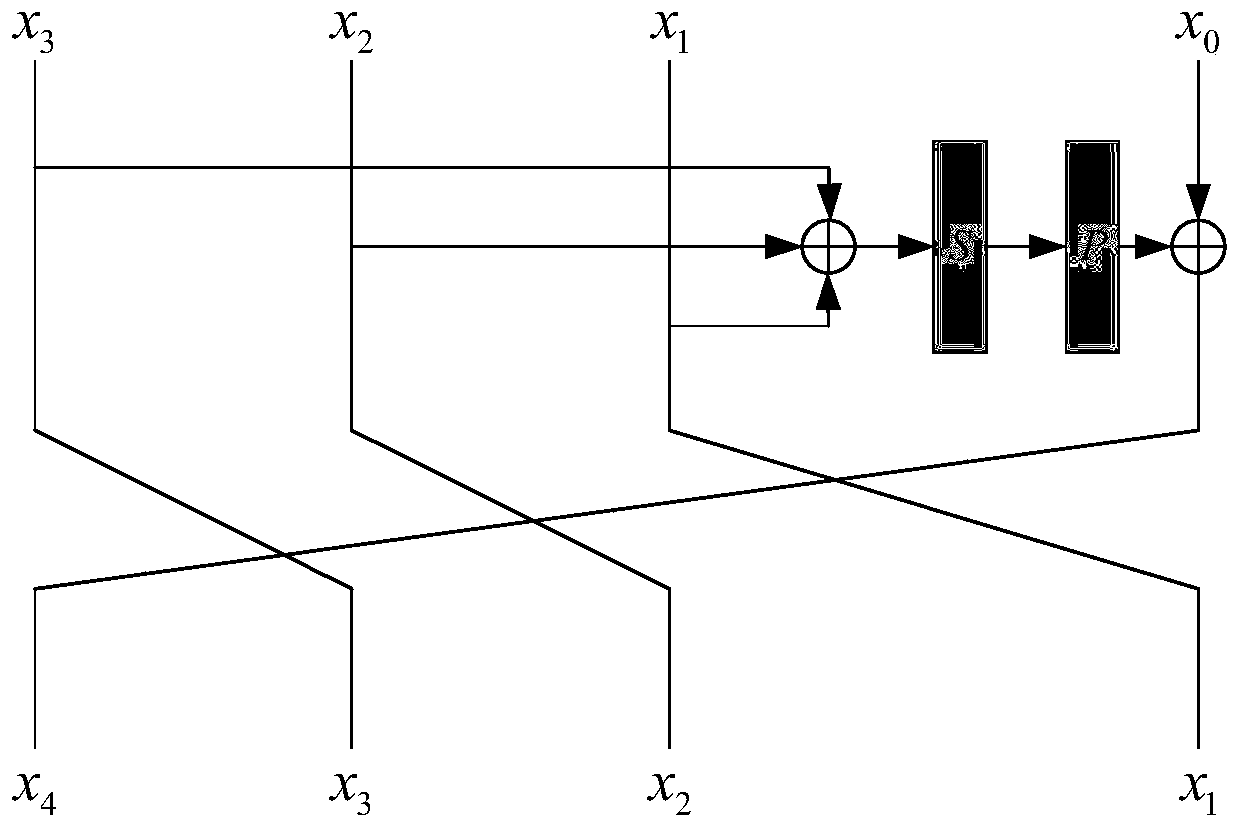
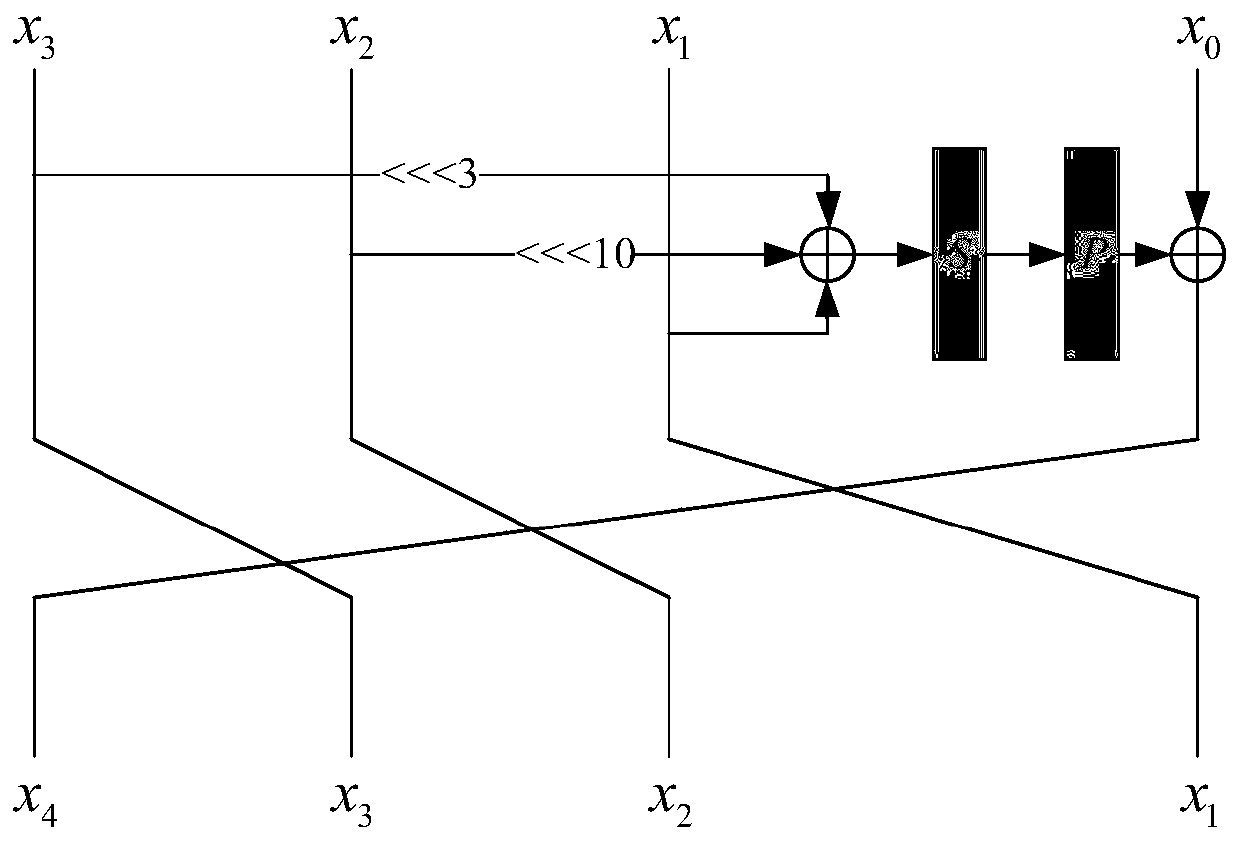
[0024] S1. Grouping the file data to be encrypted to generate multiple pieces of data, the multiple pieces of data are divided into the first type of input data and the second type of input data;
[0025] S2. Perform a cyclic shift operation on at least two pieces of data in the first type of input data to obtain preprocessed first type of input data;
[0026] S3. After performing the first XOR operation on the preprocessed input data of the first type, they are sequentially input to the S box ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com