Cooperative physical layer security implementation method based on interference node optimization layout
A technology of physical layer security and interfering nodes, which is applied in the field of wireless cooperative physical layer security implementation based on the optimal layout of interfering nodes, can solve the problems of no key research, low security capacity, and limited effect of cooperative physical layer security implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
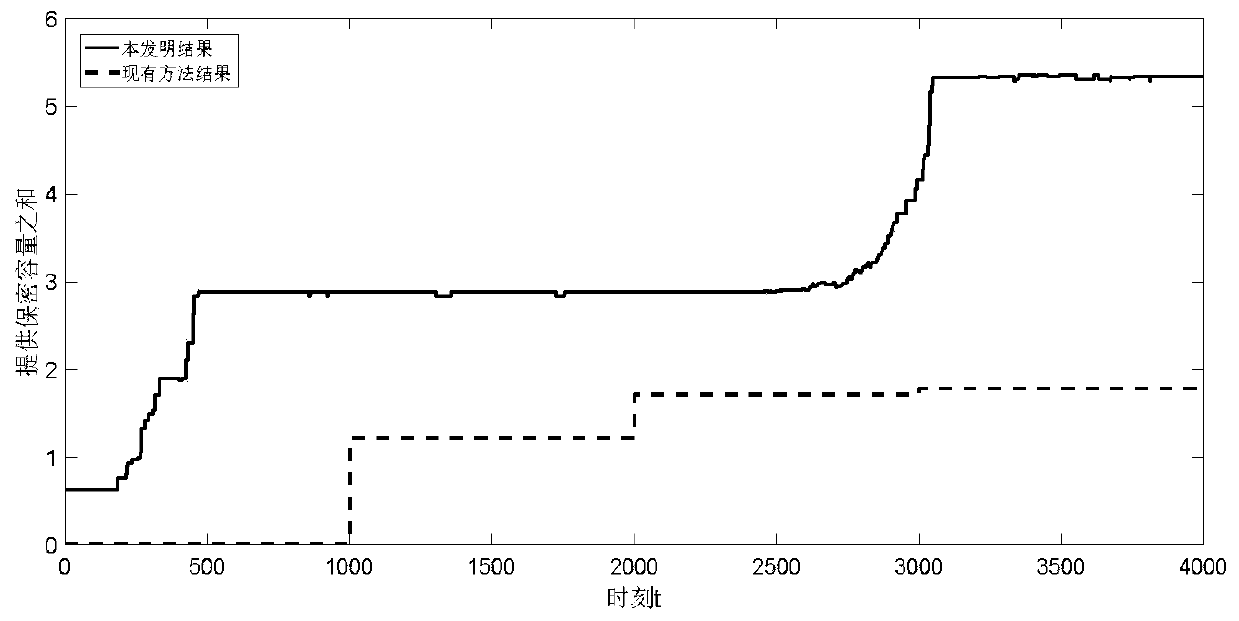
[0059] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
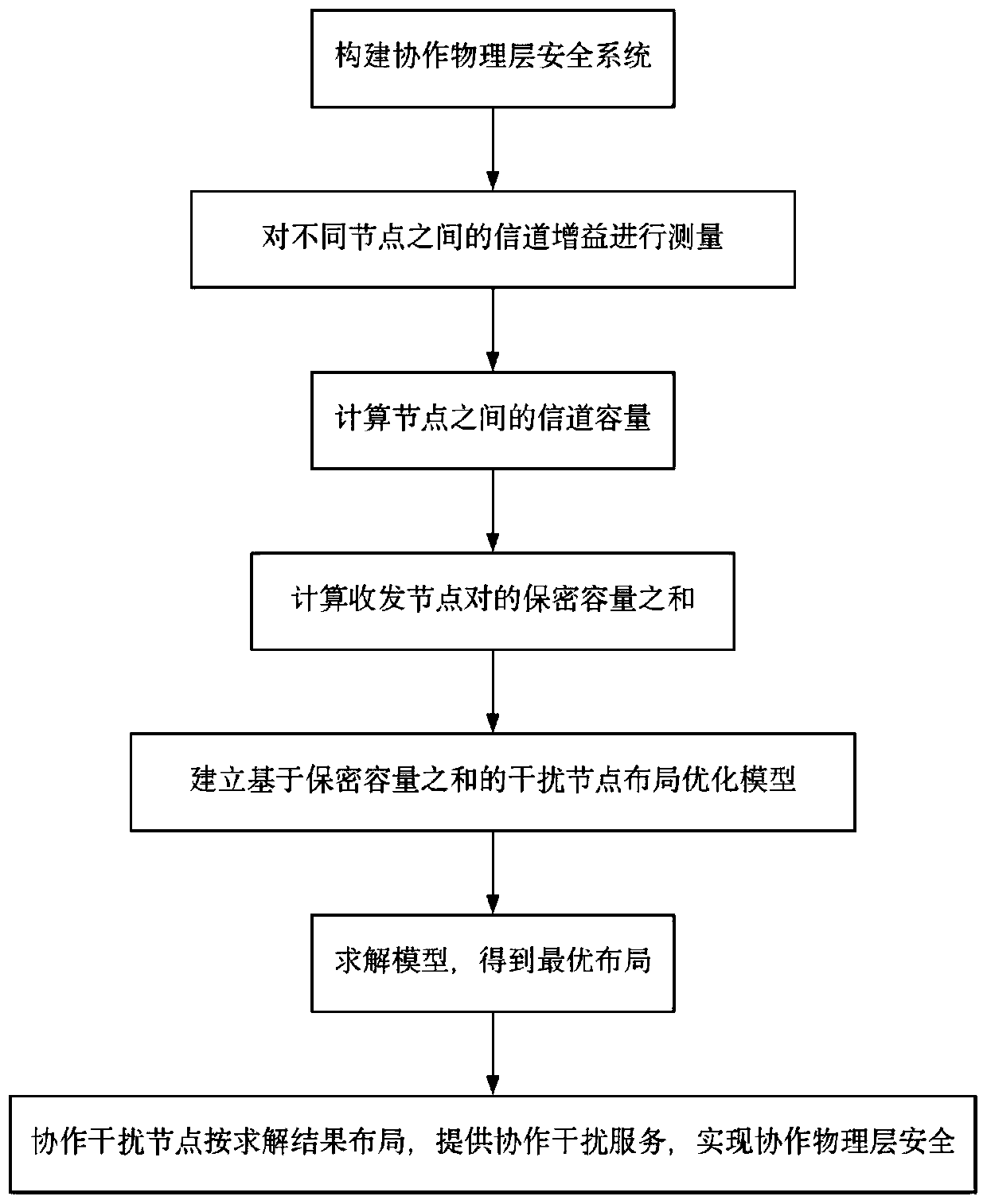
[0060] refer to figure 1 , the present invention comprises the following steps:
[0061] Step 1) Build a collaborative physical layer security system:
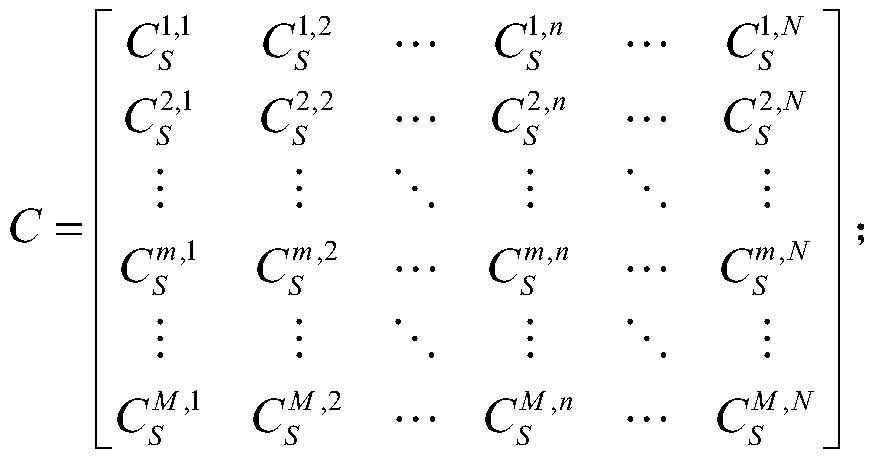
[0062] Construct a transceiver node pair (s 1 , d 1 ),(s 2 , d 2 ),...,(s n , d n),...,(s N , d N ), M cooperative interference nodes j 1 ,j 2 ,...,j m ,...,j M and the cooperative physical layer security system of the eavesdropping node E, where, s n Indicates the nth source node, d n Indicates the nth destination node, j m Indicates the mth cooperative interference node, N≥M≥1; at time t, the cooperative interference node j m The position is L m (t), to (s 1 , d 1 ),(s 2 , d 2 ),...,(s n , d n ),...,(s N , d N ) provides cooperative jamming service, let j m The sending and receiving nodes served at the current moment are expressed as p m (t) represents...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com