Face recognition security alarm method based on embedded artificial intelligence chip
A face recognition and artificial intelligence technology, applied in the field of intelligent recognition, can solve problems such as long delay, data loss, push, etc., to solve the problem of real-time security, low cost, and reduce the effect of intermediate processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
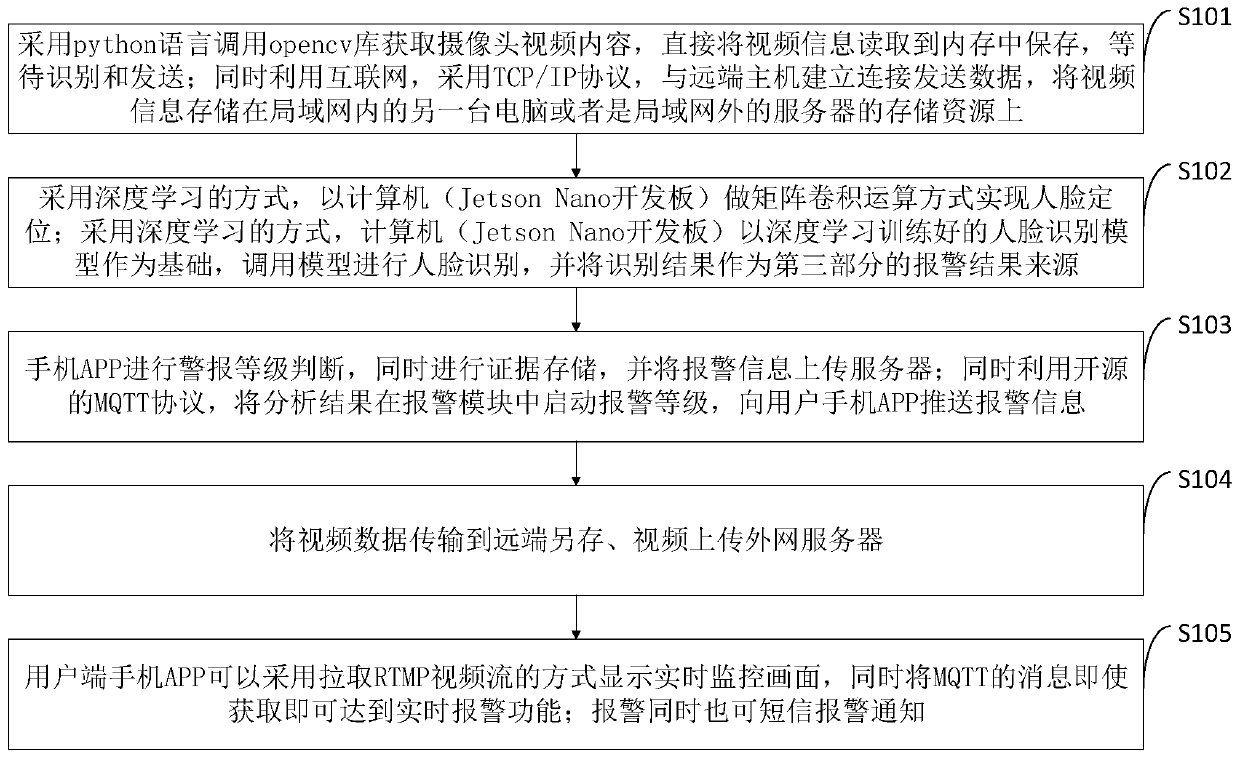
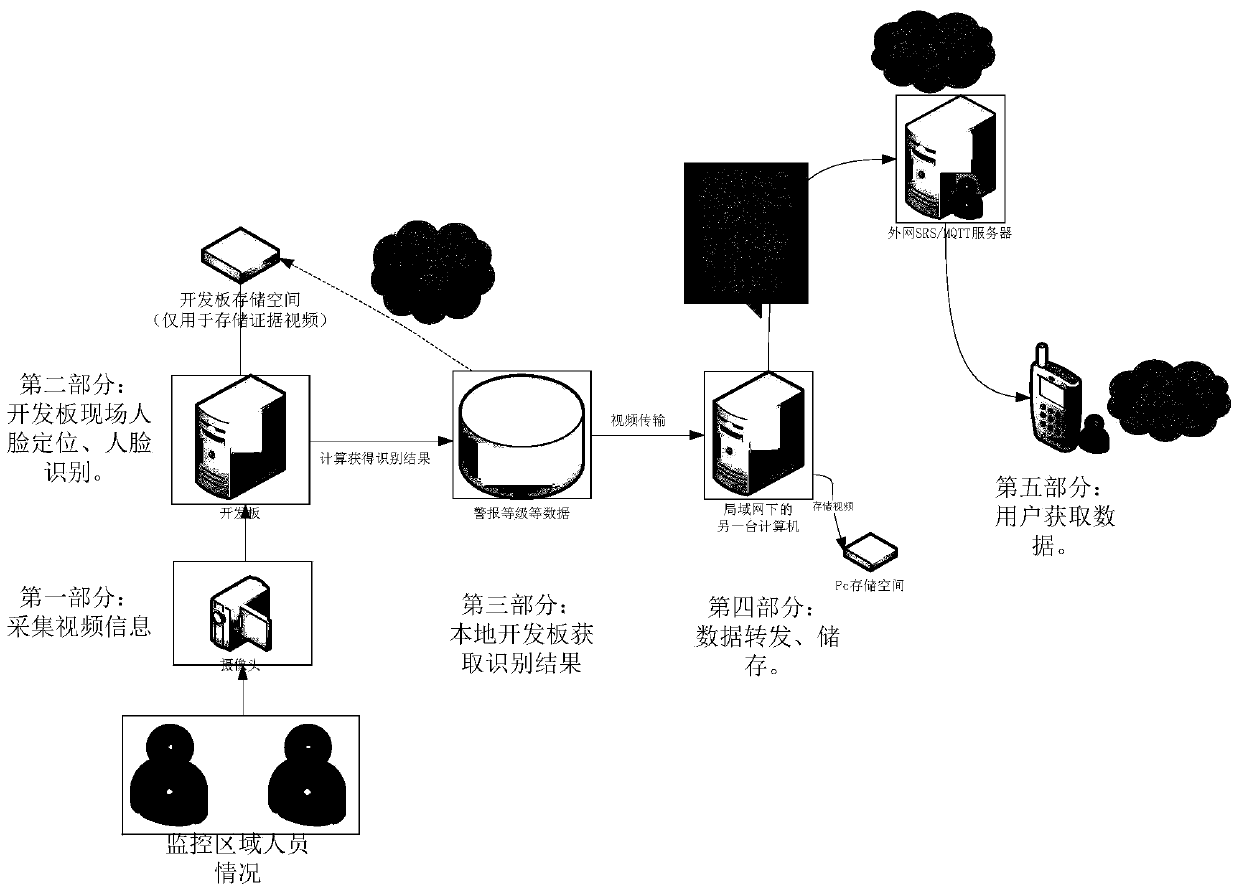
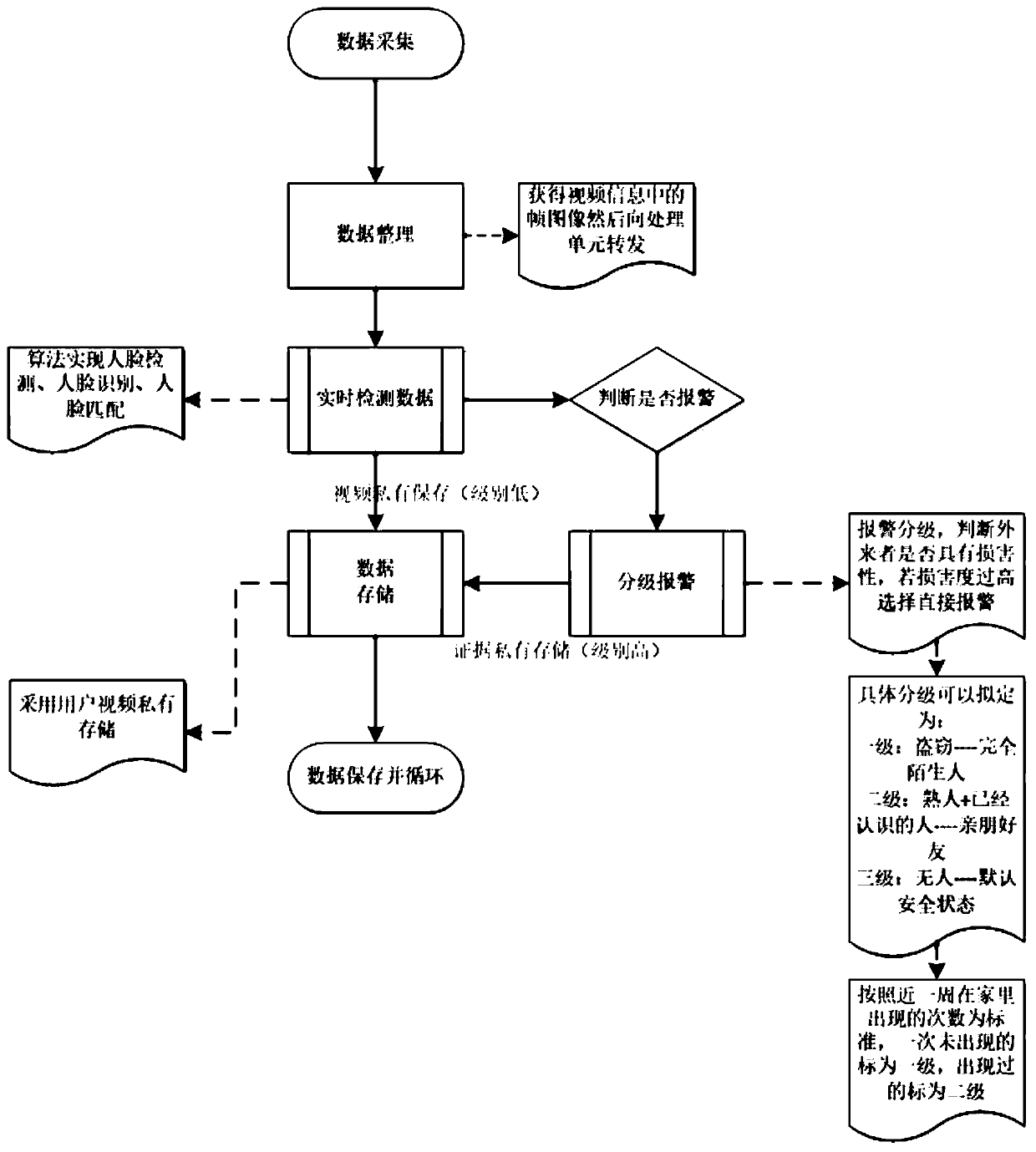
[0110] opencv library: an image processing module open sourced by the computer, used to obtain camera data. TCP / IP protocol: network communication protocol, Internet communication infrastructure. Deep Learning: Using computer artificial neural networks to extract features from input data, in order to achieve the machine's ability to learn similarly to the human brain.
[0111] Matrix convolution operation: the underlying calculation method of artificial neural network in computer deep learning, which exists in CNN neural network. Face recognition model: a black box used for face recognition calculations. The model is actually a set of very complicated mathematical formulas, which are only learned by computers. After the image is calculated through the mathematical formulas, another set of data is obtained. This Group data can be used as the basis for classification. RTMP protocol: Real Time Messaging Protocol (Real Time Message Transmission Protocol) is a streaming media tra...
Embodiment 2
[0113] The following are five sets of test results of the face recognition accuracy of embedded smart chips based on real surveillance videos in life. Each set contains about 1,000 frames of data, and each set is first recognized by a machine and then manually Identify the results of judgments. In the table below, the first column represents the label of any person that will appear in life (here is only the person who appears in the experiment, with the initials of the name as the label); the second column indicates whether the smart chip can recognize this person (know This person); the third column is the number of times the person actually appears in this set of frame data; the fourth column indicates the number of times the person is actually detected by the recognition algorithm, and the fifth column is the recognition accuracy rate of the corresponding label. Because there must be frames with no faces in each set of frame data, the frames without faces are represented by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com