Data encryption transmission method, terminal equipment and use method of superlattice chaotic device
A transmission method and data encryption technology, applied in the field of information security, can solve problems such as large amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
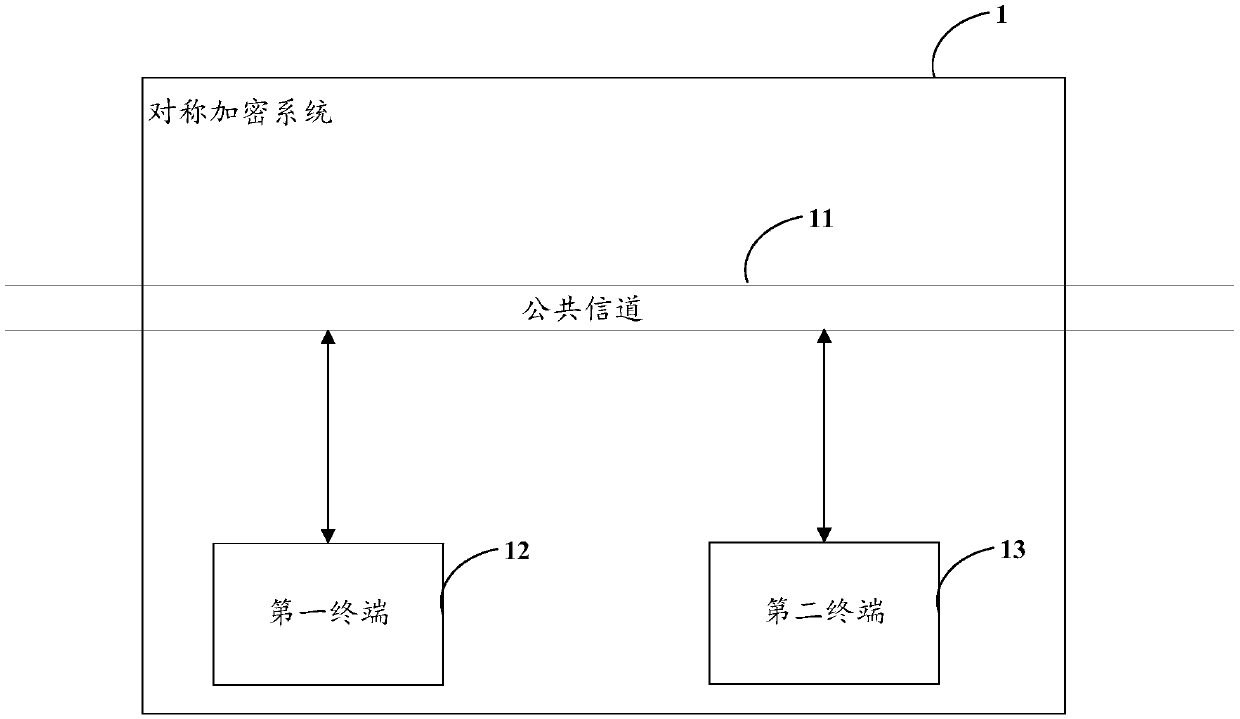
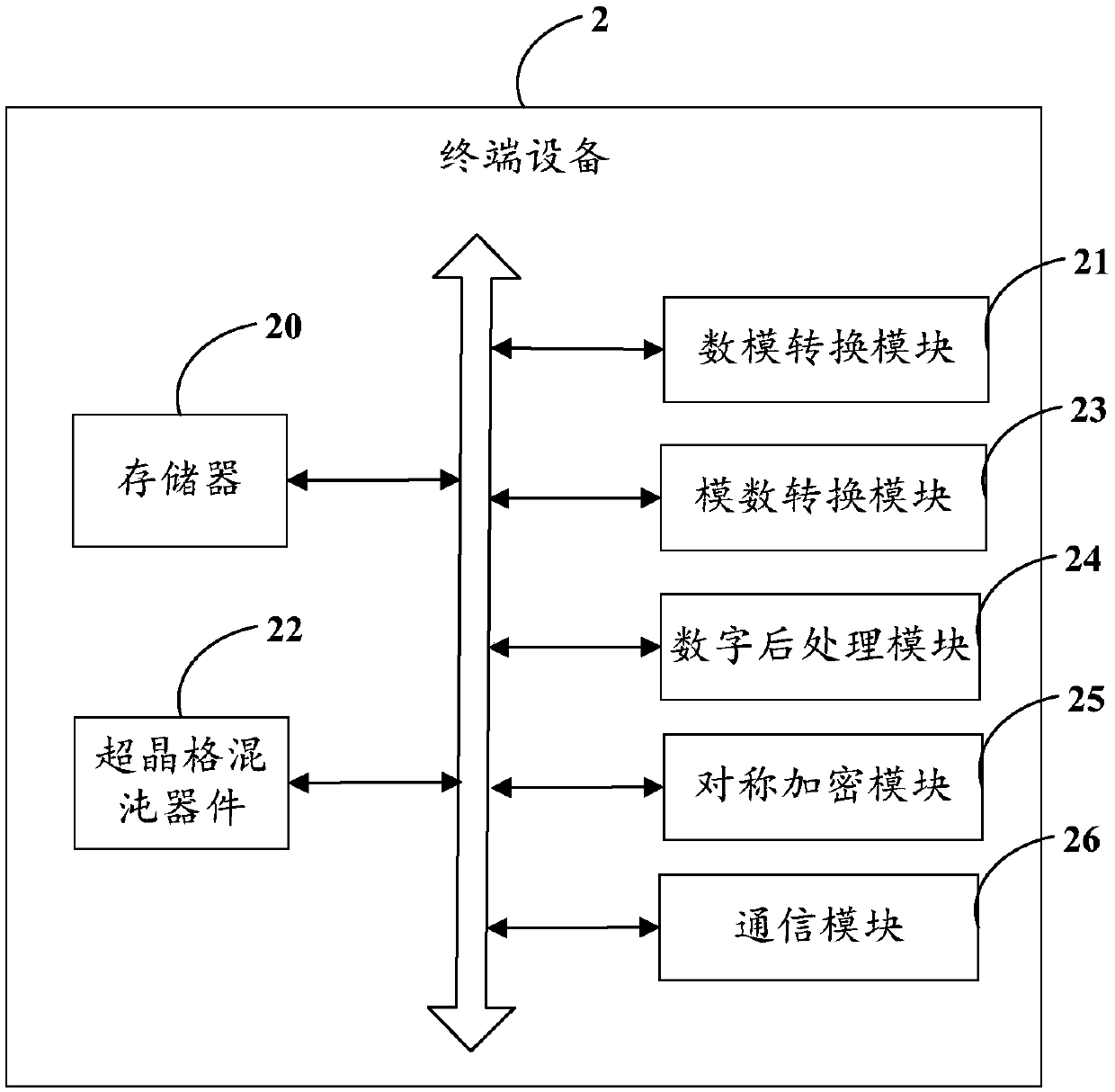
[0054] refer to figure 2 As shown, the first embodiment of the present invention proposes a terminal device 2 . It can be understood that the terminal device 2 may be the first terminal 12 or the second terminal 13 described above. The terminal device 2 includes a memory 20 , a digital-to-analog conversion module 21 , a superlattice chaotic device 22 , an analog-to-digital conversion module 23 , a digital post-processing module 24 , a symmetric encryption module 25 , and a communication module 26 .
[0055] Wherein, the memory 20 includes at least one type of readable and writable storage medium for storing local noise sources, and other data and programs required for the normal operation of the terminal. In addition, the memory 20 can also be used to temporarily store various types of data that have been output or will be output.
[0056] The digital-to-analog conversion module 21 is used to convert the local noise source stored in digital form into an analog form noise si...
Embodiment 2
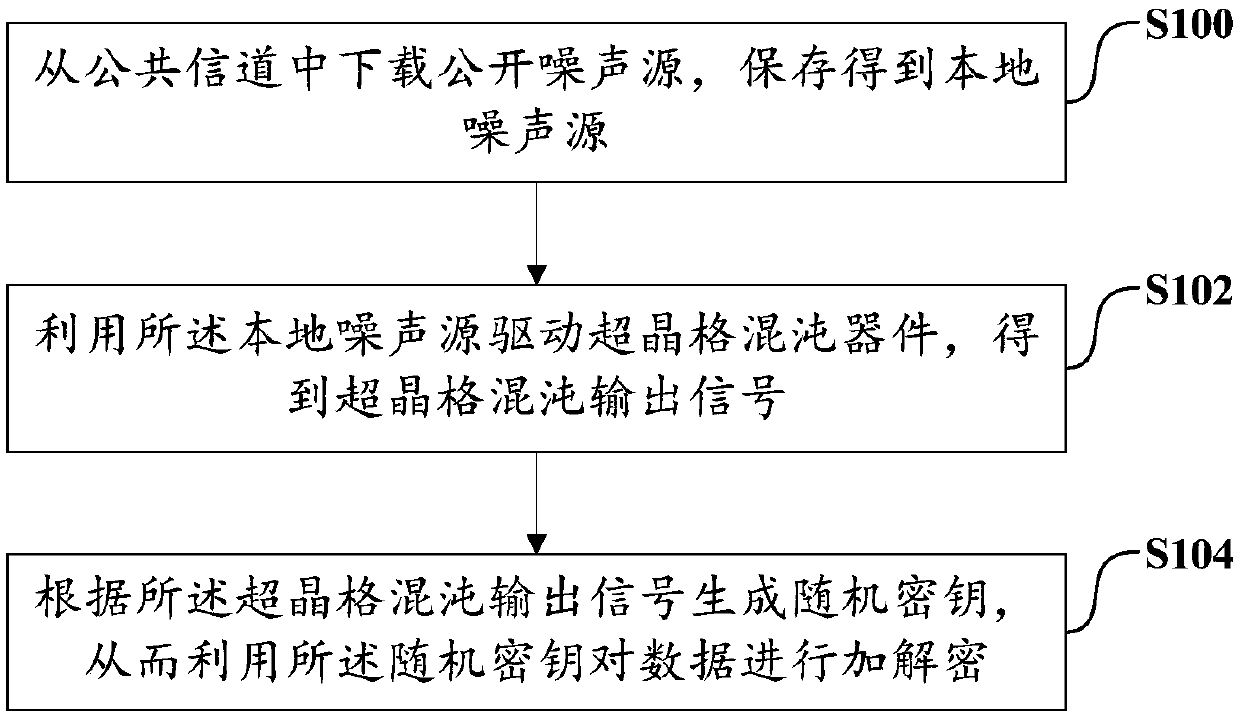
[0068] refer to image 3 As shown, the second embodiment of the present invention proposes a data encryption transmission method, which is applied to the terminal device 2 . It can be understood that the terminal device 2 may be the first terminal 12 or the second terminal 13 described above. In this embodiment, according to different requirements, image 3 The order of execution of the steps in the flowcharts shown may be changed, and certain steps may be omitted. The method includes the following steps:
[0069] S100. Download the public noise source from the public channel 11, and save the obtained local noise source.
[0070] Specifically, in order to ensure that the key generated by the first terminal 12 and the second terminal 13 is the same, so that there is no need to transfer the key between the sender and the receiver, it is necessary to ensure that the first terminal 12 and the second terminal The values of the local noise sources LNSA and LNSB used by the two...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com