A message security processing system and method
A security processing and message processing technology, applied in the field of network communication, can solve problems such as occupying CPU operating resources, interface bandwidth, security feature processing performance limitations, and enterprise losses.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
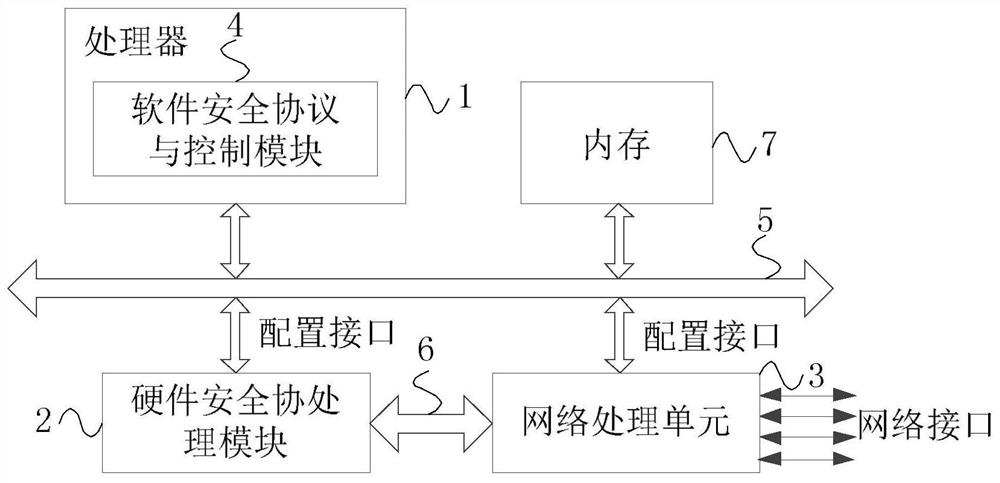
[0021] figure 1 It is a schematic structural diagram of a message security processing system in Embodiment 1 of the present invention. The technical solution of this embodiment is applicable to the case of message security processing through a hardware security co-processing module and a network processing module. The message security processing The system includes a processor 1 , a hardware security co-processing module 2 and a network processing module 3 , and the processor 1 is integrated with a software security protocol and a control module 4 .
[0022] The processor 1 is connected to the hardware security co-processing module 2 and the network processing module 3 respectively through a control management bus 5; the hardware security co-processing module 2 and the network processing module 3 are connected to each other through a message processing bus 6 connected.
[0023] In this embodiment, the processor 1 is respectively connected to the hardware security co-processin...
Embodiment 2
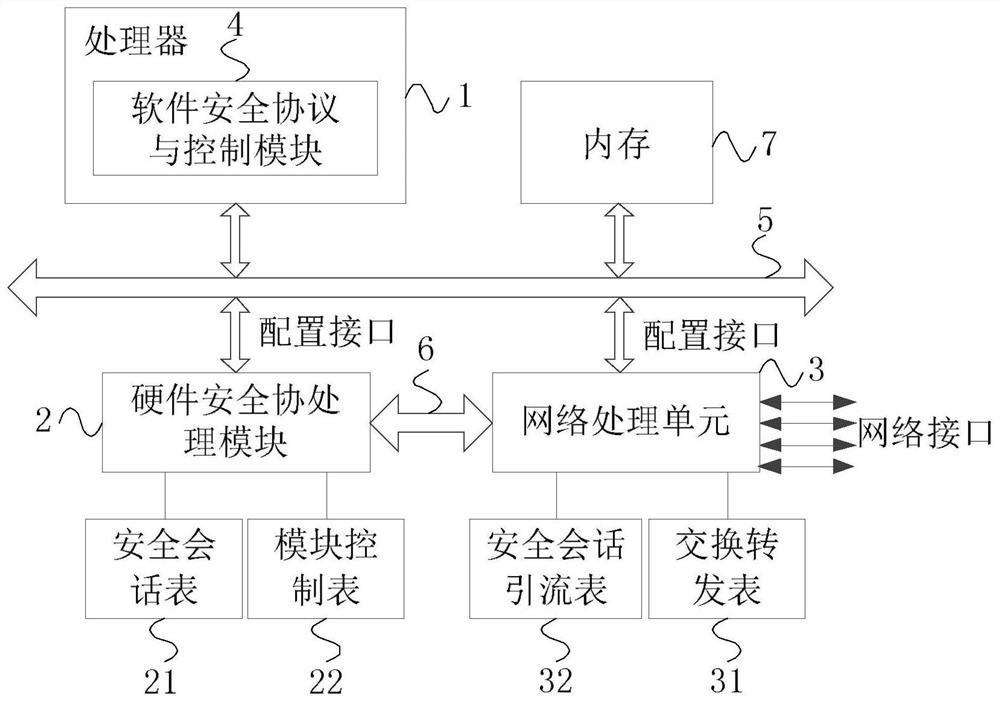
[0039] figure 2 A schematic structural diagram of a message security processing system provided by Embodiment 2 of the present invention. This embodiment is further refined on the basis of the above embodiments, providing a processor 1, a hardware security co-processing module 2 and a network processing module 3 specific functions. Combine below figure 2 A message security processing system provided in Embodiment 2 of the present invention is described:
[0040] The message security processing system includes: a processor 1 , a hardware security co-processing module 2 and a network processing module 3 , and the processor 1 is integrated with a software security protocol and a control module 4 .
[0041] The processor 1 is connected to the hardware security co-processing module 2 and the network processing module 3 respectively through a control management bus 5; the hardware security co-processing module 2 and the network processing module 3 are connected to each other throu...
Embodiment 3
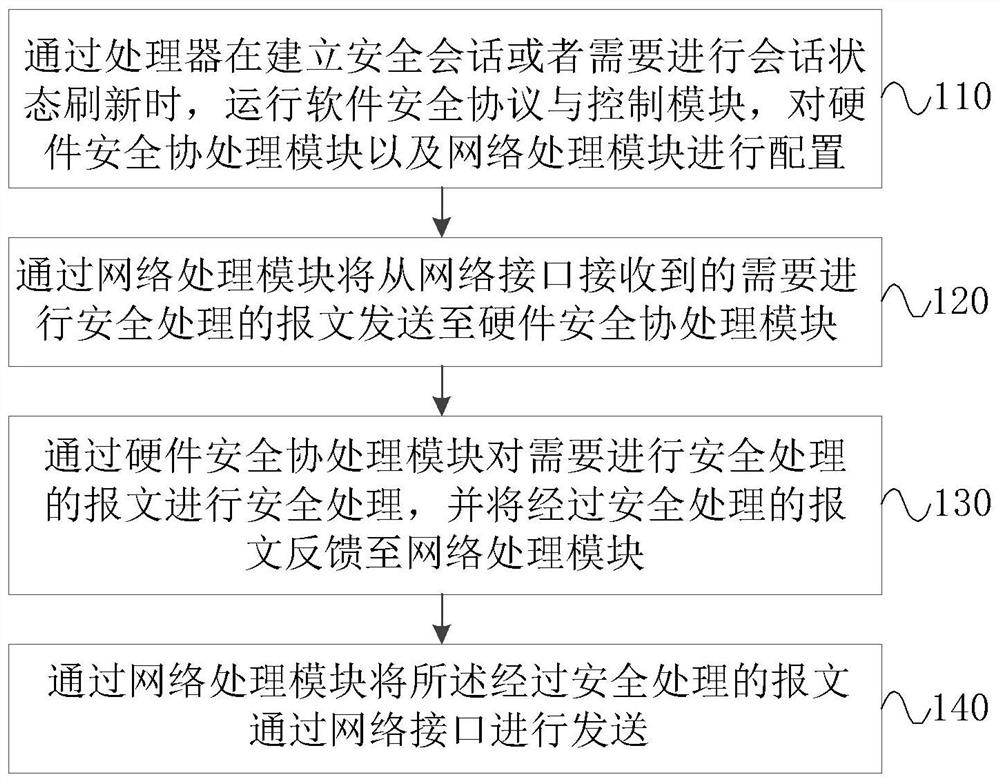
[0072] image 3 It is a flow chart of a message security processing method in Embodiment 3 of the present invention. The technical solution of this embodiment is applicable to the case of message security processing through a hardware security co-processing module and a network processing module. The execution of the document security processing system specifically includes the following steps:
[0073] Step 110, when the processor establishes a secure session or refreshes the session state, the processor runs the software security protocol and the control module, and configures the hardware security co-processing module and the network processing module.
[0074] Wherein, configuring the hardware security co-processing module and the network processing module includes configuring the security session table and the module control table in the hardware security co-processing module, and configuring the switching and forwarding table and the security session diversion table in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com