Vehicle control system network security detection method based on multi-stage feedback queue
A vehicle control system and network security technology, applied in the field of vehicle control system network security detection based on multi-level feedback queue, can solve the problem of poor autonomous controllability, lack of security encryption, security authentication and boundary protection mechanism, vehicle control network damage, etc. problems, to achieve rapid screening, efficient automatic security event injection detection mechanism, and improve the degree of automation and matching.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
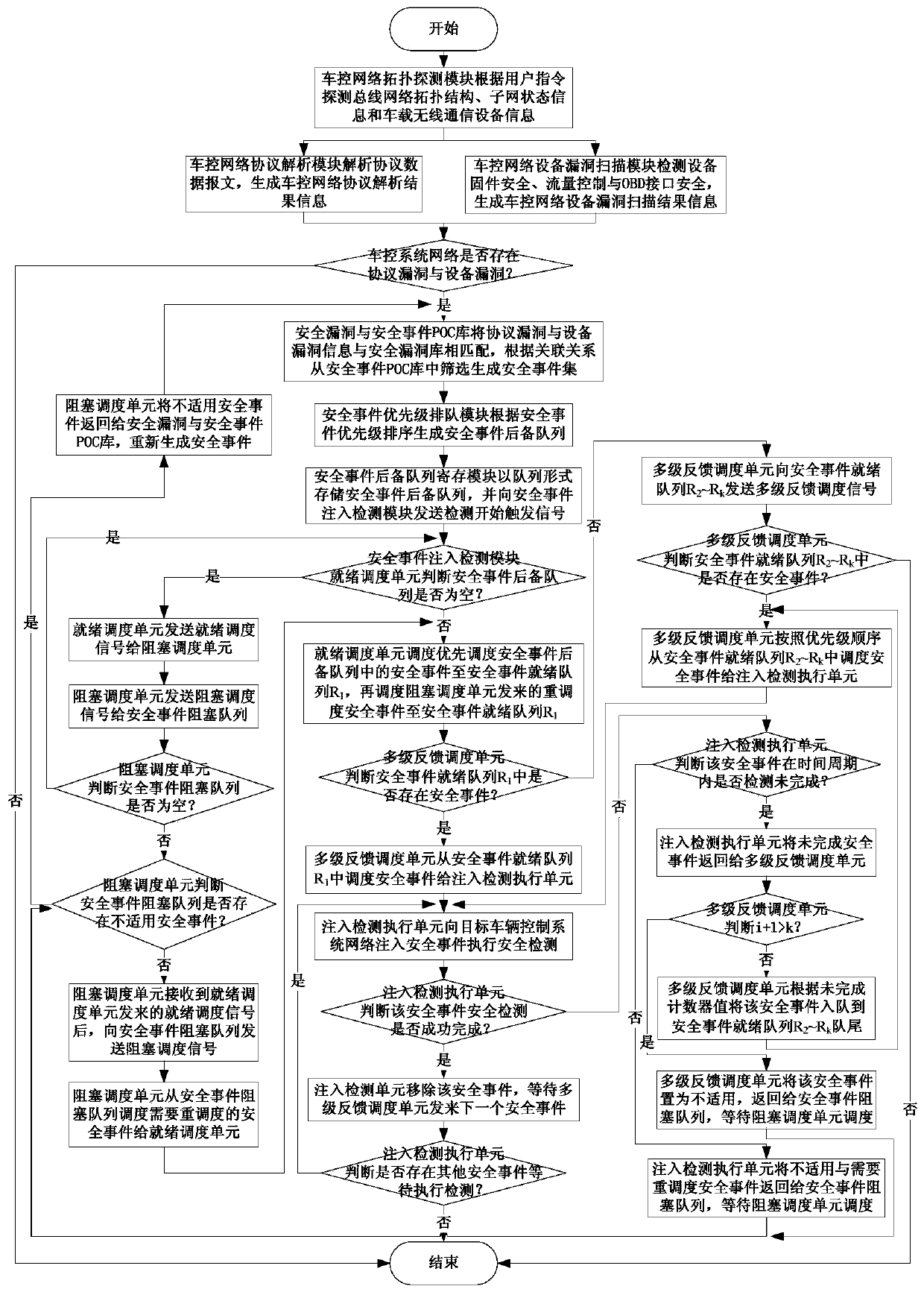
[0102] This embodiment adopts a vehicle control system network security detection method based on a multi-level feedback queue, which achieves a higher degree of automation, a more reasonable, efficient, and accurate security event injection detection mechanism, and a detection scenario that is more in line with real attack behaviors. More autonomous and controllable vehicle control system network security testing in the whole testing process.
[0103] The method for detecting the network security of the vehicle control system using the method of the present invention will be described in detail below in conjunction with specific embodiments. Therefore, it can be extended to a wider range of network security detection applications for vehicle control systems of various types of ordinary vehicles, special vehicles, and self-driving vehicles.
[0104] First build the target vehicle control system network. The target vehicle control system network uses the vehicle CAN and LIN bus...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com