Gene data desensitization method for realizing efficient similarity query and access control
A genetic data and access control technology, applied in the field of information security, can solve the problems of reducing data availability, focusing only, different access rights of genetic data, etc., to achieve the effect of reducing the number of elements, flexible authorization methods, and improving query and retrieval efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
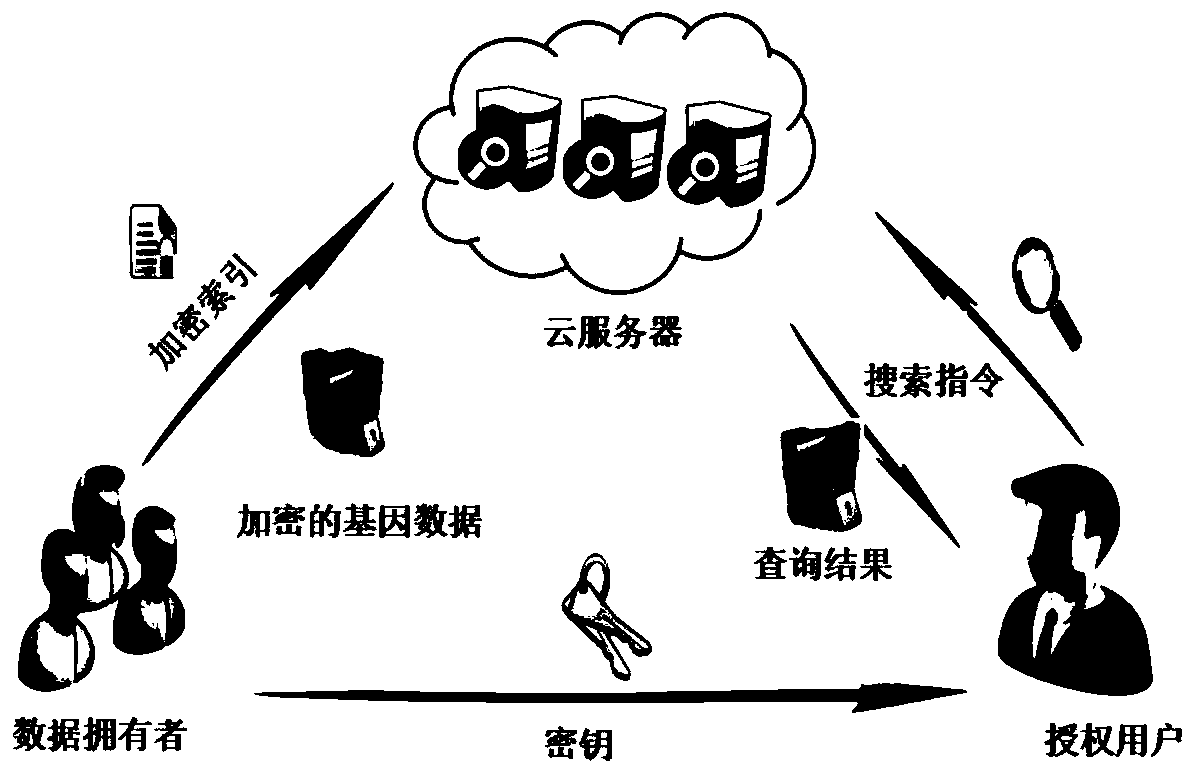
[0063] This embodiment proposes a genetic data desensitization method that realizes efficient ciphertext similarity query and secure access control in a cloud environment. The process is as follows figure 1 As shown, it specifically includes the following steps:
[0064] Step 1. System initialization: the system generates a public gene sequence, the data owner generates a set of role permissions for users to access data, and generates the keys required for specific hash function encryption, set pseudo-random permutation, and matrix security inner product operations;
[0065] System initialization, specifically includes the following steps:
[0066] Step 1.1 The system releases the public gene sequence ref that does not contain any sensitive information, and ref is the target sequence required for processing by the edit distance algorithm;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com