Quantum communication service station digital signcryption method and system based on asymmetric key pool
A technology of quantum communication and service station, which is applied in the field of digital signcryption system of quantum communication service station, which can solve the problems of huge key capacity of symmetric key pool, pressure of key storage, inability to store key cards, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0138] Assume that there are two quantum communication service stations QA and QB, client A (signcryption party) belonging to QA and client B (cryptographic verification party) belonging to QB. The ID of A contains the ID of QA, and the ID of A is denoted as IDA; the ID of B contains the ID of QB, and the ID of B is denoted as IDB, indicating the affiliation.
[0139] 1. A has file F, generate signcryption file
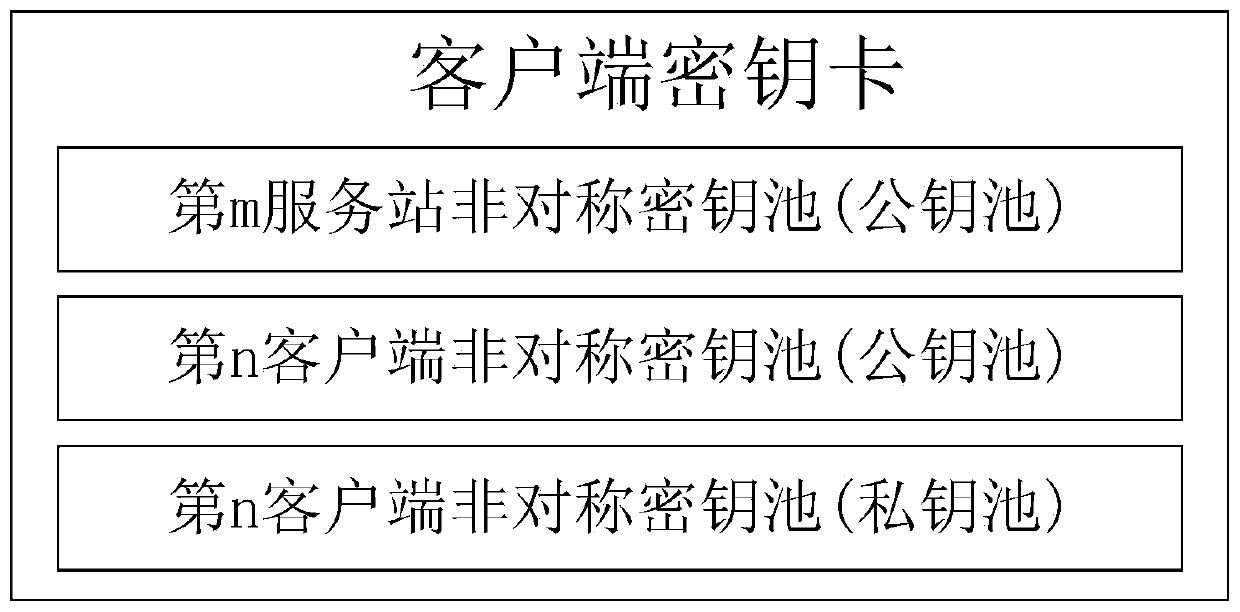
[0140] 1.1. A takes the random number ria, and uses the function FA (for example, splits a number into three segments according to the length of 2:3:5) to act on ria to obtain three numbers ria1, ria2 and ria3, and then use ria1 to encrypt from the client Take kia1 / Kia1 from the client asymmetric key pool (private key pool / public key pool) of the key card, and use ria2 to take Kia2 from the asymmetric key pool (public key pool) of the service station of the client key card. Among them, the parameters "kia1", "Kia1", "Kia2", etc. represent the value of the corresponding po...
Embodiment 2
[0175] Assuming that there is a quantum communication service station Q, both client A (signcryption party) and client B (cryptography party) belong to Q. The ID of A is IDA, and the ID of B is IDB.
[0176] 1. A has file F, generate signcryption file
[0177] 1.1. A takes the random number ria, and uses the function FA (for example, splits a number into three segments according to the length of 2:3:5) to act on ria to obtain three numbers ria1, ria2 and ria3, and then use ria1 to encrypt from the client Take kia1 / Kia1 from the client asymmetric key pool (private key pool / public key pool) of the key card, and use ria2 to take Kia2 from the asymmetric key pool (public key pool) of the service station of the client key card.
[0178] Let xa=ria3, according to the formula ka=Kia2 xa mod p calculates the value of ka, and then uses the function fa1 (for example, splitting a number into two segments according to a length of 1:1) to apply to ka to obtain two numbers: the first intermediat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com