A complete avalanche 4*4 S box implementation method
An implementation method and complete technology, applied in the field of information security, can solve the problems of simple S-box algebraic expressions and not satisfying the complete avalanche criterion, and achieve the effects of improving security, good avalanche effect, and resisting linear attacks and algebraic attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
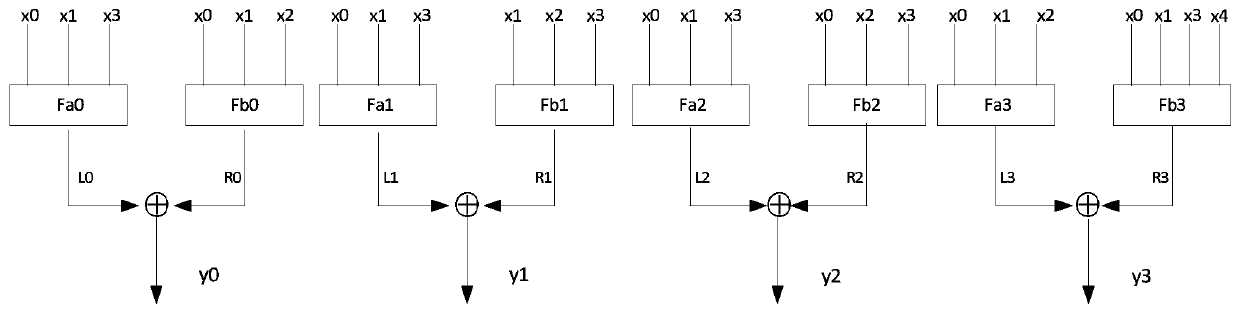
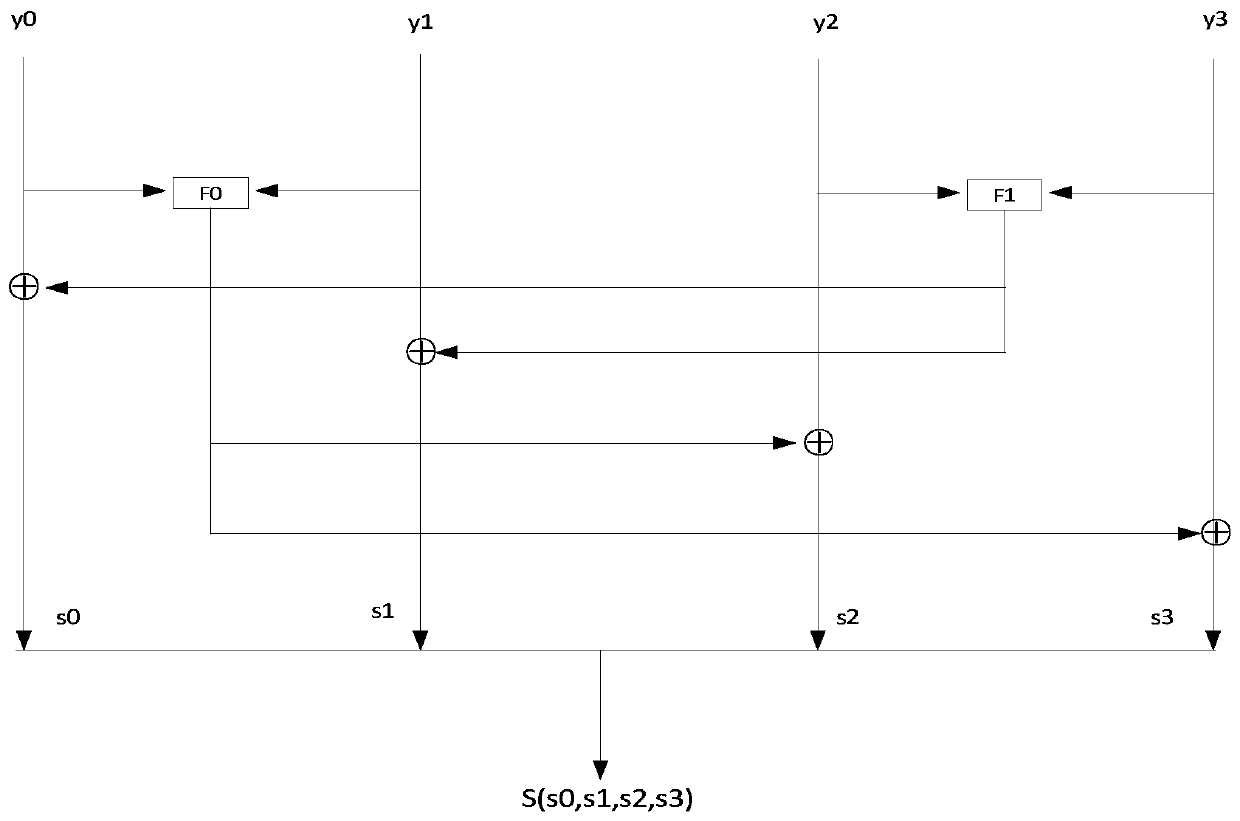
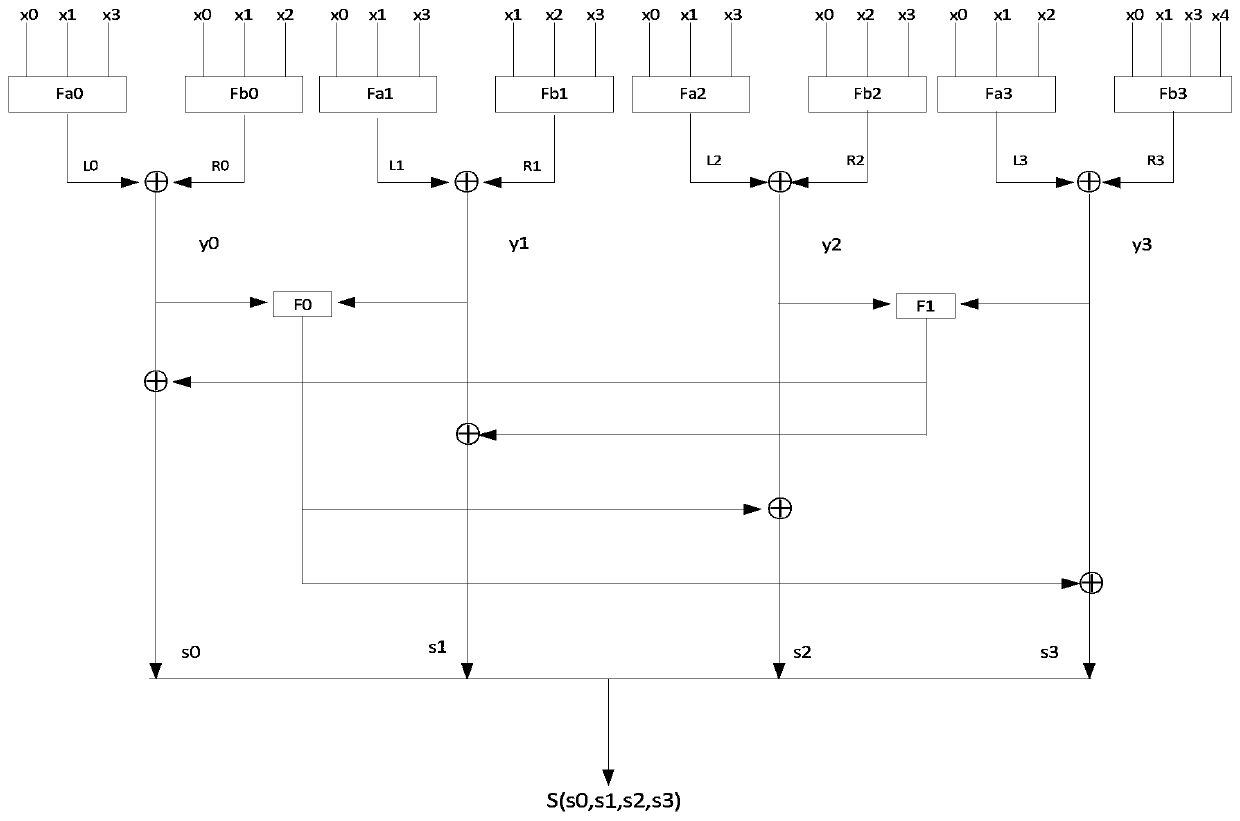
[0052] A method and device for implementing a complete avalanche 4×4 S-box of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0053] The actual operation of the S box is a mapping table. For a 4×4 S box, the input is an integer from 0 to 15, and the output is an integer from 0 to 15. The input information of the S box is only 4 bits each time. For example, if you input a 0, use The 4-bit binary number representation is 0000. Then 0000 is represented by (x0, x1, x2, x3), that is, x0, x1, x2, and x3 represent a 0 respectively. .
[0054] Suppose a number a (a∈[0,15]) is input, its binary numbers are x0, x1, x2, x3, and x0, x1, x2, x3 are set according to figure 1 Enter the nonlinear layer.
[0055] The output of the nonlinear layer is obtained as y0, y1, y2, y3.
[0056] a input nonlinear layer operation, the corresponding output is:
[0057] a(0)=0, a(1)=8, a(2)=F, a(3)=3, a(4)=2, a(5)=5, a(6)=C, a (7)=A, a(...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com