Intrusion detection method, apparatus and system, device and storage medium
A technology for intrusion detection and storage media, applied in transmission systems, electrical components, etc., can solve problems affecting server business operation, increasing CPU, affecting performance, etc., to achieve the effect of improving intrusion detection performance and avoiding CPU consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] An embodiment of the present invention provides an intrusion detection method, such as figure 1 As shown, the method includes:
[0044] S101, monitoring system call information through a configured audit module for monitoring various system calls;
[0045] S102. Perform intrusion detection on the monitored system call information according to the pre-received detection rule.
[0046] The method in the embodiment of the present invention executes the host on the host that needs to be detected. The Linux (an operating system) kernel provides an audit mechanism. The function of the audit module is to monitor various system calls, and when a system call occurs, record the relevant information of the call. The detection rules can be received from the server, and the detection rules include related attributes such as rule identification (id), name, description information, rule type (black and white list), severity level and rule expression. Wherein, the description inform...
Embodiment 2
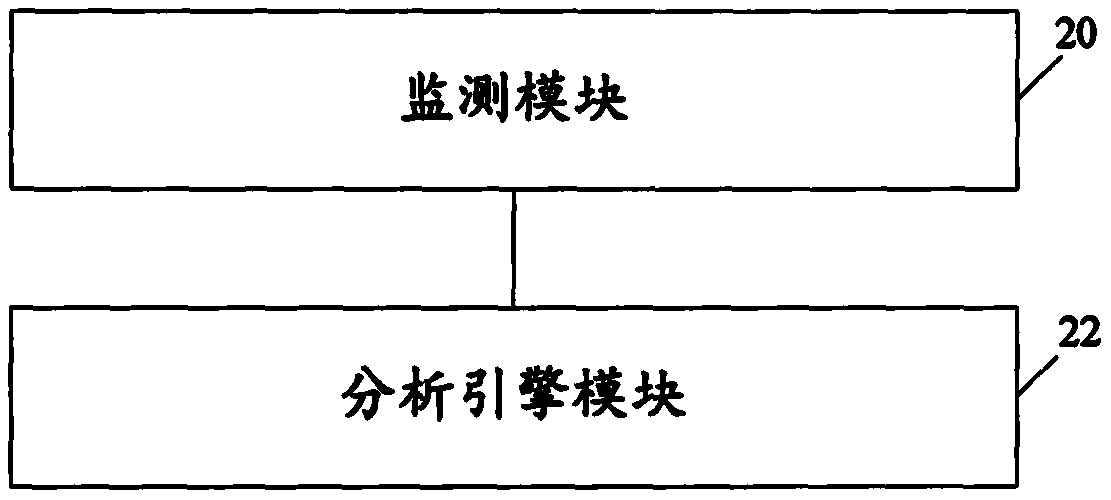
[0074] Corresponding to the method in Embodiment 1, the embodiment of the present invention provides a corresponding intrusion detection device, such as figure 2 As shown, the device includes:
[0075] A monitoring module 20, configured to monitor system call information through an audit module configured to monitor various system calls;
[0076] The analysis engine module 22 is configured to receive the system call information monitored by the detection module, and perform intrusion detection on the monitored system call information according to the pre-received detection rules.
[0077] In some embodiments, the device also includes:
[0078]A configuration module, configured to configure monitoring information of the audit module; the monitoring information is used to indicate system calls monitored by the audit module.
[0079] In some implementations, the monitoring module 20 is specifically configured to process the monitored system call information into formatted syst...
Embodiment 3
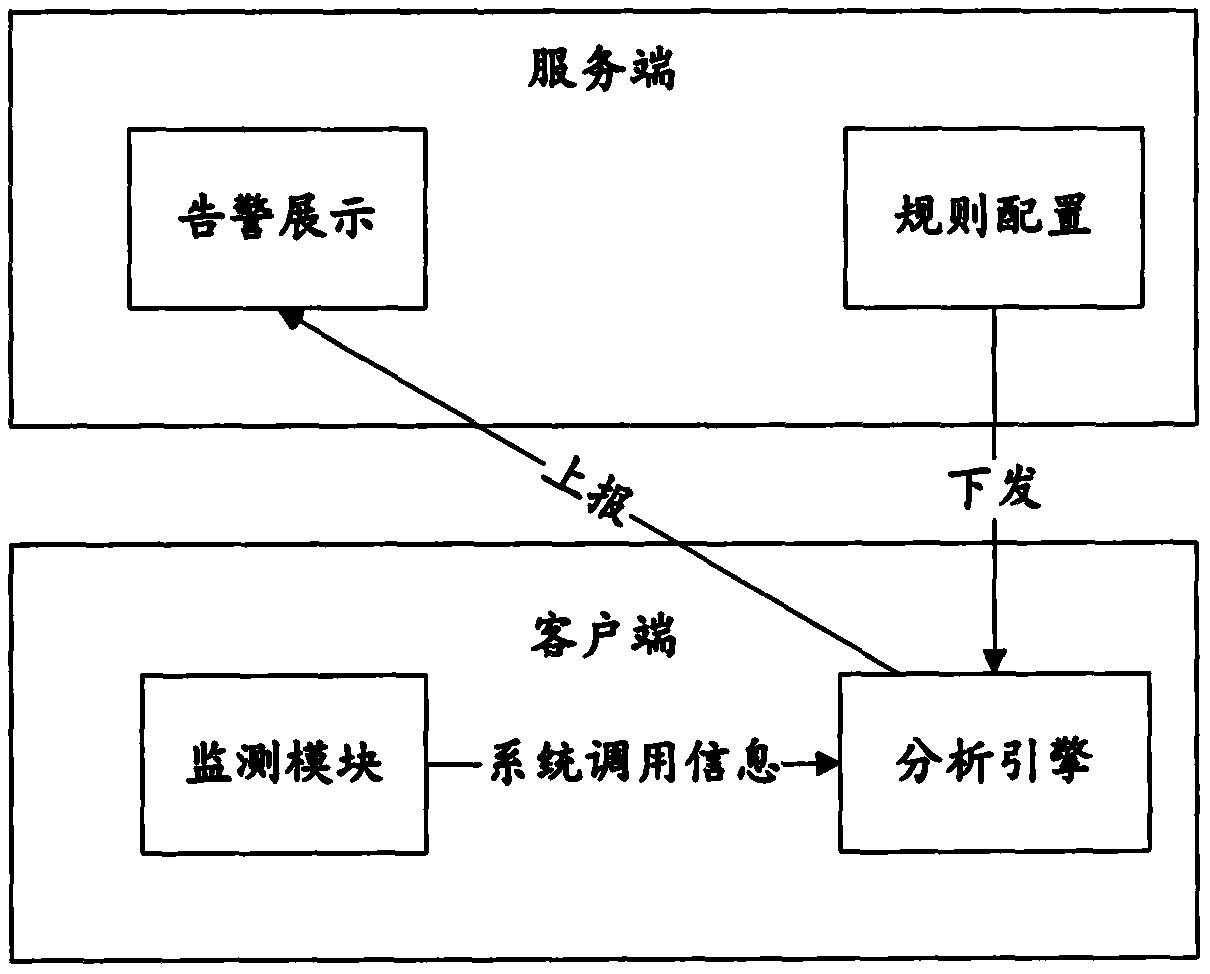
[0084] An embodiment of the present invention provides an intrusion detection system, such as image 3 As shown, the system includes a host and a server device; the host includes the intrusion detection device according to any one of Embodiment 2; the server device is configured to send detection rules to the host.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com