Network intrusion classification method based on Bayes of total indirected graph
A Bayesian classifier and network intrusion technology, which is applied in data exchange networks, special data processing applications, instruments, etc., can solve problems such as inability to apply real-time, failure to consider attribute independence, relationship dependency, and high event complexity , to achieve the effect of improving intrusion detection performance, simple calculation, and reducing false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
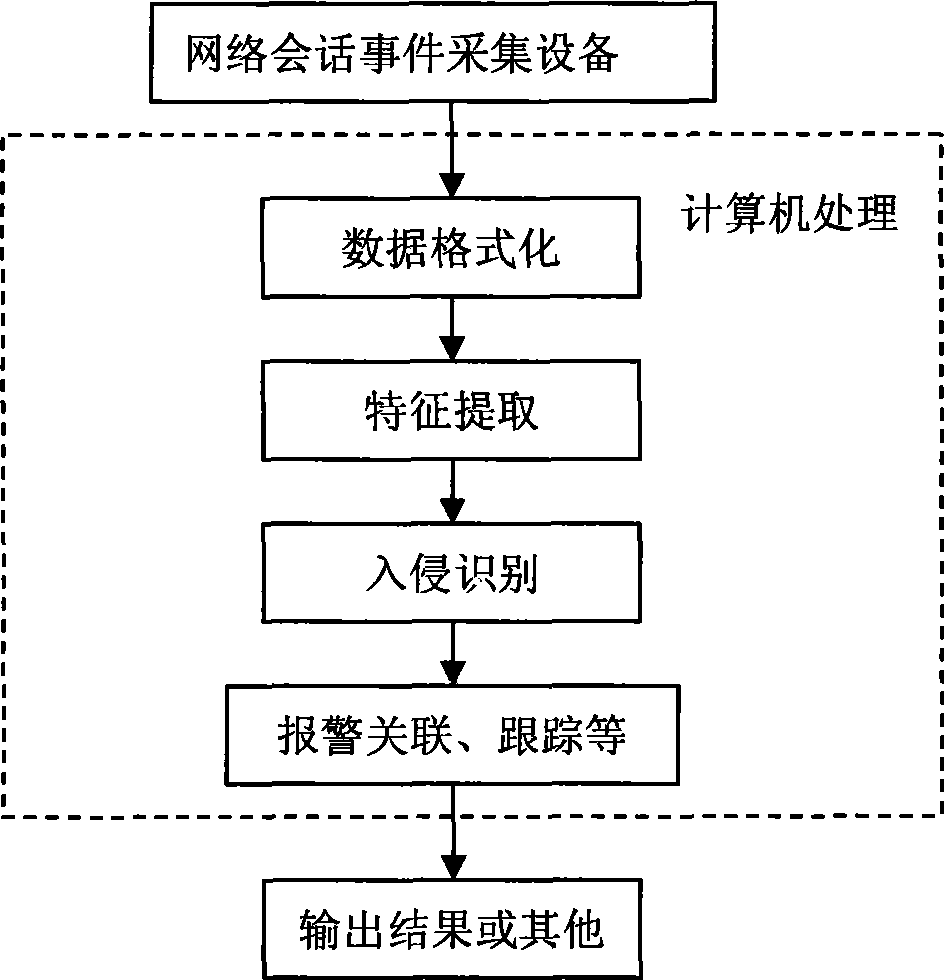
[0045] Such as figure 1 As shown, the intrusion detection system obtains network message data through the network session event collection device, and performs preprocessing such as message data formatting and feature extraction, and then performs intrusion identification. deal with.
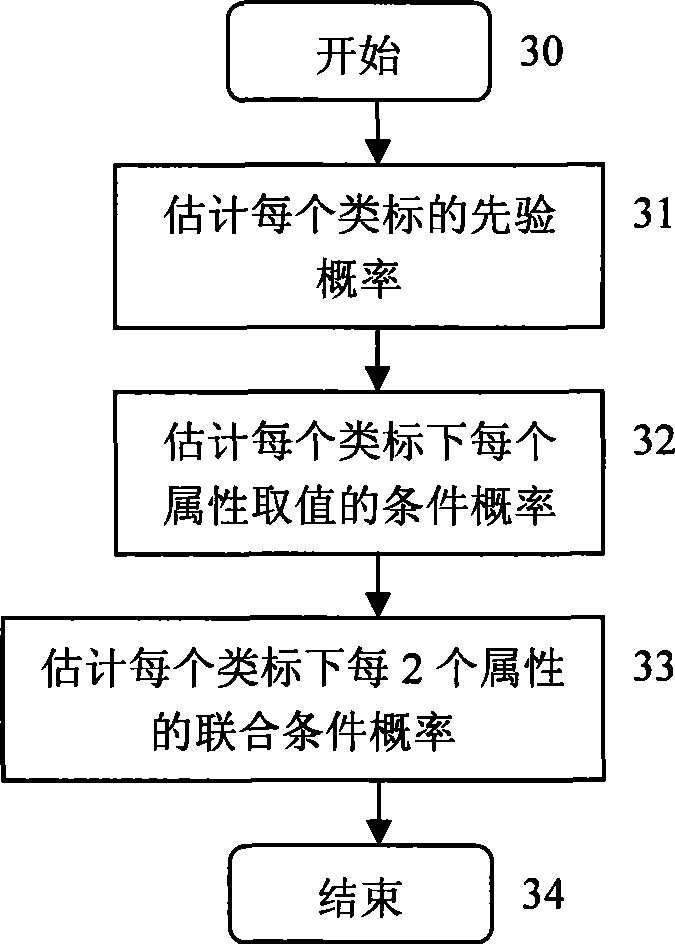
[0046] Intrusion identification is the core step of the network intrusion detection system, and the idea of the present invention is to improve the performance of the entire network intrusion detection system by improving the classification accuracy of the classifier in the intrusion identification. The intrusion recognition process is the flow chart of the Bayesian network intrusion classification method based on the completely undirected graph of the present invention. figure 2 shown.
[0047] Step 0 is the initial state of the network intrusion classification method of the present invention;
[0048] In the training phase (steps 1-3), step 1 collects historical session events known to b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com