Immune-based Internet of Things distributed intrusion detection method and system
An intrusion detection and Internet of Things technology, applied in the field of Internet of Things information security, can solve problems such as inability to adapt to the Internet of Things network environment, and achieve the effects of improving intrusion detection performance, improving Internet of Things environment capabilities, and reducing training costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] Embodiment 1: an immune-based Internet of Things distributed intrusion detection method, specifically comprising the following steps:
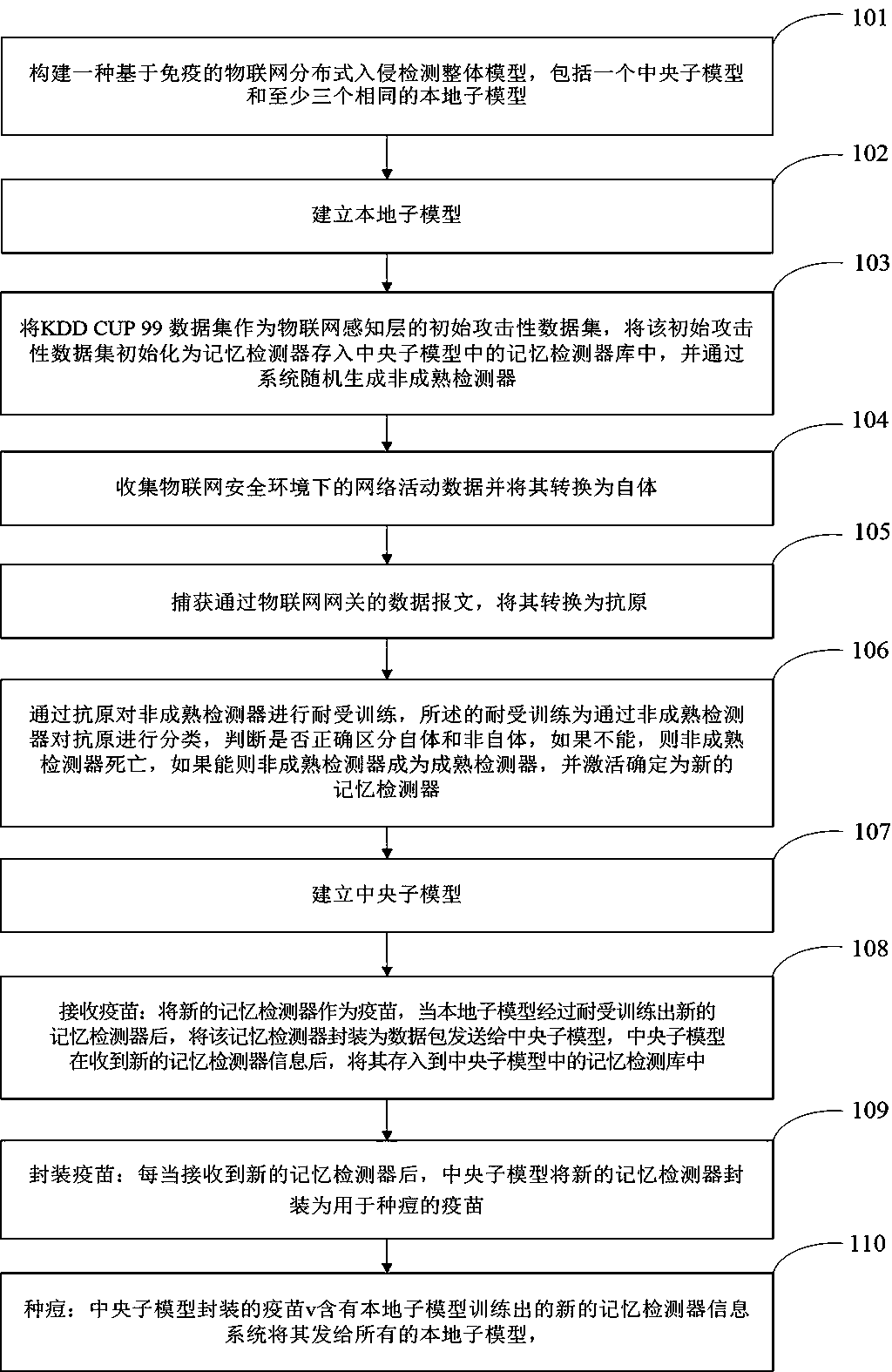
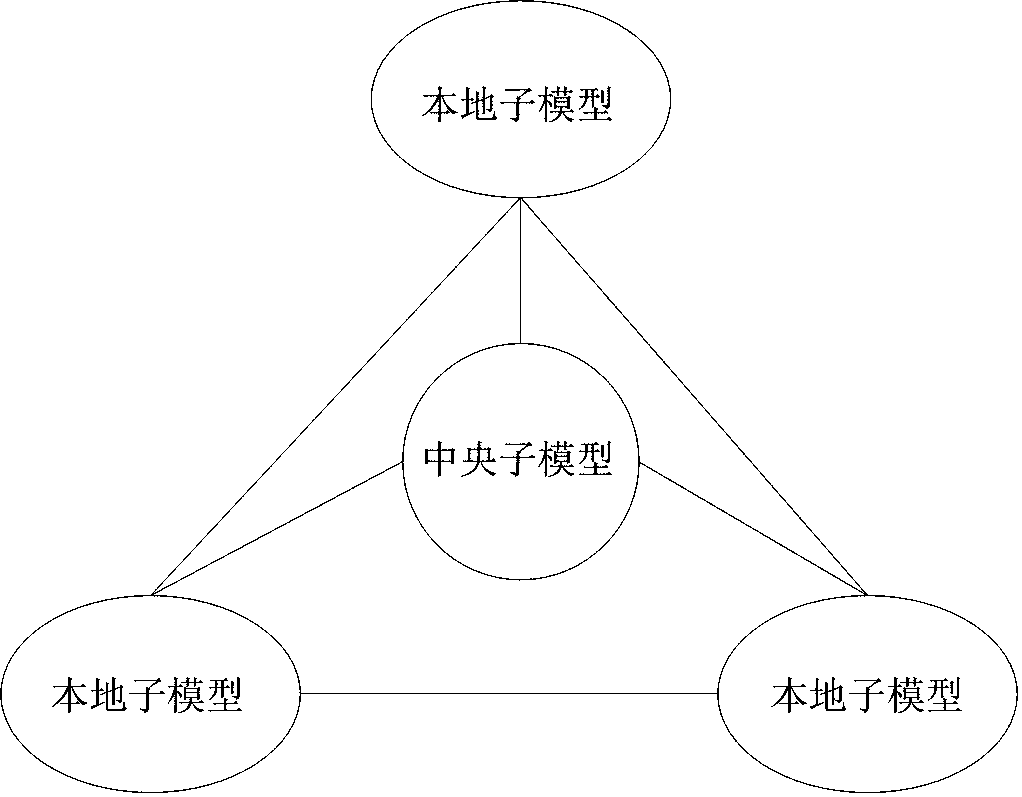
[0055] Step 101: Build an immune-based IoT distributed intrusion detection overall model, including a central sub-model and at least three identical local sub-models; the local sub-models are connected to the IoT gateway in a bypass manner, and each local sub-model The model runs independently in a distributed manner, and is managed and coordinated by the central sub-model. The local sub-model and the central sub-model together constitute the overall model of the immune-based IoT distributed intrusion detection model.
[0056] Step 102: Establish a local sub-model: the local sub-model includes a detector and an antigen, the antigen is a data feature of the perception layer data of the Internet of Things, and the antigen is divided into self and non-self, and the self is a data feature of normal data, The non-self is a data feature of th...
Embodiment 2
[0067] Embodiment 2: Another immune-based Internet of Things distributed intrusion detection method specifically includes the following steps:
[0068] Step 201: Construct an overall immune-based IoT distributed intrusion detection model, including a central sub-model and at least three identical local sub-models; the local sub-models are connected to the IoT gateway in a bypass manner, and each local sub-model The model runs independently in a distributed manner, and is managed and coordinated by the central sub-model. The local sub-model and the central sub-model together constitute the overall model of the immune-based IoT distributed intrusion detection model.
[0069] Step 202: Establish a local sub-model: the local sub-model includes a detector and an antigen, the antigen is a data feature of the perception layer data of the Internet of Things, and the antigen is divided into self and non-self, and the self is a data feature of normal data, The non-self is a data feature...
Embodiment 3
[0089] Embodiment 3: an immune-based distributed intrusion detection system for the Internet of Things, comprising:
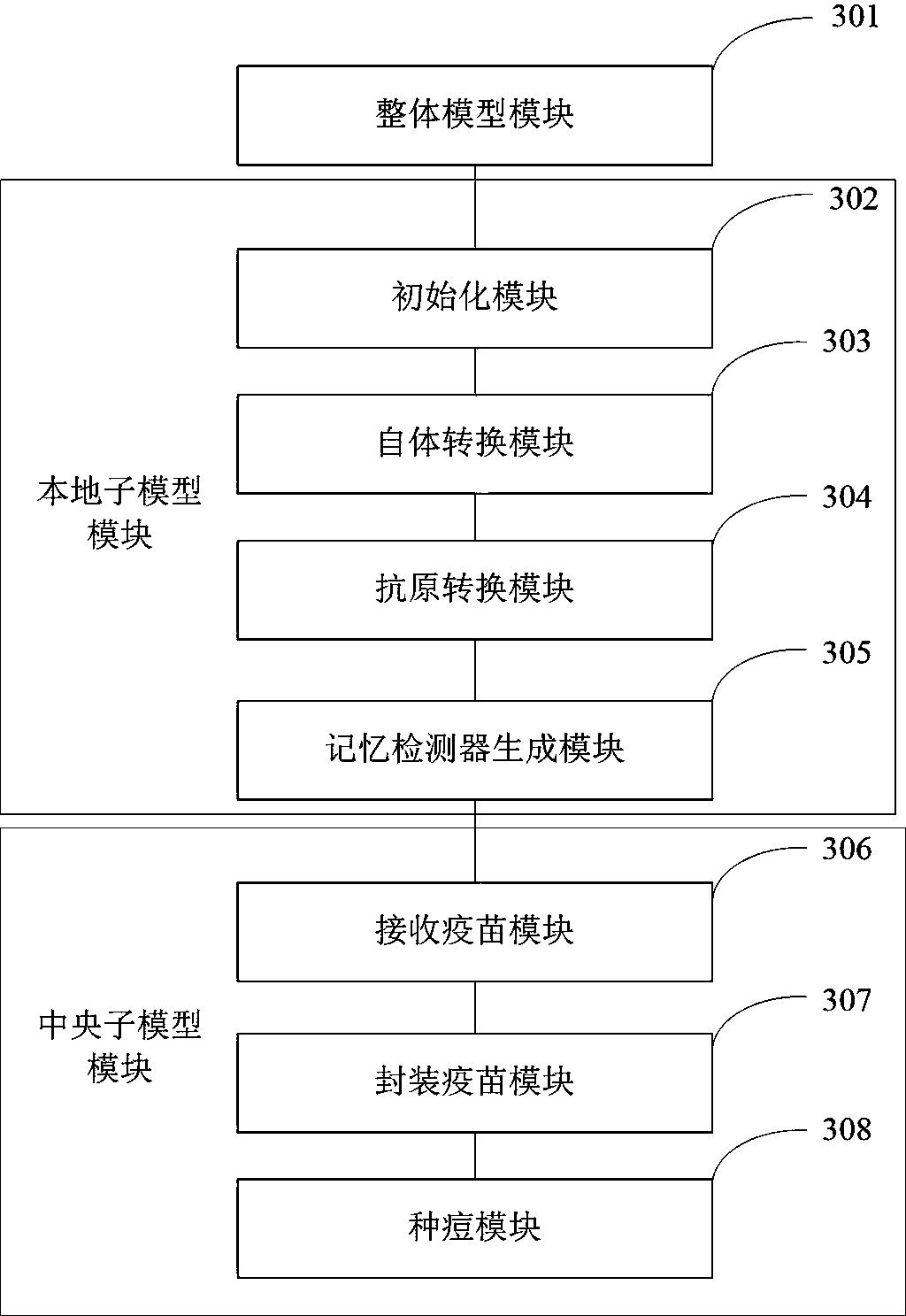
[0090] Overall model module 301, local sub-model module and central sub-model module, described local sub-model module includes initialization module 302, autologous conversion module 303, antigen conversion module 304, memory detector generation module 305; described central sub-model The modules include a vaccine receiving module 306, a vaccine packaging module 307, and a vaccination module 308; the overall model module 301 is sequentially connected to an initialization module 302, an autologous conversion module 303, an antigen conversion module 304, a memory detector generation module 305, a vaccine receiving module 306, and a vaccine packaging module. Module 307, vaccination module 308.
[0091] The overall model module 301 is used to construct an overall model of an immune-based distributed intrusion detection of the Internet of Things, including a centra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com