Conditional mutual information based network intrusion classification method of double-layer semi-idleness Bayesian
A technology of conditional mutual information and Bayesian classifiers, applied in data exchange networks, electrical components, digital transmission systems, etc. Issues such as different event attribute independence relations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be described in detail below in conjunction with the accompanying drawings.
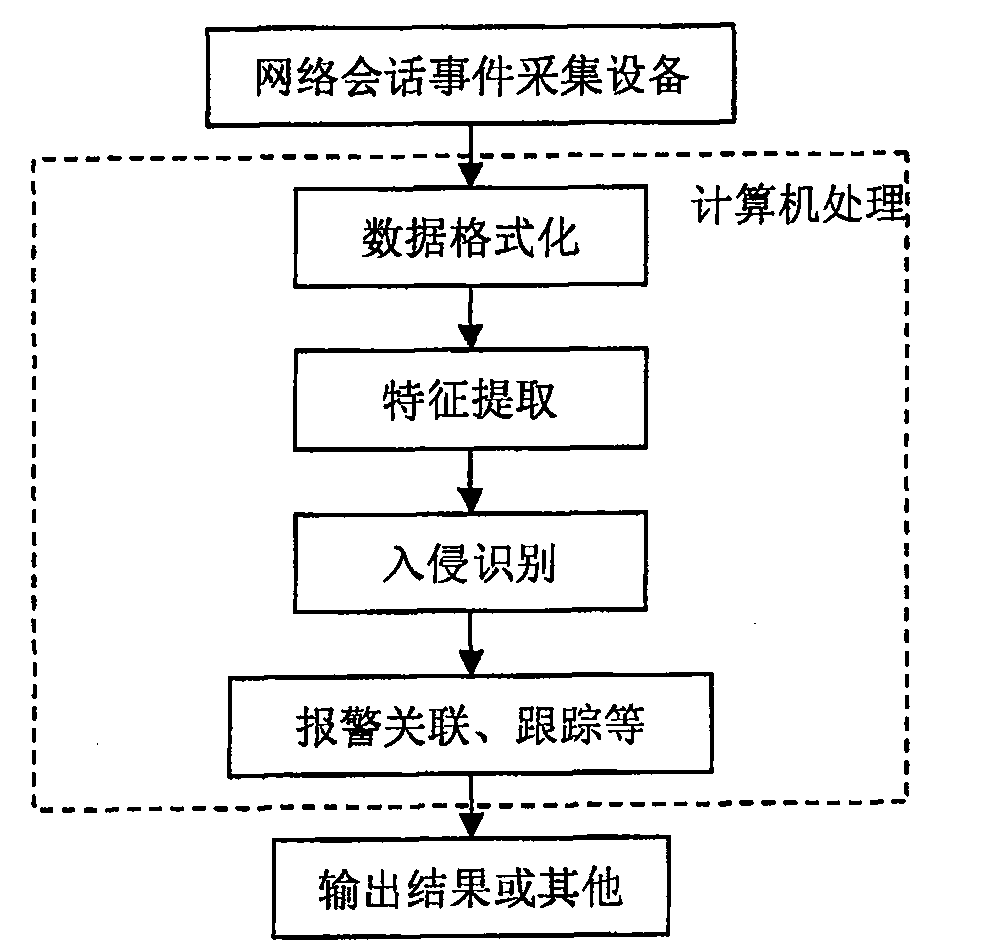
[0064] Such as figure 1 As shown, the intrusion detection system obtains network message data through the network session event collection device, and performs preprocessing such as message data formatting and feature extraction, and then performs intrusion identification. deal with.
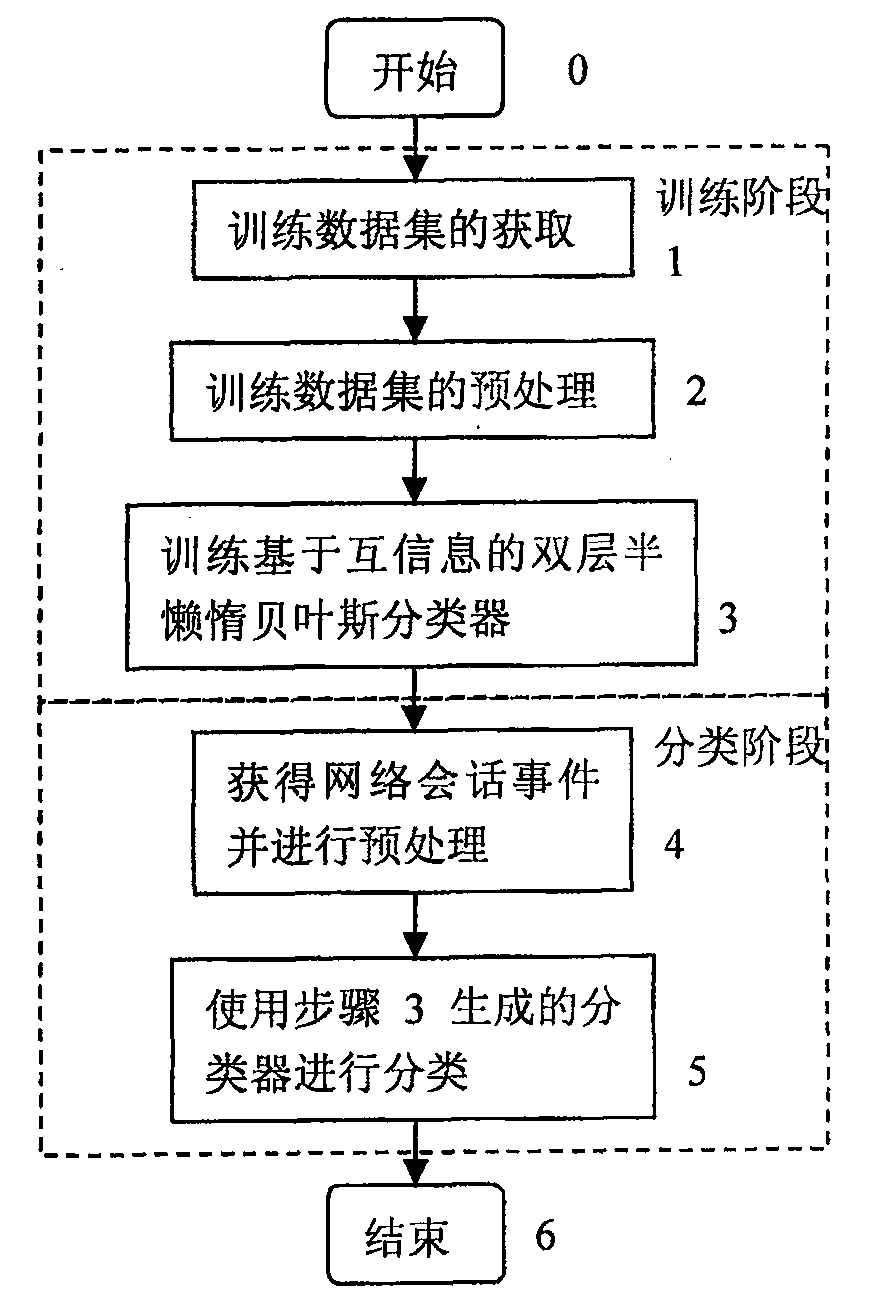
[0065] Intrusion identification is the core step of the network intrusion detection system, and the idea of the present invention is to improve the performance of the entire network intrusion detection system by improving the classification accuracy of the classifier in the intrusion identification. The flow chart of the intrusion identification process, that is, the network intrusion classification method based on the conditional mutual information of the present invention, is as follows: figure 2 shown.
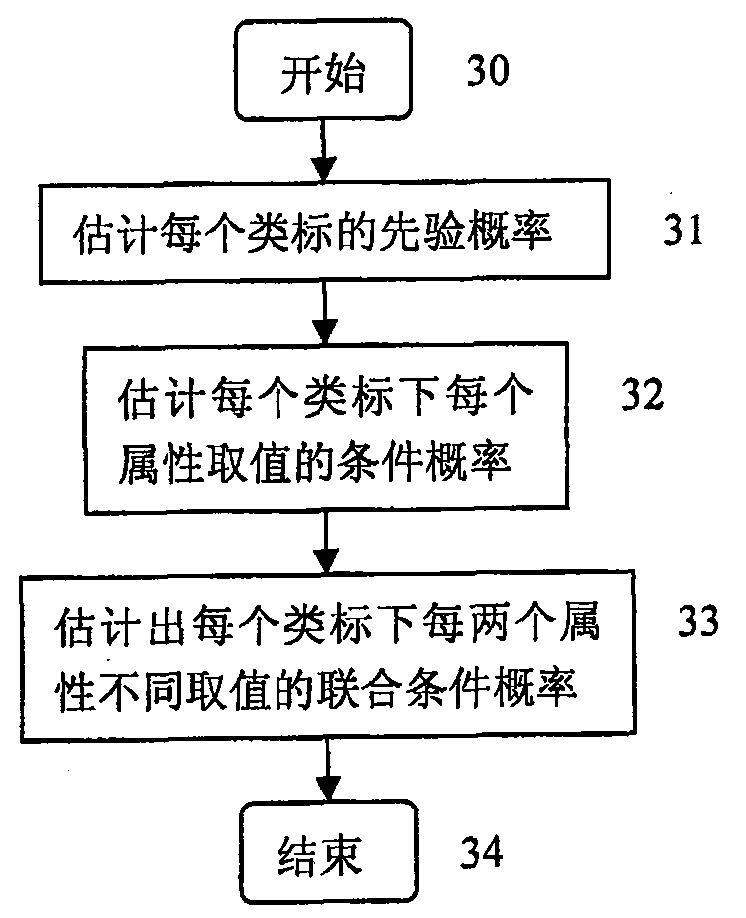
[0066] Step 0 is the initial state of the network intrusion classificatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com