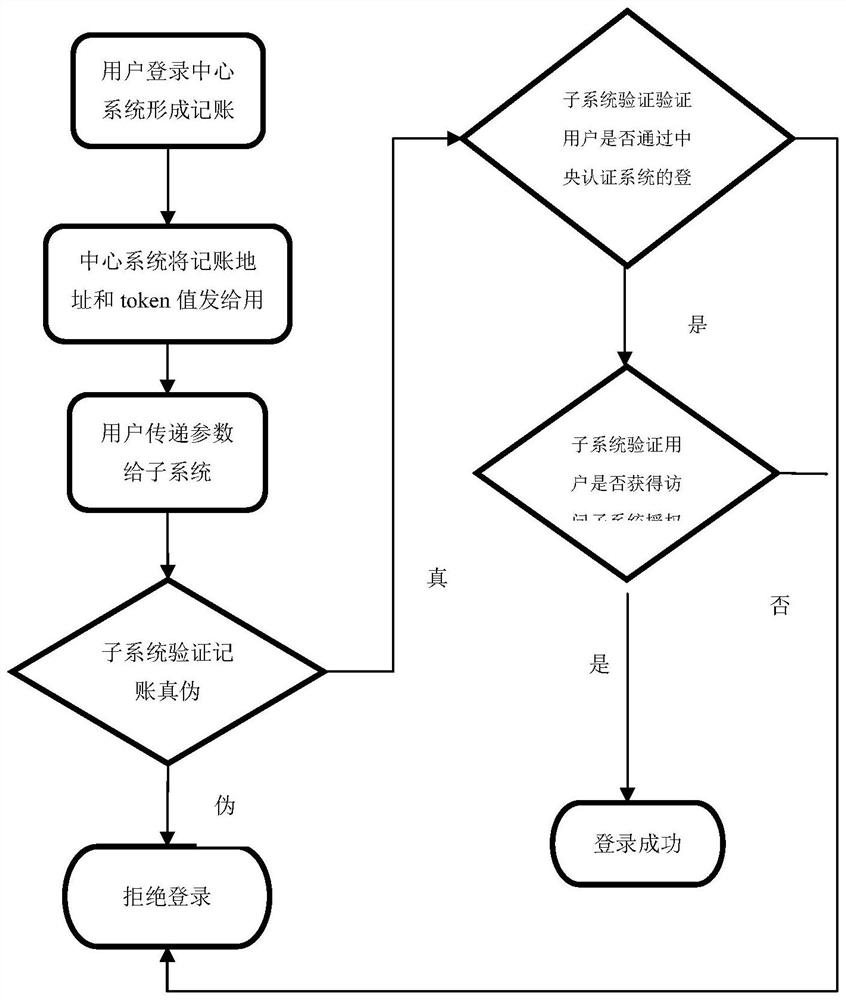
A secure single sign-on method based on blockchain zero-knowledge proof
A technology of zero-knowledge proof and login method, applied in the field of secure single sign-on and single sign-on based on blockchain zero-knowledge proof, it can solve the problems of frequent notification interaction, untrusted public cloud insecurity, etc. Query pressure, reduce pressure, reduce the effect of interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0041] Embodiment: In an untrusted cloud environment, 2 users log in to 5 subsystems;
[0042] The specific simulation parameters are as follows:
[0043] Let the subsystem IDs be 1 to 5 respectively, that is, sys_set={1,2,3,4,5};
[0044] User A is authorized to allow access to subsystems 1, 2, 3, namely auth_sys_set A ={1,2,3};
[0045] User B is authorized to allow access to subsystem 4,5, ie auth_sys_set B ={4,5};
[0046] 1. Log in to the central authentication system stage
[0047] After user A is authenticated by the central authentication system, the session token token allocated A =101, generate accounting account A , and save it to the shared storage area, the address is address A , and put address A and token A =101 sent to user A;
[0048] accounting account A The specific generation steps are as follows:
[0049] 1.1) Extract the coefficients of the constant term (t, a 1 ,a 2 ...a m+1 ), get (1,-107,617,-1116,505)
[0050] t(x-sys 1 )(x-sys 2 )(x...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com