IoT device access method, device, device and storage medium
A technology of IoT devices and access methods, applied in the field of IoT, can solve the problems of limited number of concurrency and limited access efficiency of IoT devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
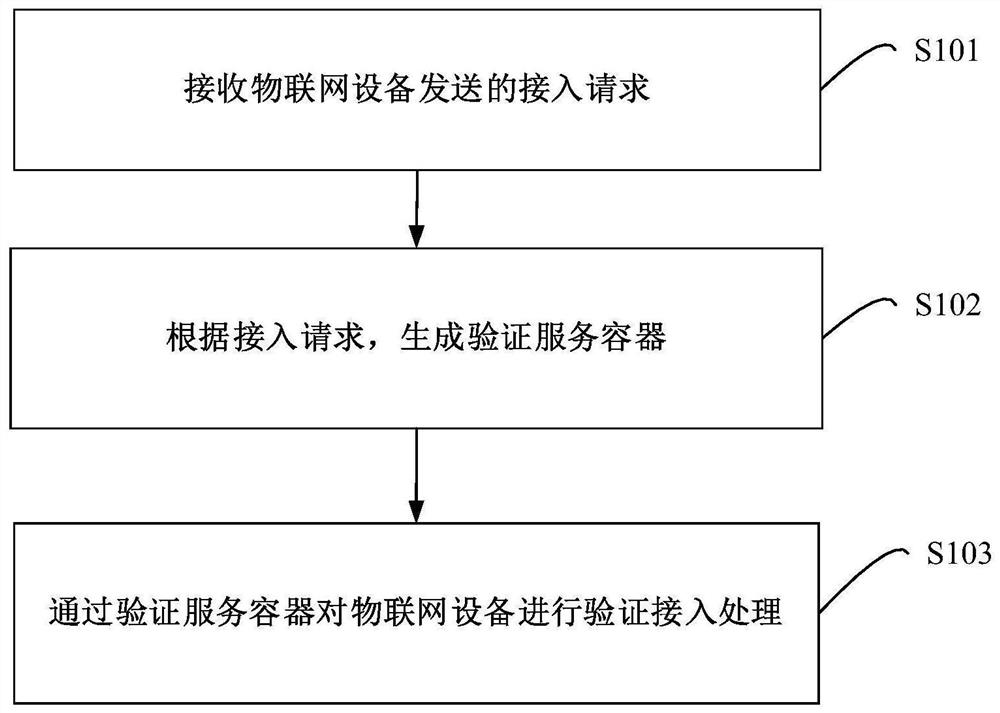
[0029] figure 1 It is a flow chart of the IoT device access method provided by Embodiment 1 of the present invention. The embodiment of the present invention aims at the problem that when large-scale Internet of Things devices request to access the Internet of Things concurrently, because the access server can handle the limited number of concurrent accesses of Internet of Things devices, which limits the access efficiency of Internet of Things devices, it provides Internet of things device access method. The method in this embodiment is applied to an access server. In other embodiments, the method can also be applied to other devices. This embodiment uses a terminal device as an example for schematic illustration. Such as figure 1 As shown, the specific steps of the method are as follows:
[0030] Step S101, receiving an access request sent by an Internet of Things device.
[0031] Wherein, the access request includes identification information of the IoT device.
[0032...
Embodiment 2
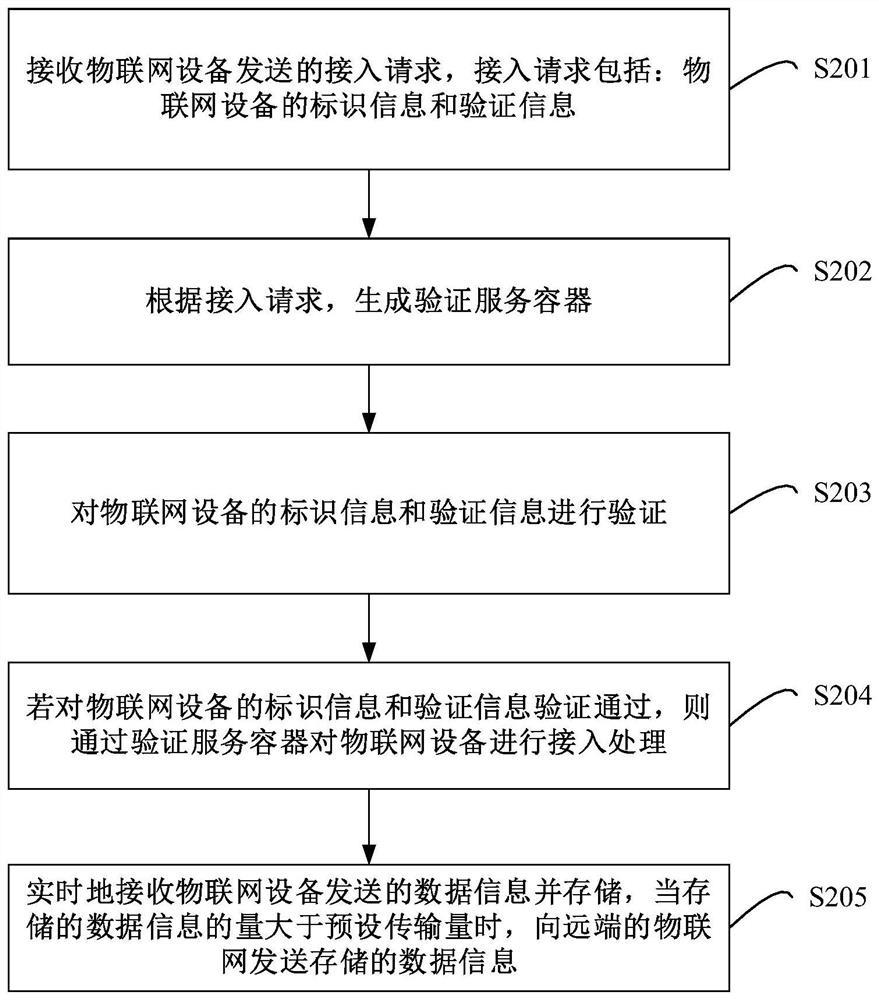
[0040] figure 2 It is a flow chart of the IoT device access method provided by Embodiment 2 of the present invention. On the basis of the first embodiment above, in this embodiment, the access request includes: the identification information and verification information of the IoT device, and the verification and access processing is performed on the IoT device through the verification service container, including: The identification information and verification information are verified; if the identification information and verification information of the Internet of Things device are verified, the Internet of Things device is accessed through the verification service container. Such as figure 2 As shown, the specific steps of the method are as follows:
[0041] Step S201, receiving an access request sent by an Internet of Things device, where the access request includes: identification information and verification information of the Internet of Things device.
[0042] W...
Embodiment 3
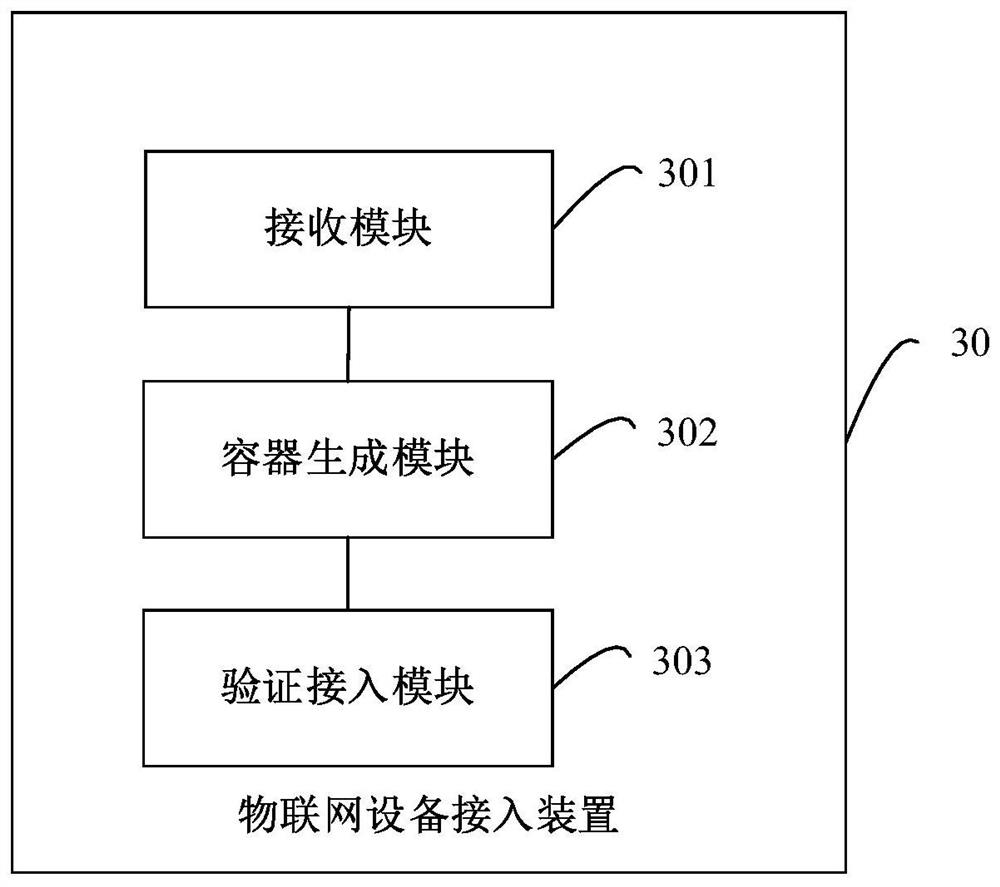
[0069] image 3 It is a schematic structural diagram of an IoT device access device provided in Embodiment 3 of the present invention. The Internet of Things device access apparatus provided in the embodiment of the present invention can execute the processing flow provided in the embodiment of the Internet of Things device access method. Such as image 3 As shown, the device 30 includes: a receiving module 301 , a container generating module 302 and a verification access module 303 .
[0070] Specifically, the receiving module 301 is configured to receive an access request sent by an IoT device.
[0071] The container generation module 302 is configured to generate a verification service container according to the access request.
[0072] The verification access module 303 is used for performing verification access processing on the IoT device through the verification service container.
[0073] The device provided in the embodiment of the present invention may be specifi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com