Method and system for detecting flow of peer-to-peer network
A traffic detection and peer-to-peer network technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as inability to accurately distinguish P2P application traffic, inability to achieve efficient and real-time detection, and complex machine learning implementations , to achieve the effect of improving concurrent processing capabilities, improving reliability and scalability, and good real-time performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] A method and system for peer-to-peer network traffic detection, used for real-time, efficient and accurate detection of encrypted and unencrypted P2P application traffic.
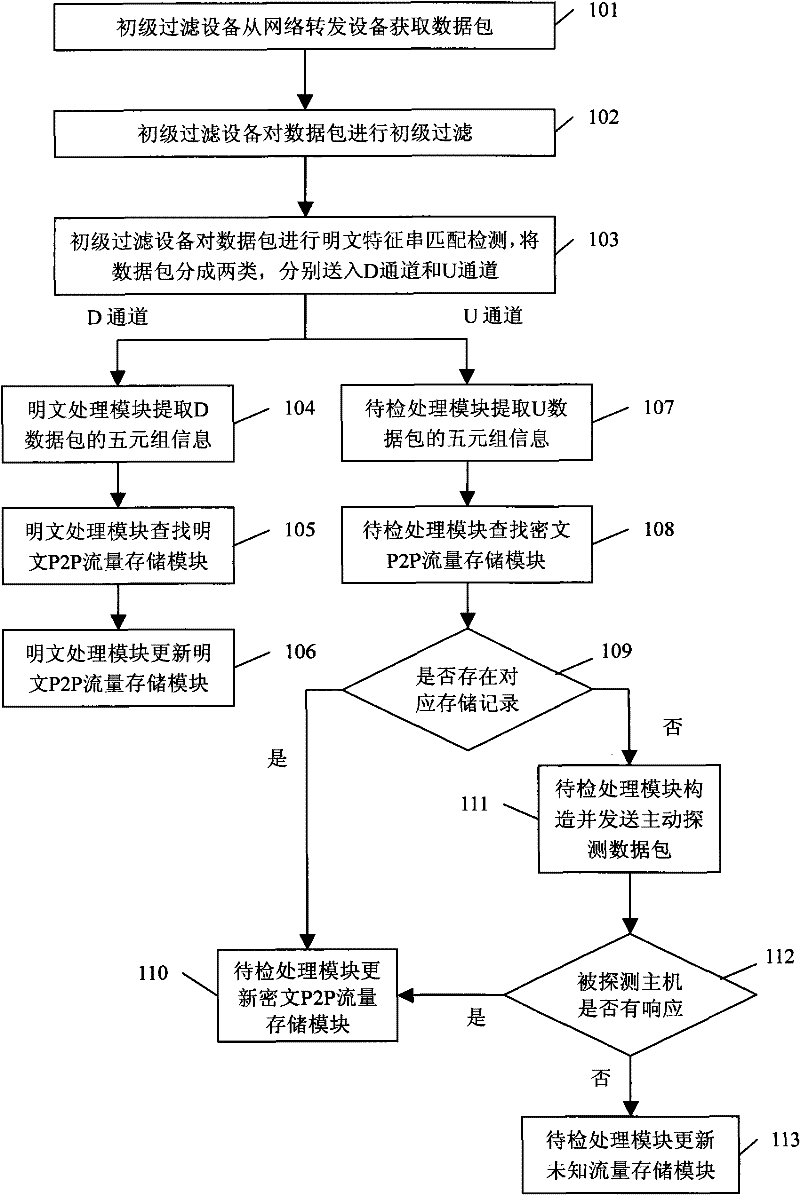
[0040] figure 1 It is a flow chart of the peer-to-peer network traffic detection method in this embodiment, and is described in detail through specific steps below:
[0041] Step 101, the primary filtering device obtains data packets from the network forwarding device
[0042] For a network forwarding device with a fiber interface, the primary filter device can obtain the original data packet through optical fiber splitting on the network forwarding device. For the network forwarding device with port mirroring function, the primary filtering device can obtain the original data packet through the mirror port on the network forwarding device. For network forwarding devices that do not have optical fiber interfaces and port mirroring functions, a network tap or hub can be connected to the uplink (Up-L...
Embodiment 2
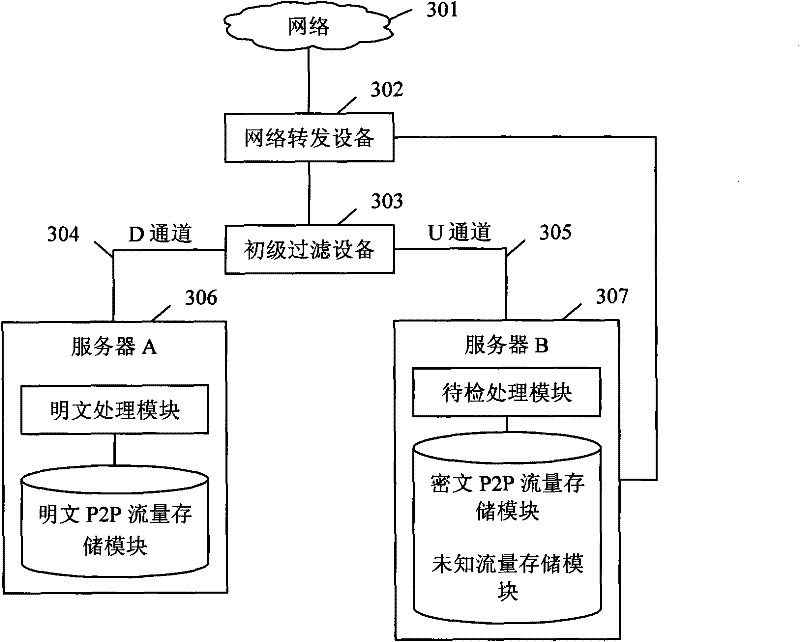
[0112] Figure 4 A network diagram of a peer-to-peer network traffic detection system provided in this embodiment includes a network 401, a network forwarding device A402, a primary filtering device 403, a server A404, a server B405, and a network forwarding device B406. in:
[0113] Network 401, that is, in Embodiment 1 image 3 The shown network 301 may be a network such as the Internet, a metropolitan area network, a campus network, or an enterprise network.
[0114] The network forwarding device A402 may be a router, a layer 3 switch, a layer 2 switch and other devices capable of forwarding data packets. The network forwarding device is only the data packet acquisition source of the primary filtering device.
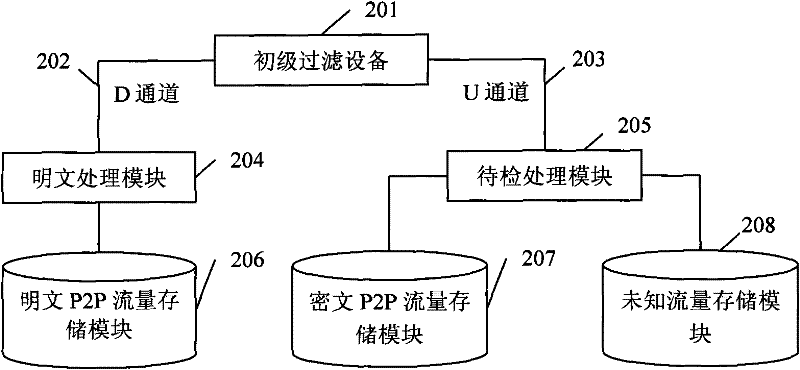
[0115] The primary filtering device 403 is the embodiment 1 figure 2 The primary filter device 201 is shown.
[0116] The server A404 specifically implements the figure 2 The plaintext P2P traffic storage module, the ciphertext P2P traffic storage module and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com