Computer security login guarantee system
A computer security, computer technology, applied in computing, image data processing, instruments, etc., can solve problems such as information leakage, inability to log in securely, passwords easily stolen, etc., to improve identification accuracy, improve information security, and reduce errors. the effect of the situation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The computer security login protection system provided by the present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
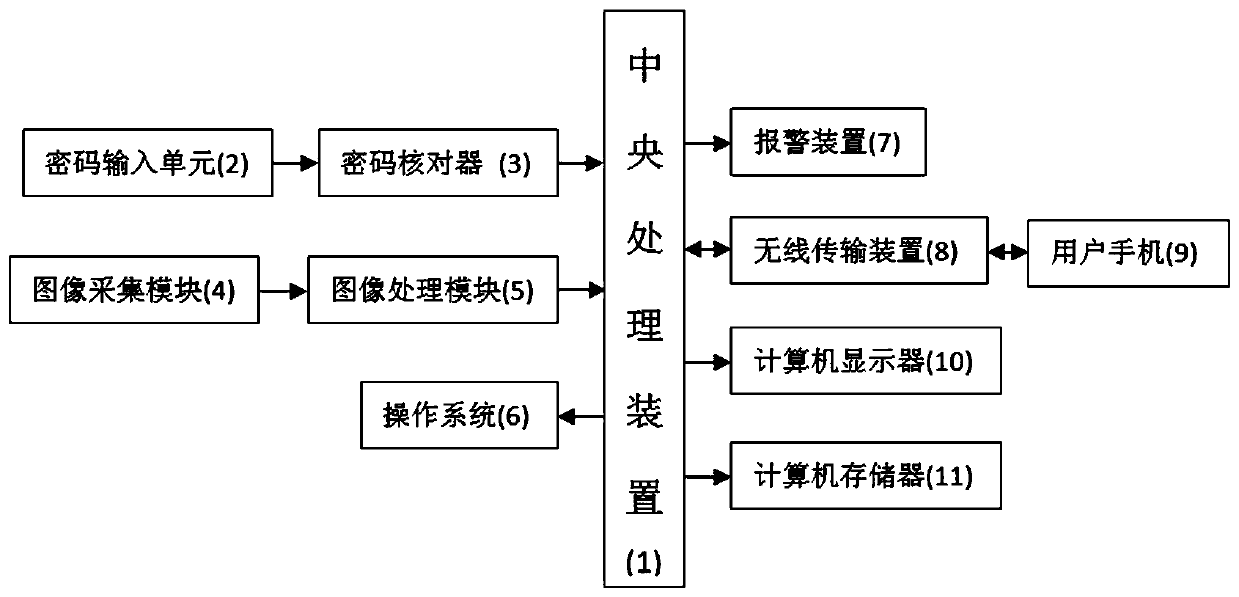
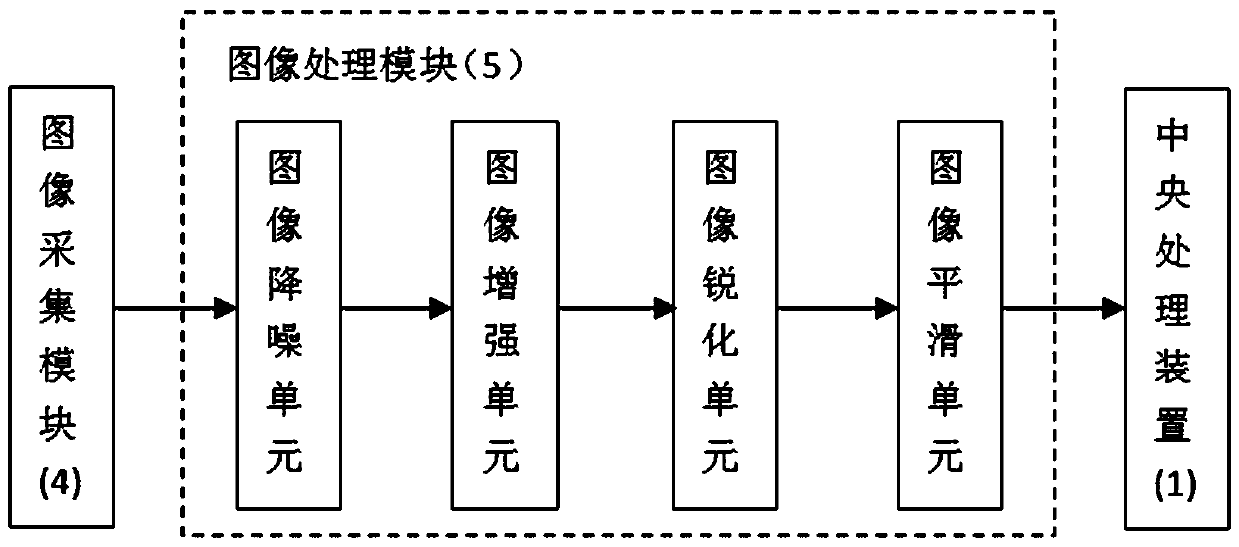
[0035] Such as figure 1 As shown, the computer security login guarantee system provided by the present invention includes a central processing device (1), a password input unit (2), a password checker (3), an image acquisition module (4), an image processing module (5), an operating system (6), alarm device (7), wireless transmission device (8), user mobile phone (9), computer monitor (10) and computer memory (11);
[0036] Wherein, the output end of the password checker (3) and the output end of the image processing module (5) are connected to the input end of the central processing unit (1), the input end of the operating system (6) and the input end of the alarm device (7) terminal, the input terminal of the computer monitor (10) and the input terminal of the computer memory (11) are all co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com