Method and device for automatically detecting Weblogic known loophole
An automatic detection and vulnerability technology, applied in electrical components, transmission systems, etc., can solve problems such as affecting user security, the server has no judgment method, affecting data availability, confidentiality and integrity, etc., to reduce manual detection and improve work. The effect of efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
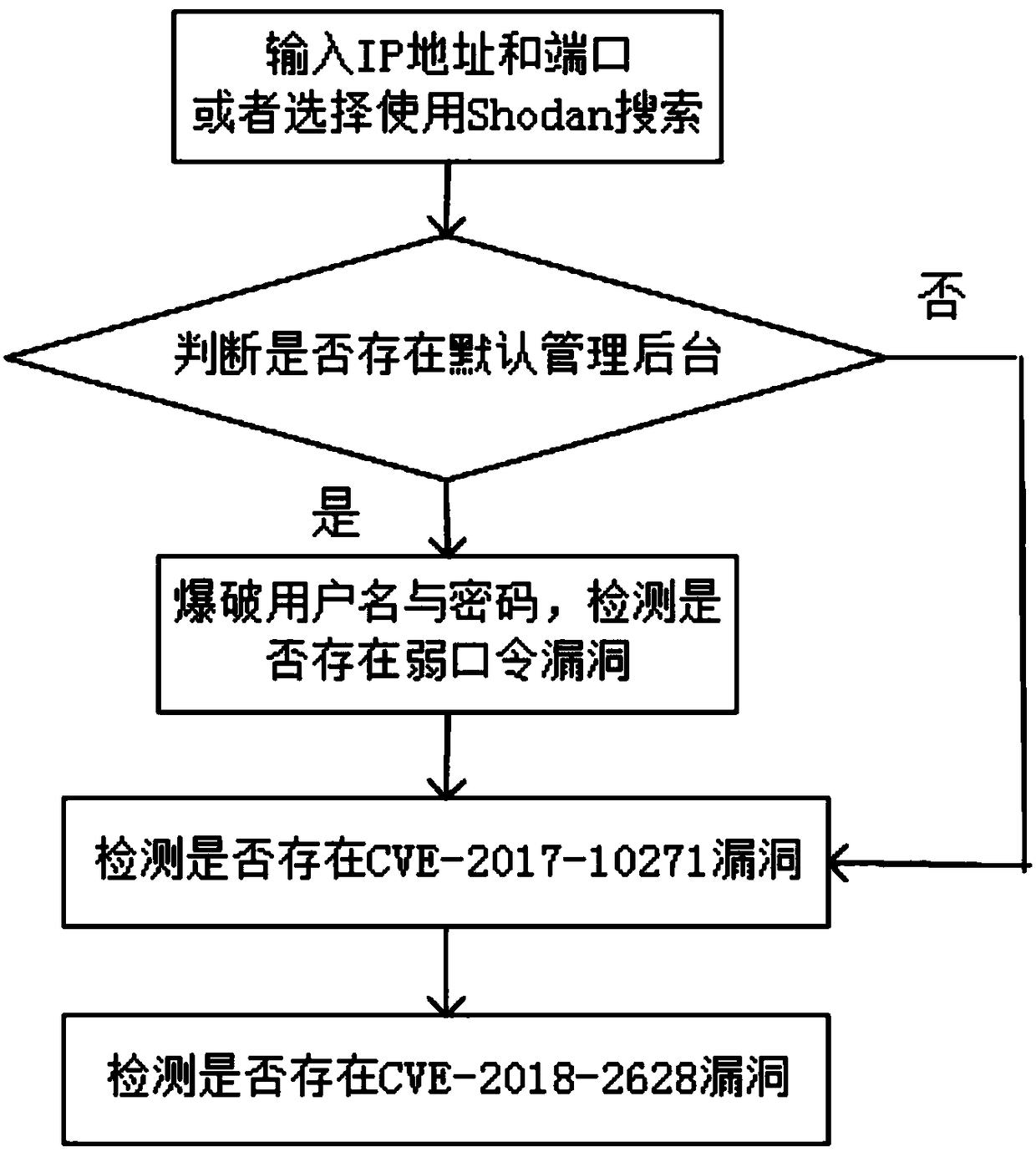
[0040] Such as figure 1 As shown, the embodiment of the present invention is a method for automatically detecting known loopholes in WebLogic, and the method includes:
[0041]S1: Find the WebLogic server to be detected.
[0042] The implementation of this step is mainly divided into two categories, one is to enter the IP address and port, and the other is to use Shodan to achieve.
[0043] Enter the IP address and port in one of the following two ways:
[0044] Method 1: Enter the IP address and port of the WebLogic server to be detected.
[0045] Method 2: Input a file ip.txt, said file ip.txt contains one or more IP addresses and ports, and each IP address and port corresponds to a WebLogic server.
[0046] The principle of using Shodan to realize is: use Shodan to search WebLogic, Shodan's URL is https: / / www.shodan.io / , Shodan is a search engine, but it is different from Google, a search engine that searches URLs, Shodan uses To search for online devices in cyberspace,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com