Power grid information security evaluation method and apparatus based on AHP and big data
A technology of security assessment and information security, applied in the field of information security, can solve the problems of inability to assess the security of vertically encrypted authentication devices, security risks, etc., and achieve the effects of improving accuracy, ensuring comprehensiveness, and ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
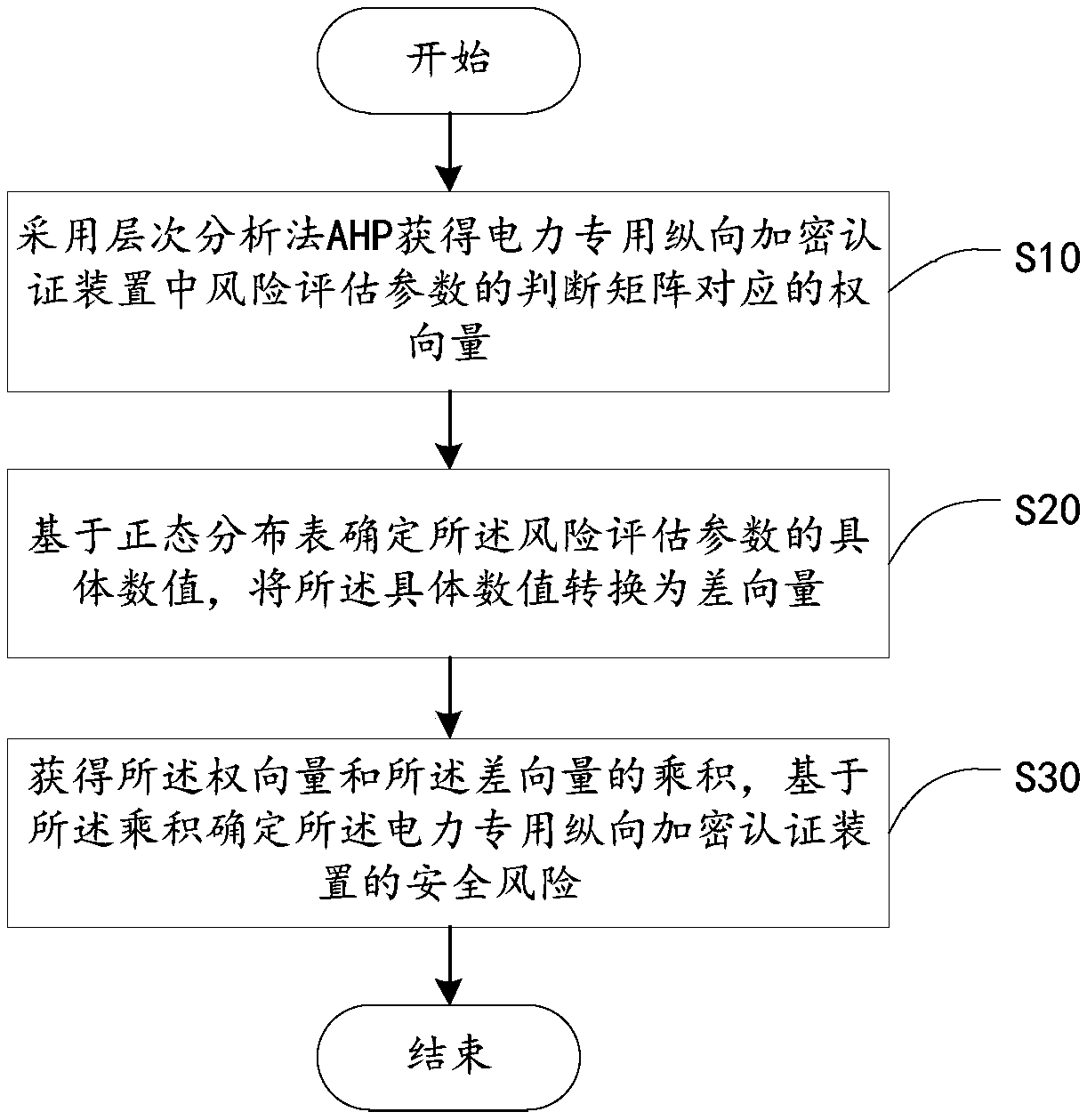
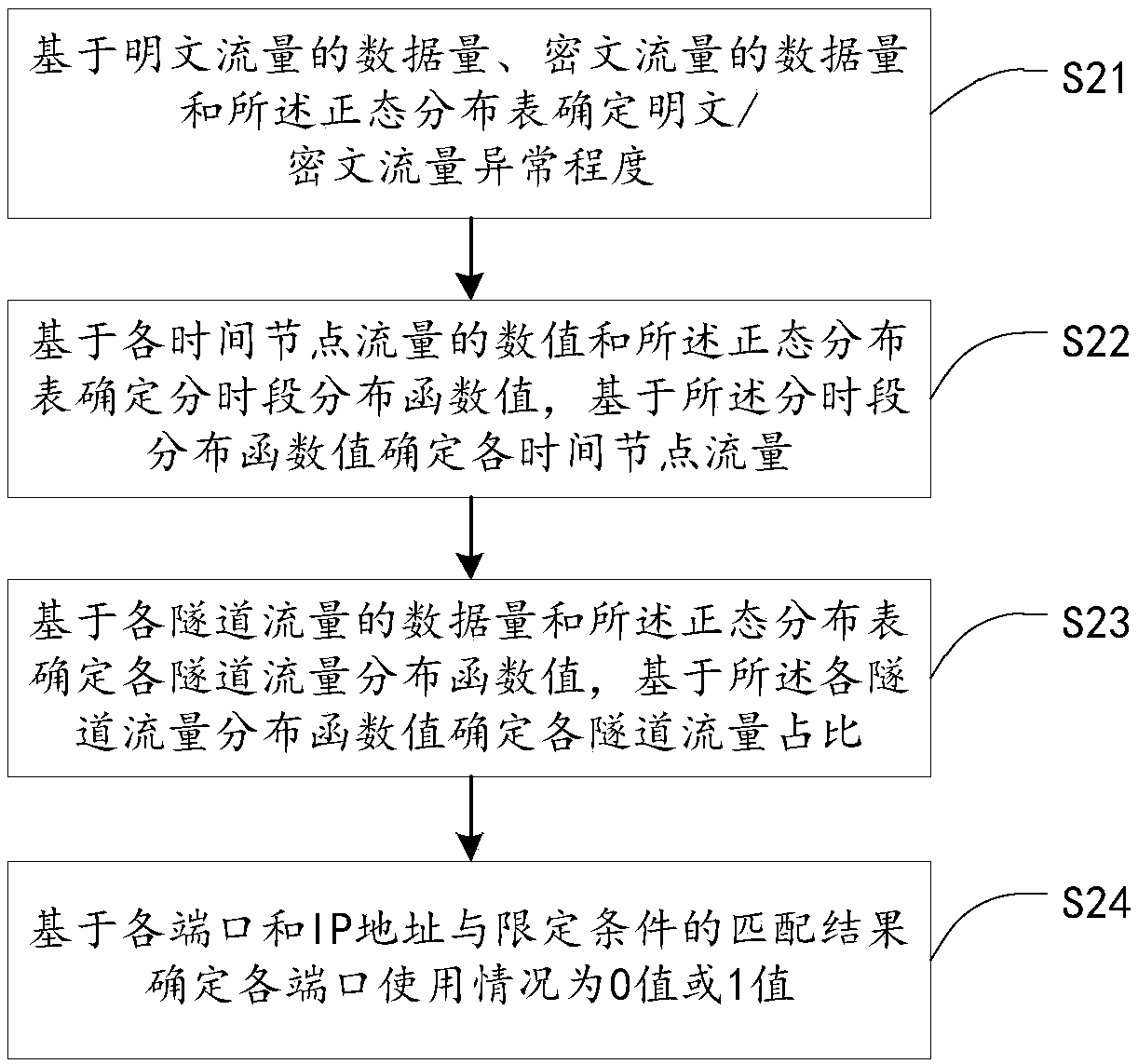
[0028]According to the applicant's research, it is found that the existing power grid information security assessment technology cannot perform accurate assessment based on the importance of each parameter in the vertical encryption and authentication device for electric power when performing security assessment on the data flow in the vertical encryption and authentication device for electric power. Security Risk Assessment. The current information security risk assessment can be summarized into three categories: quantitative risk assessment methods, qualitative risk assessment methods, and qualitative and quantitative assessment methods. Quantitative assessment methods often simplify and blur complex issues for the purpose of quantification, and some risk factors may be misunderstood after being quantified. Qualitative evaluation methods are too subjective and have high requirements for the evaluators themselves. The existing qualitative and quantitative comprehensive evalu...
no. 2 example
[0081] In order to cooperate with the grid information security assessment method based on AHP and big data provided in the first embodiment of the present invention, the second embodiment of the present invention also provides a power grid information security assessment device 100 based on AHP and big data.
[0082] Please refer to Figure 4 , Figure 4 A block diagram of a power grid information security evaluation device based on AHP and big data provided by the second embodiment of the present invention.
[0083] The security assessment device 100 includes a weight vector determination module 110 , a difference vector determination module 120 and a security risk determination module 130 .
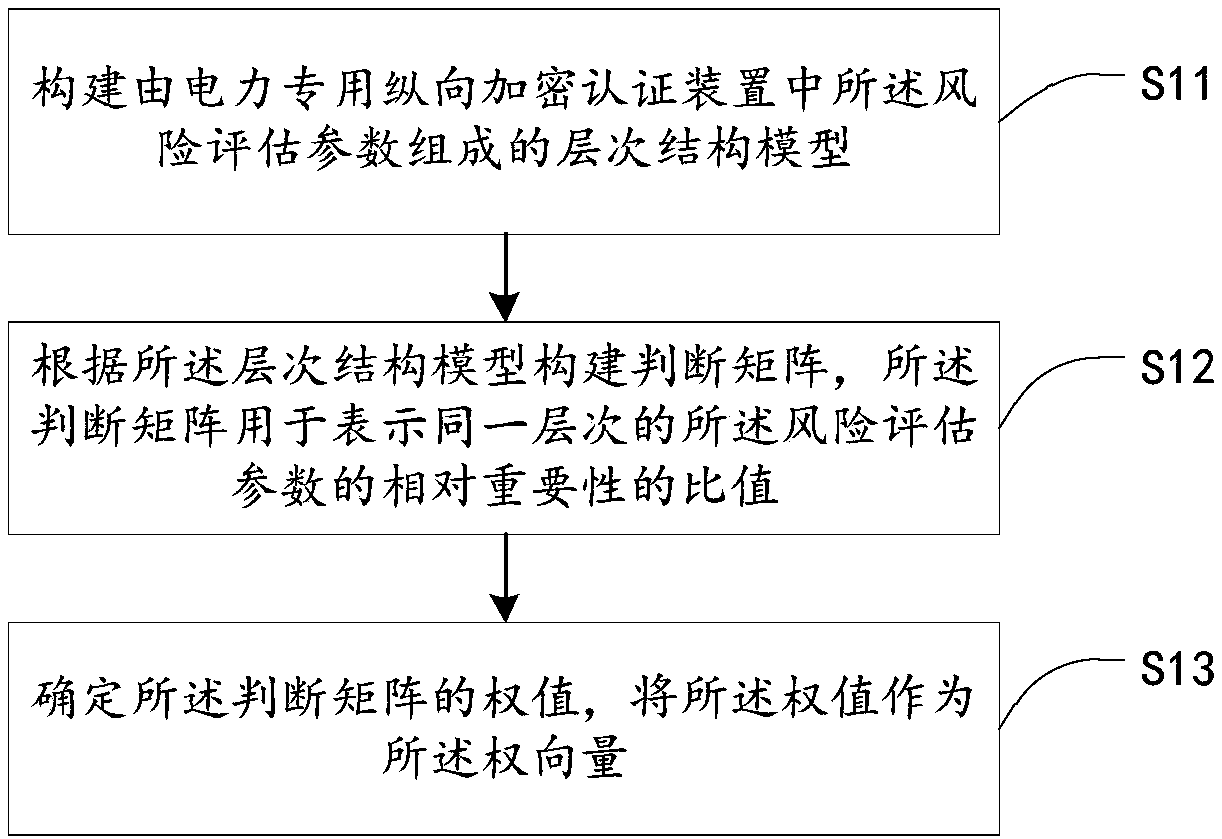
[0084] The weight vector determination module 110 is configured to obtain the weight vector corresponding to the judgment matrix of the risk assessment parameter in the electric power-specific vertical encryption authentication device by using the analytic hierarchy process (AHP).
...
no. 3 example
[0091] Please refer to Figure 5 , Figure 5 The third embodiment of the present invention provides a structural block diagram of an electronic device applicable to the embodiments of the present application. The electronic device 200 provided in this embodiment may include a security assessment apparatus 100 , a memory 201 , a storage controller 202 , a processor 203 , a peripheral interface 204 , an input and output unit 205 , an audio unit 206 , and a display unit 207 .
[0092] The memory 201, storage controller 202, processor 203, peripheral interface 204, input and output unit 205, audio unit 206, and display unit 207 are electrically connected to each other directly or indirectly to realize data transmission or interact. For example, these components can be electrically connected to each other through one or more communication buses or signal lines. The security assessment device 100 includes at least one software function module that can be stored in the memory 201 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com