A multi-layer anomaly detection method based on network traffic
An anomaly detection and network traffic technology, applied in the field of network security, can solve the problem that the detection effect of the anomaly detection classifier cannot be well satisfied, the attack behavior of small traffic cannot be well identified, and the attack behavior cannot be well detected and other problems, to achieve the effect of improving classification accuracy, data compactness, and parameter selection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in detail below with reference to the accompanying drawings and examples.
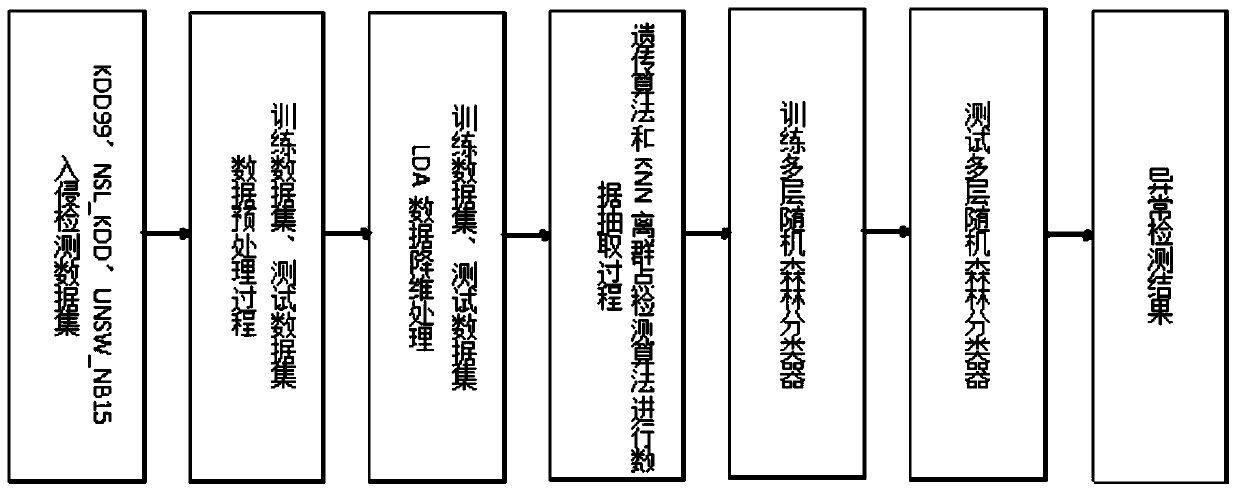
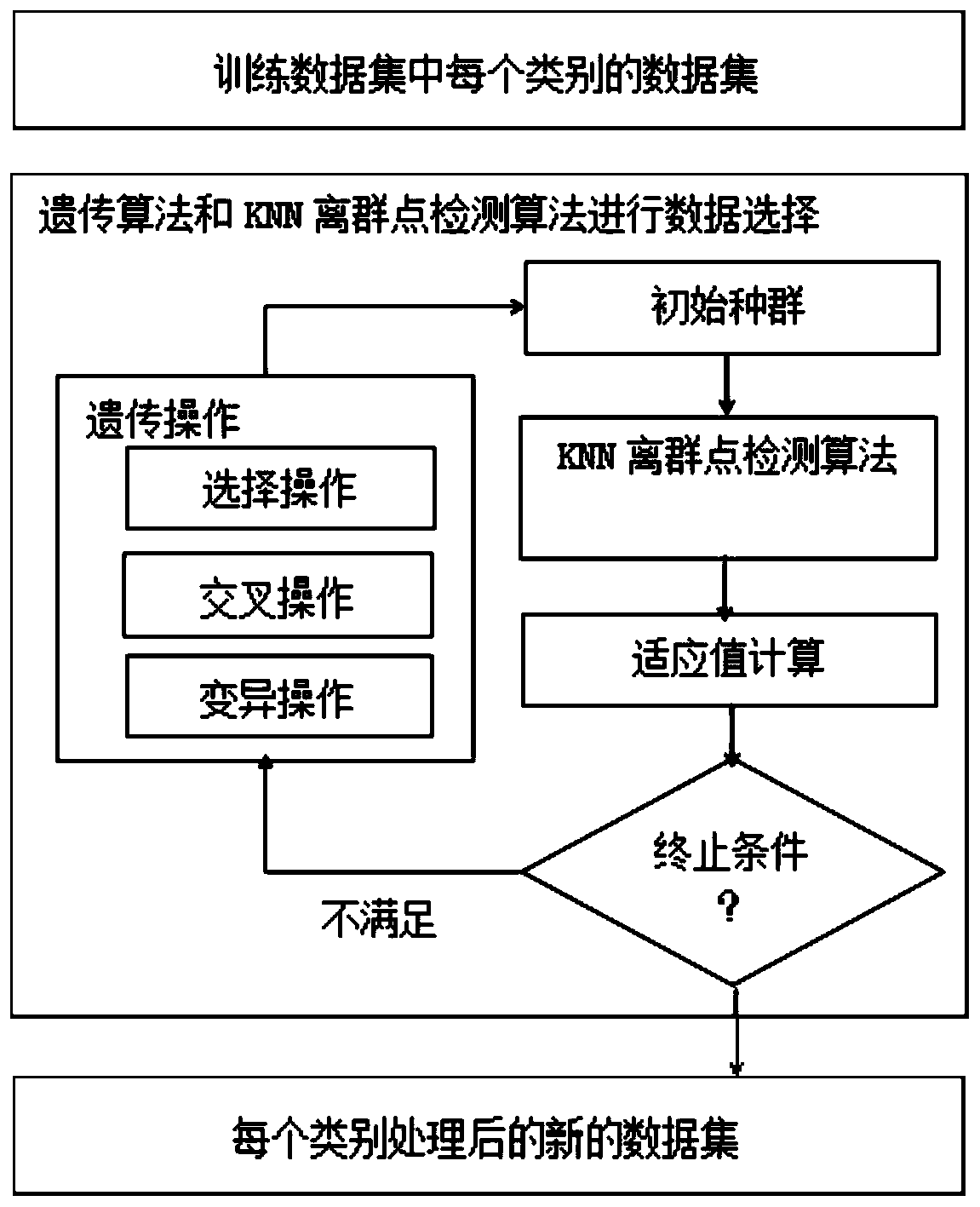
[0039] The invention provides a multi-layer anomaly detection method based on network traffic. The method combines a linear discriminant analysis method LDA, a genetic algorithm, a KNN outlier detection algorithm and a random forest algorithm, and is a fusion self-adaptive method.
[0040] This invention is based on the benchmark data set KDD99, the improved data set NSL_KDD of KDD99, and the NUSW_NB15 data set that is more in line with the modern network. Among them, the NUSW_NB15 data set is a network anomaly detection data set released in 2015, including 9 new attacks Type, this data set can better reflect the traffic characteristics and attack methods of the current network.
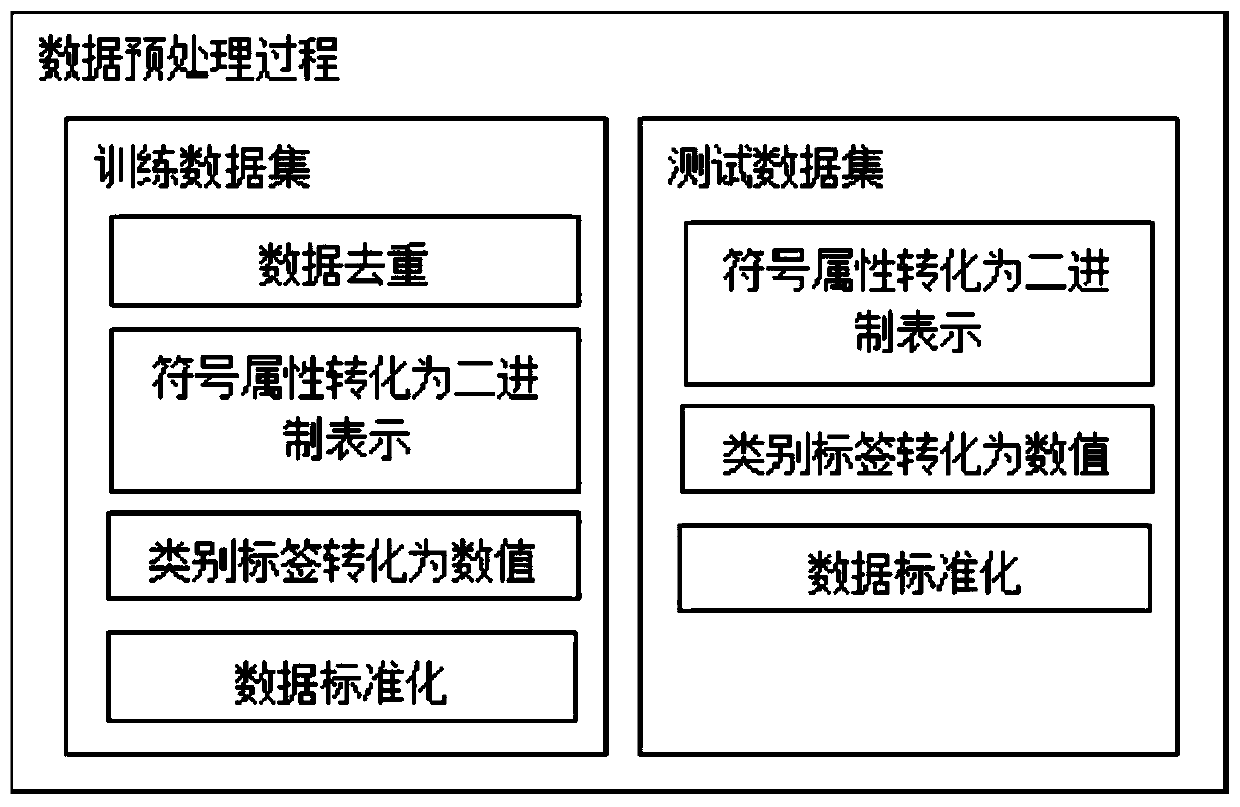
[0041] The method of the invention can be divided into two aspects: data processing and anomaly detection. Data processing mainly uses LDA, genetic algorithm and KNN outlier det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com