An improved ppt2003 file deciphering method and device
A file and header file technology, applied in the field of information security, can solve problems such as password error, inability to decrypt each object, inability to open encrypted files correctly, etc., to ensure correctness, speed up cracking, and reduce the amount of calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
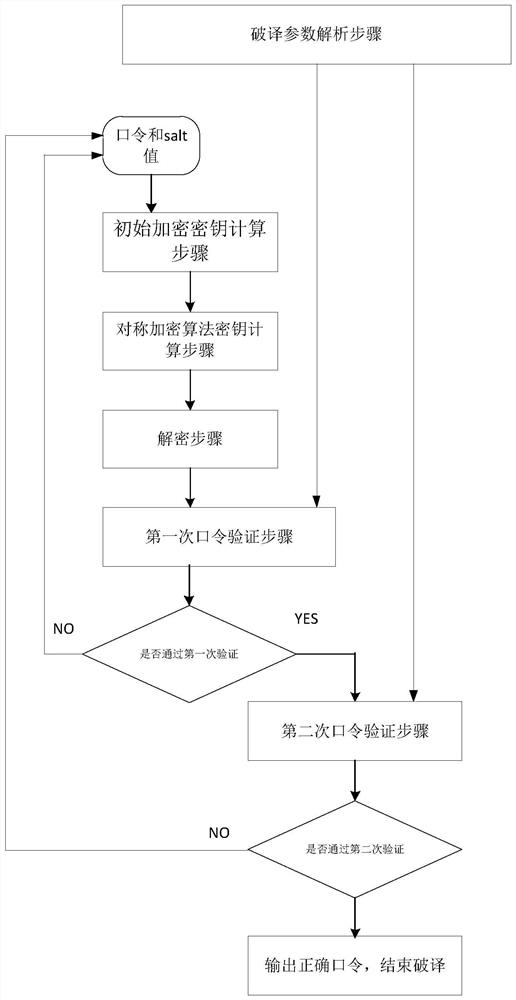
[0032] as attached figure 1 As shown, this embodiment discloses a process of an improved PPT2003 file deciphering method, which deciphering method includes:
[0033] S1, deciphering parameter analysis step, from the encrypted file to be deciphered, extract the parameters and ciphertext required for deciphering, wherein, the parameters required for deciphering include salt value, encrypted fresh number and its corresponding hash value, encrypted documentAtom header file data;
[0034] S2. The initial encryption key calculation step is to calculate the initial encryption key key according to the input password password and salt value;
[0035] S3, the symmetric encryption algorithm key calculation step, according to the initial encryption key key, select the block number corresponding to the documentAtom header file data, and generate the symmetric encryption algorithm key key1 required for decrypting the documentAtom header file data according to the hash algorithm;
[0036] ...
Embodiment 2
[0041] In this embodiment, the file header of documentAtom is used as fixed data, and the corresponding block number is 2. Assume that the newly added password verification of the present invention is the first password verification, and the original password verification is the second password verification. The specific deciphering method is as follows:
[0042] R1. Obtain the salt value, the encrypted fresh number and its corresponding hash value, and the encrypted documentAtom header file data from the encrypted PPT2003 file.
[0043] R2, according to the input password password and salt value, and then use the hash algorithm to generate the key key required for decryption.
[0044] R3. Using the key key and the block number 2 corresponding to the documentAtom, generate the key key1 required for decrypting the documentAtom header file.
[0045] R4. Use the key key1 to decrypt the encrypted documentAtom header file data, and then compare them. If they are not equal, it is ...
Embodiment 3
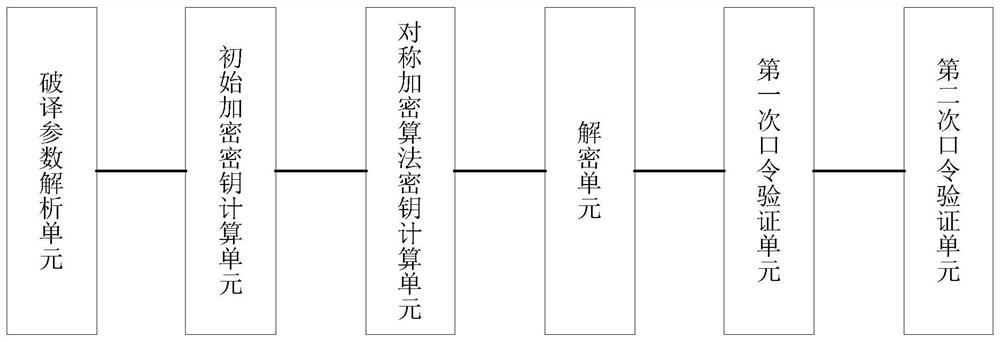
[0051] as attached figure 2 As shown, an improved PPT2003 file deciphering device, the deciphering device includes deciphering parameter analysis unit, initial encryption key calculation unit, symmetric encryption algorithm key calculation unit, decryption unit, first password verification unit connected in sequence and the second password verification unit, wherein,
[0052] The deciphering parameter parsing unit is used to extract the parameters and ciphertext required for deciphering from the encrypted file to be deciphered, wherein the parameters required for deciphering include salt value, encrypted fresh number and its corresponding hash value, Encrypted documentAtom header file data;
[0053] The initial encryption key calculation unit is used to calculate the initial encryption key key according to the input password password and salt value;
[0054] The symmetric encryption algorithm key calculation unit is used to select the block number corresponding to the docum...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com