Method for performing security binding, medium, equipment and terminal
A terminal and security technology, which is applied to security devices, secure communication devices, and key distribution, can solve problems such as the inability to prevent malicious binding of terminals, and achieve the effect of improving security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
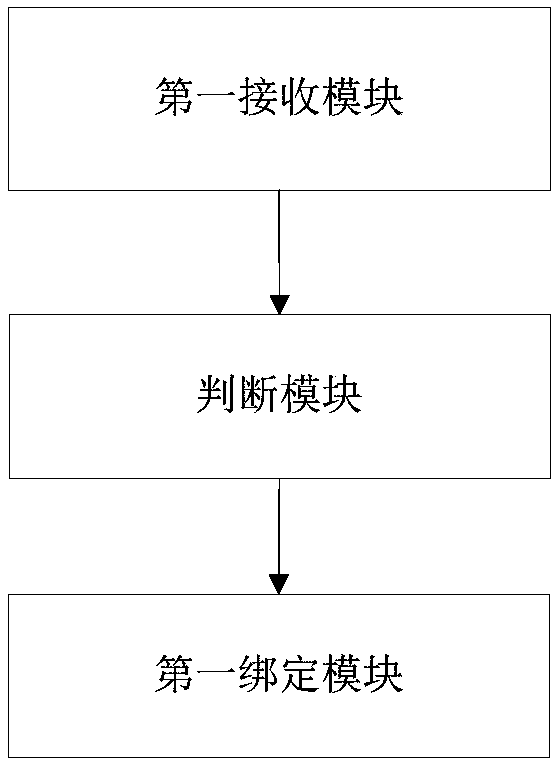
[0049] figure 1 It is a flow chart of a method for performing secure binding on a cloud device in Embodiment 1, and the method includes:
[0050] Step 101, receiving a binding request from a terminal, wherein the binding request includes at least unique configuration identification information of the terminal and a smart device identification of the smart device to be bound;
[0051] Step 102, determining whether there is a pre-stored correspondence between the unique configuration identification information of the terminal and the smart device identification of the smart device to be bound;
[0052] Step 103, in the case that the above-mentioned corresponding relationship is pre-stored, bind the terminal and the smart device to be bound.
[0053] This method only allows terminals that have a corresponding relationship with the smart device to be bound to the smart device, while terminals that do not have a corresponding relationship with the smart device cannot be bound. Th...
Embodiment 2
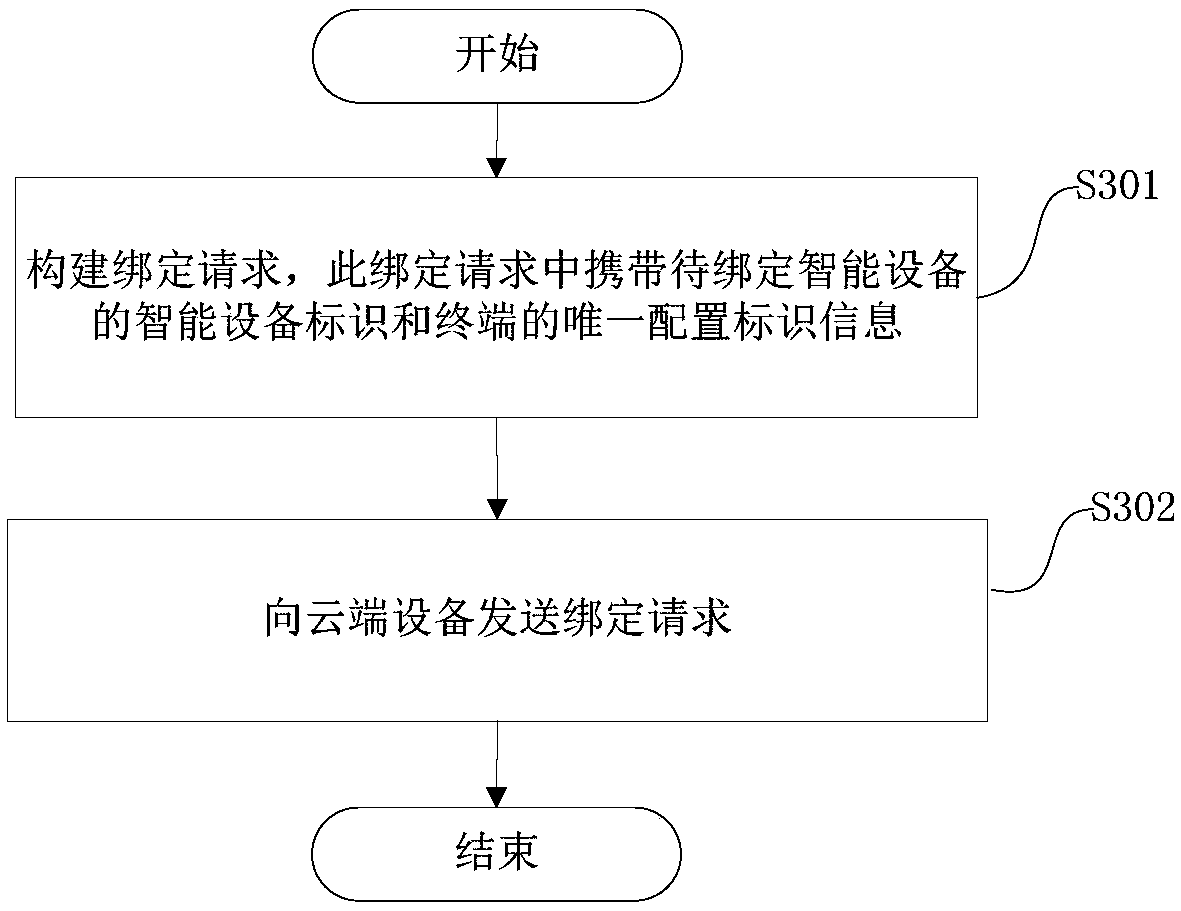
[0068] Embodiment 2 provides a method for performing security binding, which is applied to a terminal, such as image 3 As shown, this method includes:
[0069] Step 301, constructing a binding request, which carries the smart device identification of the smart device to be bound and the unique configuration identification information of the terminal;
[0070] Step 302, sending a binding request to the cloud device.
[0071] This method also includes before step 301:
[0072] Step 300-1, generating unique configuration identification information of the terminal; specifically, generating unique configuration identification information according to the timestamp information, or generating unique configuration identification information according to the timestamp information and the identification of the terminal.
[0073] Step 300-2, sending a configuration network access command to the smart device, and configuring the network access command to carry the unique configuration ...
Embodiment 3
[0086] The method for secure binding applied to smart devices in the third embodiment includes: receiving configuration network access instructions from the terminal, parsing network access information and unique configuration identification information from the configuration network access instructions, accessing the local area network according to the network access information, accessing After success, send the identification of the smart device and the unique configuration identification information to the cloud device; and, after the access is successful, send the identification of the smart device to the terminal.
[0087] The smart device in this embodiment three includes:
[0088] The fourth receiving module is used to receive configuration network access instructions from the terminal;
[0089] The parsing module is used to parse the network access information and the unique configuration identification information from the configuration network access instruction;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com