A searchable public key encryption method, system and server using the method
A public key encryption and server technology, which is applied in the field of cryptography and cloud storage security, can solve the problems of high efficiency of ciphertext data, achieve the effect of simple algorithm, reduce complex cryptographic operation process, and reduce time overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
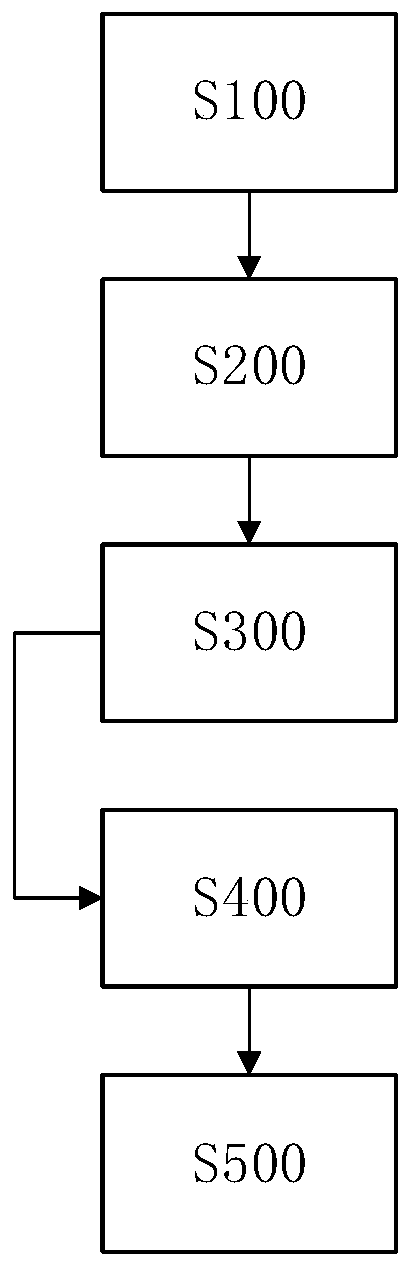
[0055] refer to figure 1 , this embodiment discloses a searchable public key encryption method. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
[0056] According to a preferred embodiment, the method of the present invention may include step 100: construct a bilinear map according to preset security parameters, and output a public parameter PK and a private key SK. Preferably, the public parameter PK is public. That is, anyone can obtain the public parameter PK. For example, sender A and / or server B. The private key SK is kept secretly by the receiver C. It should be noted that the public parameter PK may be called the master public key PK in some other documents, and the private key SK is called the master private key SK, or adopt other equivalent names mentioned in the present invention. As long as it is consistent with the idea expressed in the present invention, it should ...
Embodiment 2
[0077] This embodiment is a further improvement on Embodiment 1, and repeated content will not be repeated here. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
[0078] According to a preferred embodiment, the method of the present invention may further include: a keyword extraction step.
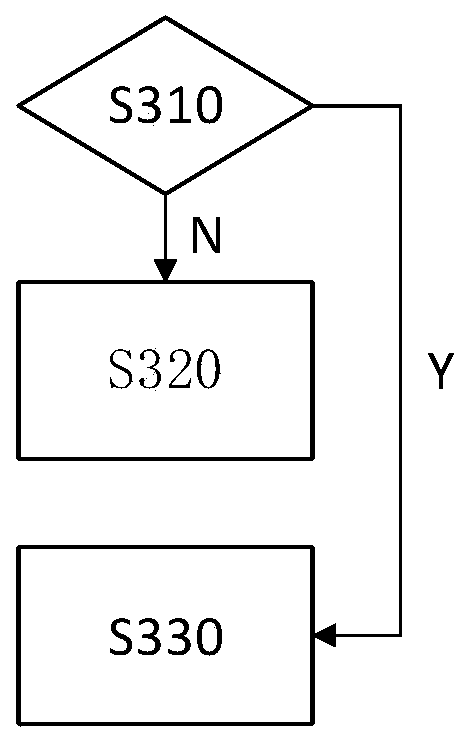
[0079] Preferably, the keyword extraction step includes: obtaining a file to be encrypted; extracting keywords from the file to be encrypted according to a preset keyword sample set, the keyword sample set includes keywords of different granularities; keyword is used as the keyword of the file to be encrypted. Obtaining keywords in this way is efficient and complete, and avoids the problem that sender A misses mentioning, wrong keywords, or receiver C and sender A have inconsistent understanding of the file, resulting in receiver C being unable to effectively retrieve relevant files. .
[008...
Embodiment 3
[0087] This embodiment is a further improvement on Embodiment 1 or 2 and their combination, and the repeated content will not be repeated. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
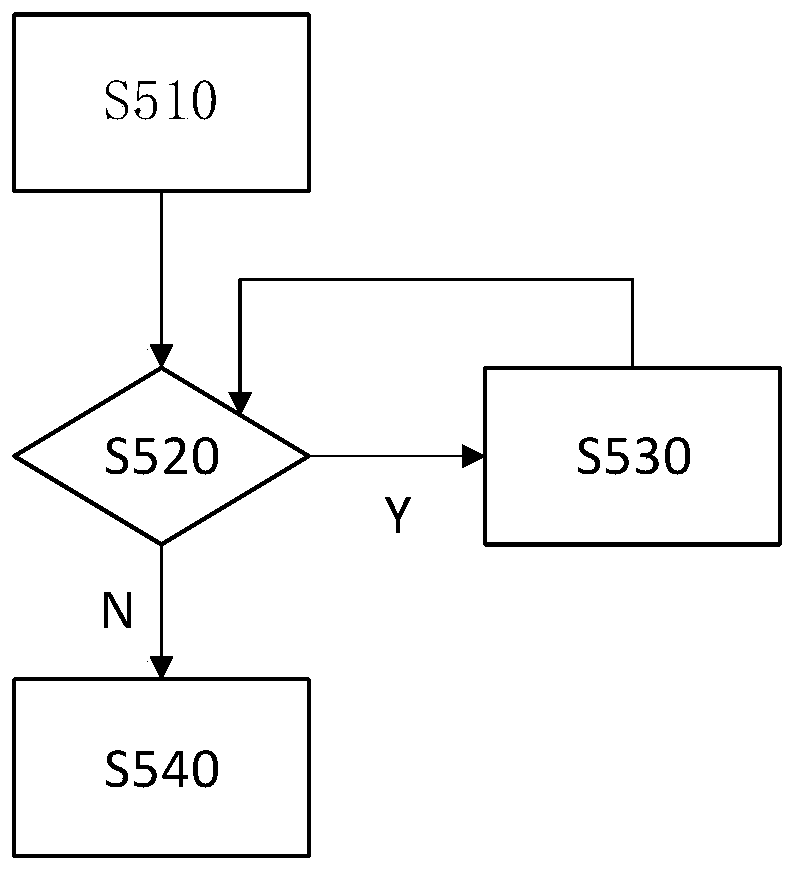
[0088] refer to Figure 4 , the present invention also discloses a practical searchable public key encryption system, which is suitable for executing each method step described in the present invention, so as to achieve the expected technical effect. In this embodiment, the key distribution center D is set independently. The independent key distribution center can make the system have higher security. Especially in the case where the owners of the key distribution center D and the server B are different, the possibility of the private key being leaked by the server B can be reduced. It can also prevent the server B from checking the specific situation of the keyword W privately and intercepting...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com