Electronic key management method and device
An electronic key and management method technology, applied to instruments, time registers, individual input/output registers, etc., can solve the problems of reduced security of electronic keys, inability to use visitor authorization, and inability to access owners, etc. The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
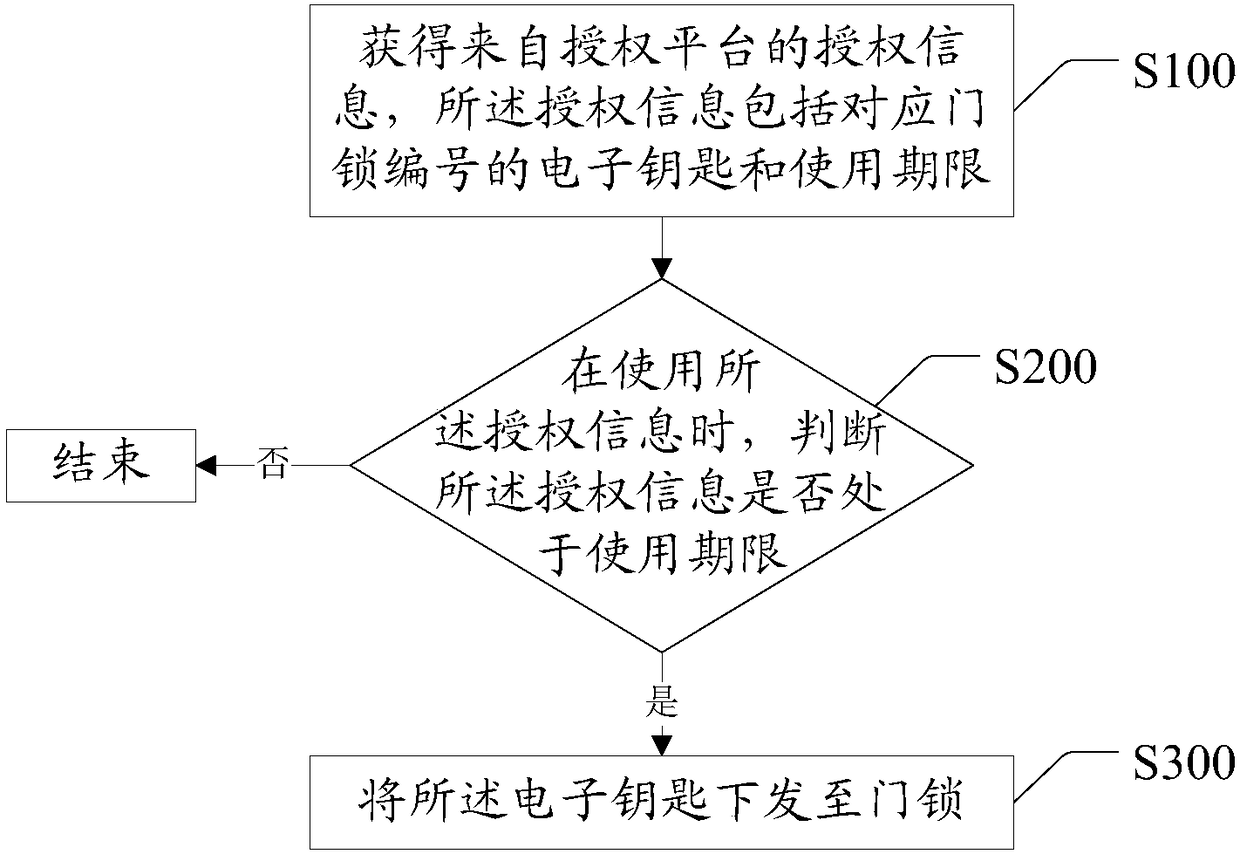
[0075] Please see figure 1 , The first embodiment of the electronic key management device of the present invention is used to manage electronic keys of offline mobile terminals. The electronic key management method includes the following steps:
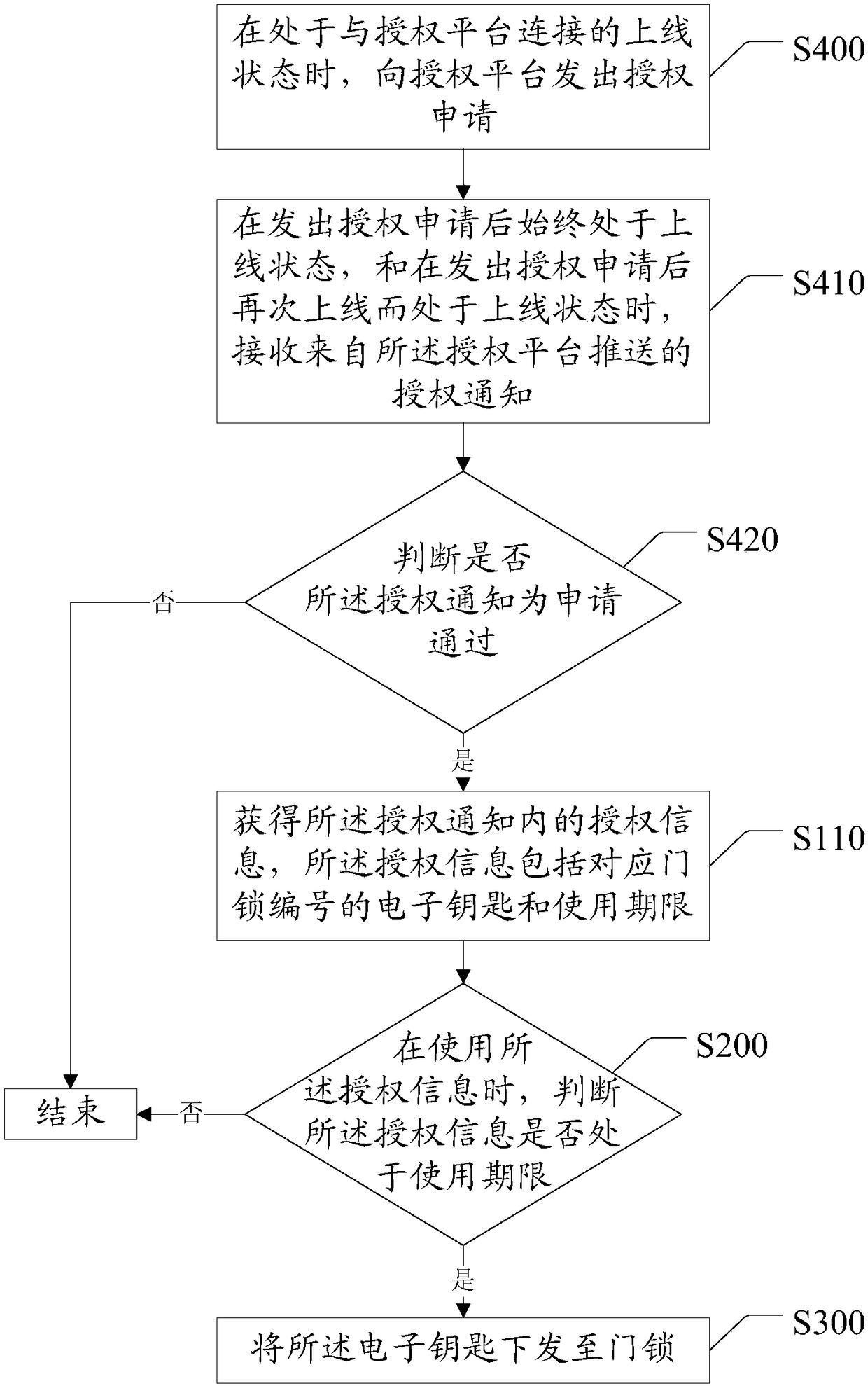
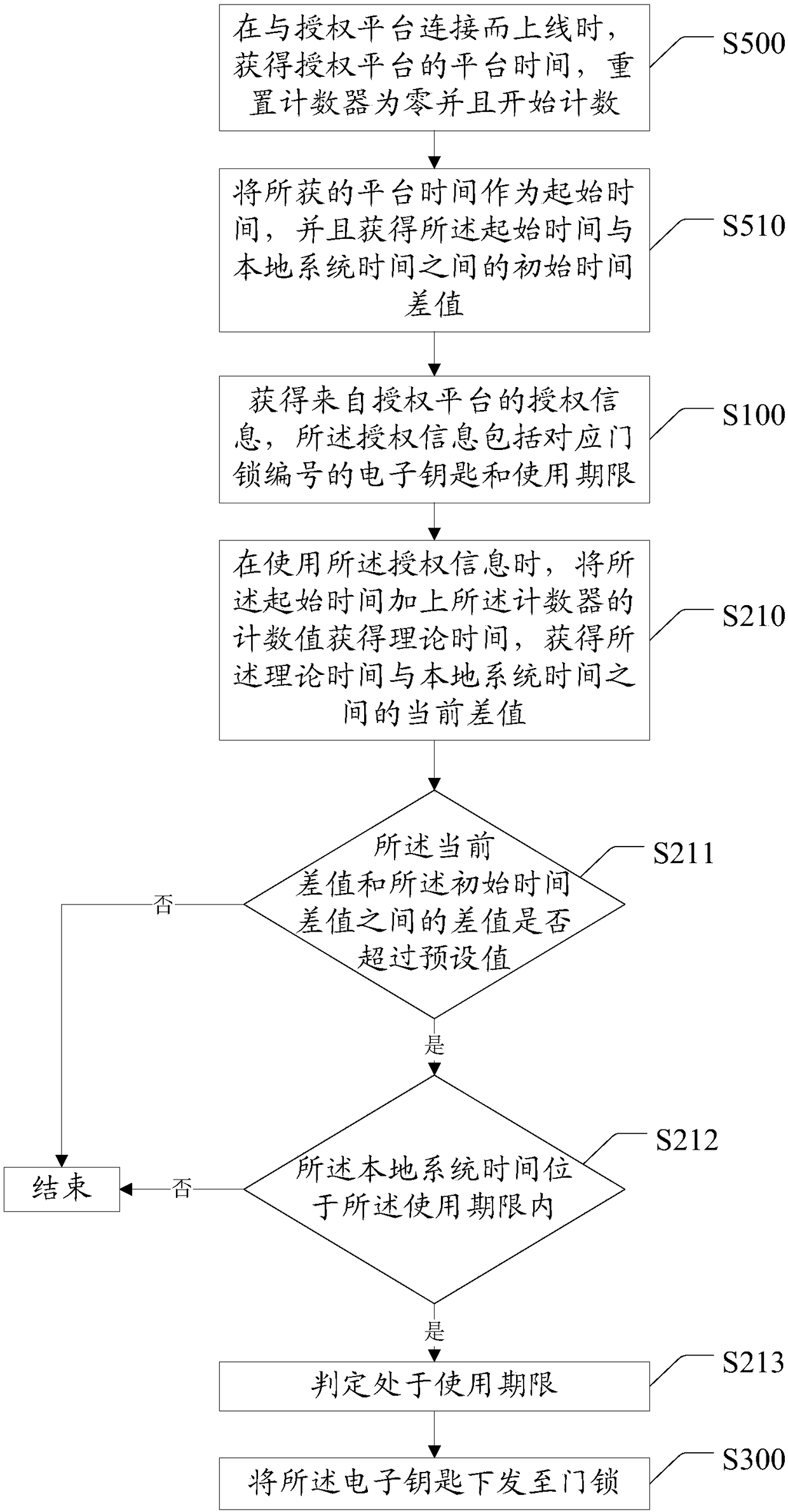
[0076] Step S100: Obtain authorization information from the authorization platform, the authorization information includes the electronic key corresponding to the door lock number and the expiration date; wherein the visitor's mobile terminal is connected to the authorization platform through the network and applies for the electronic key. After the authorization platform passes, the corresponding electronic key will be issued to open the door lock with the corresponding number. The use period can be set according to needs, such as 10s, 60s, 3 minutes, or 10 minutes.
[0077...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com