Threat processing system based on smart grid information security detection
A smart grid and information security technology, applied in the field of threat processing systems, can solve the problems of lack of three-dimensionality, inability to guide the construction of smart grid security systems, lack of linkage, etc., and achieve the effect of comprehensive guidance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0025] The technical scheme that the present invention solves the problems of the technologies described above is:
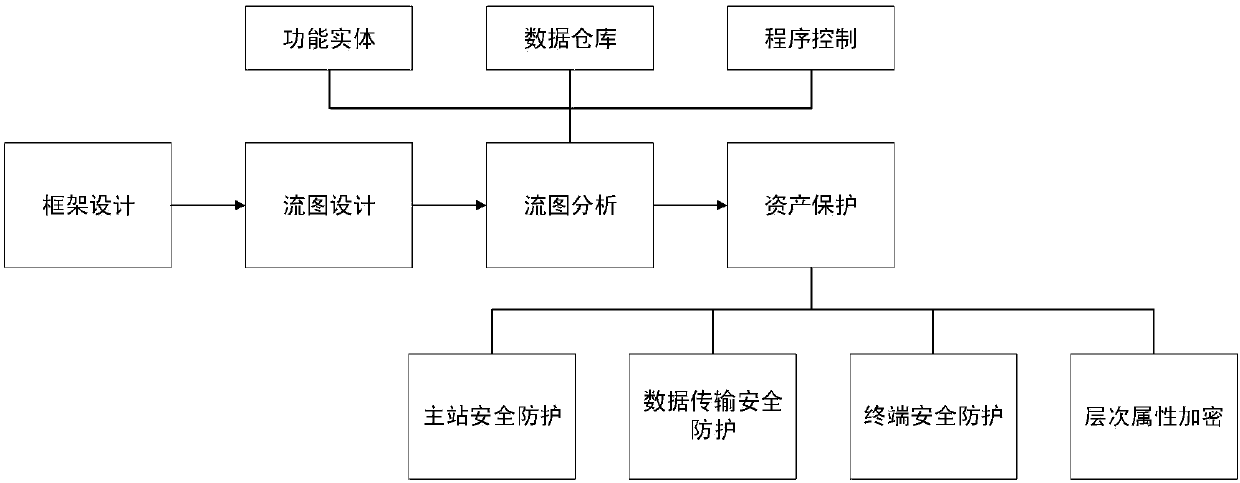
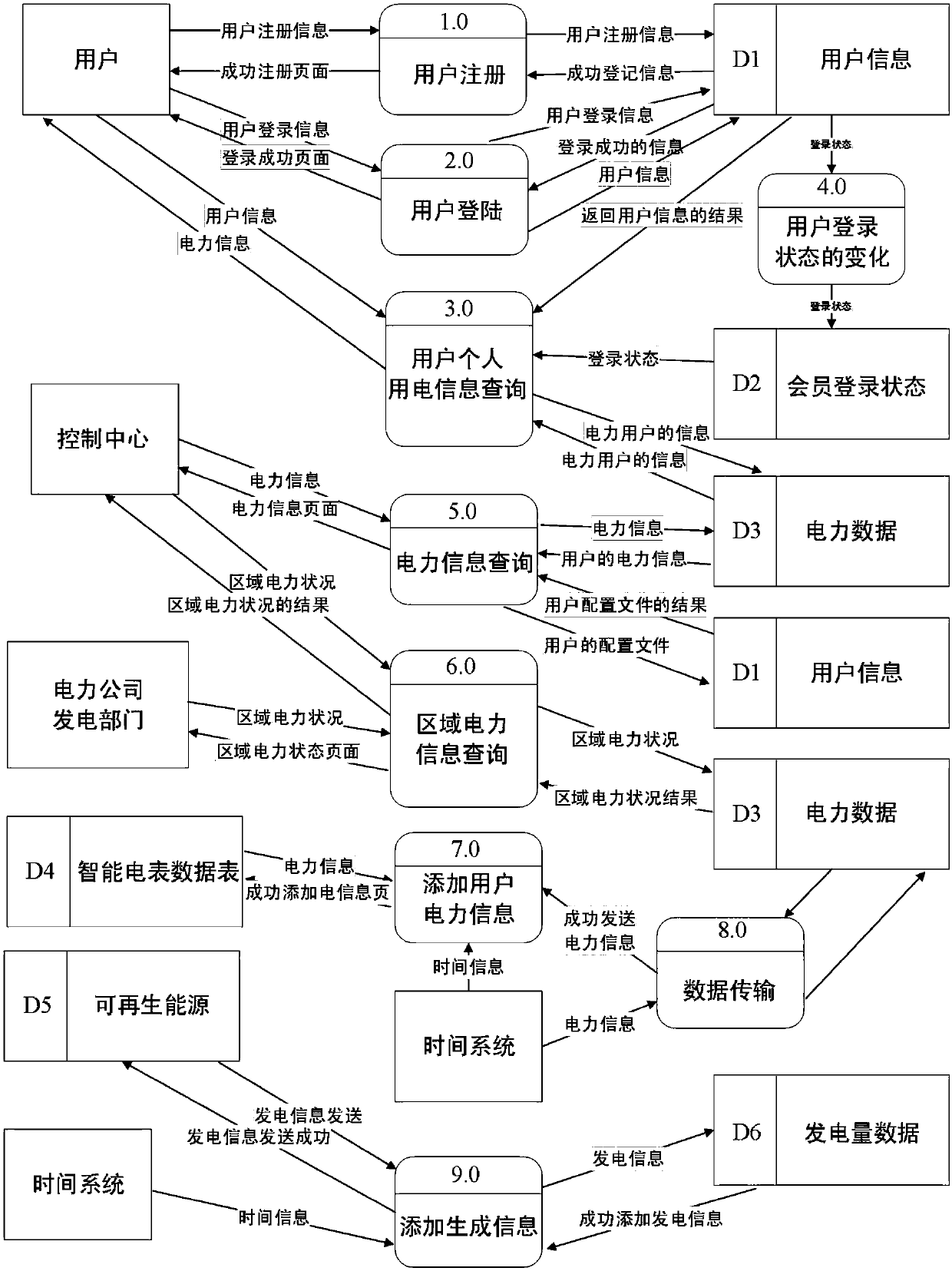
[0026] figure 1 Shown is a threat processing system based on smart grid information security detection, which mainly includes two parts: the building block of the smart grid framework and the flow graph analysis module, among which:
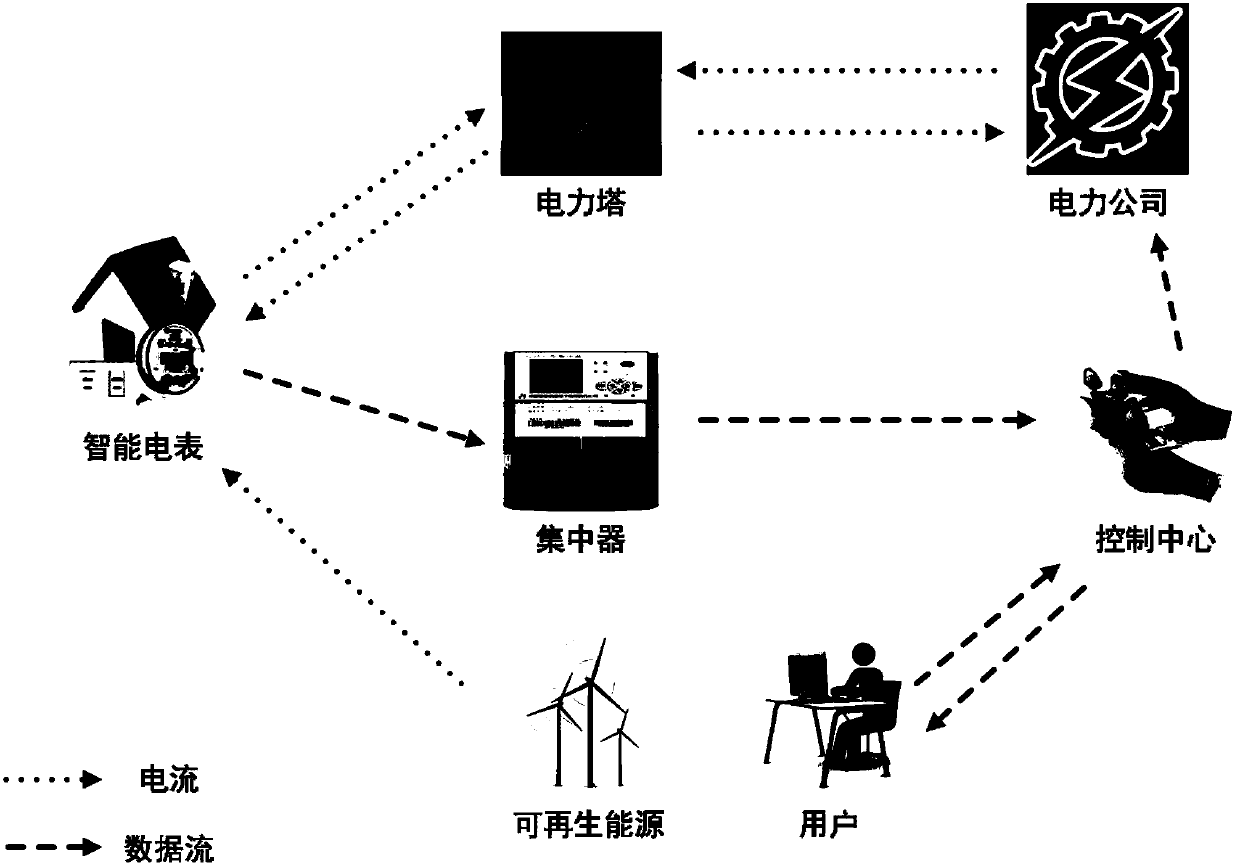
[0027] The building block of the smart grid framework: designed according to the characteristics of the smart grid, it consists of seven parts: smart meters, power towers, power companies, control centers, concentrators, renewable energy and users; smart meters are used to share relevant information with public facilities for monitoring and billing purposes;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com