Method, terminal device and storage medium for detecting malicious code injected when apk is running
A malicious code and memory address technology, the application is injected into the malicious code field when the Android installation package is detected, which can solve the problem of inaccurate detection results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
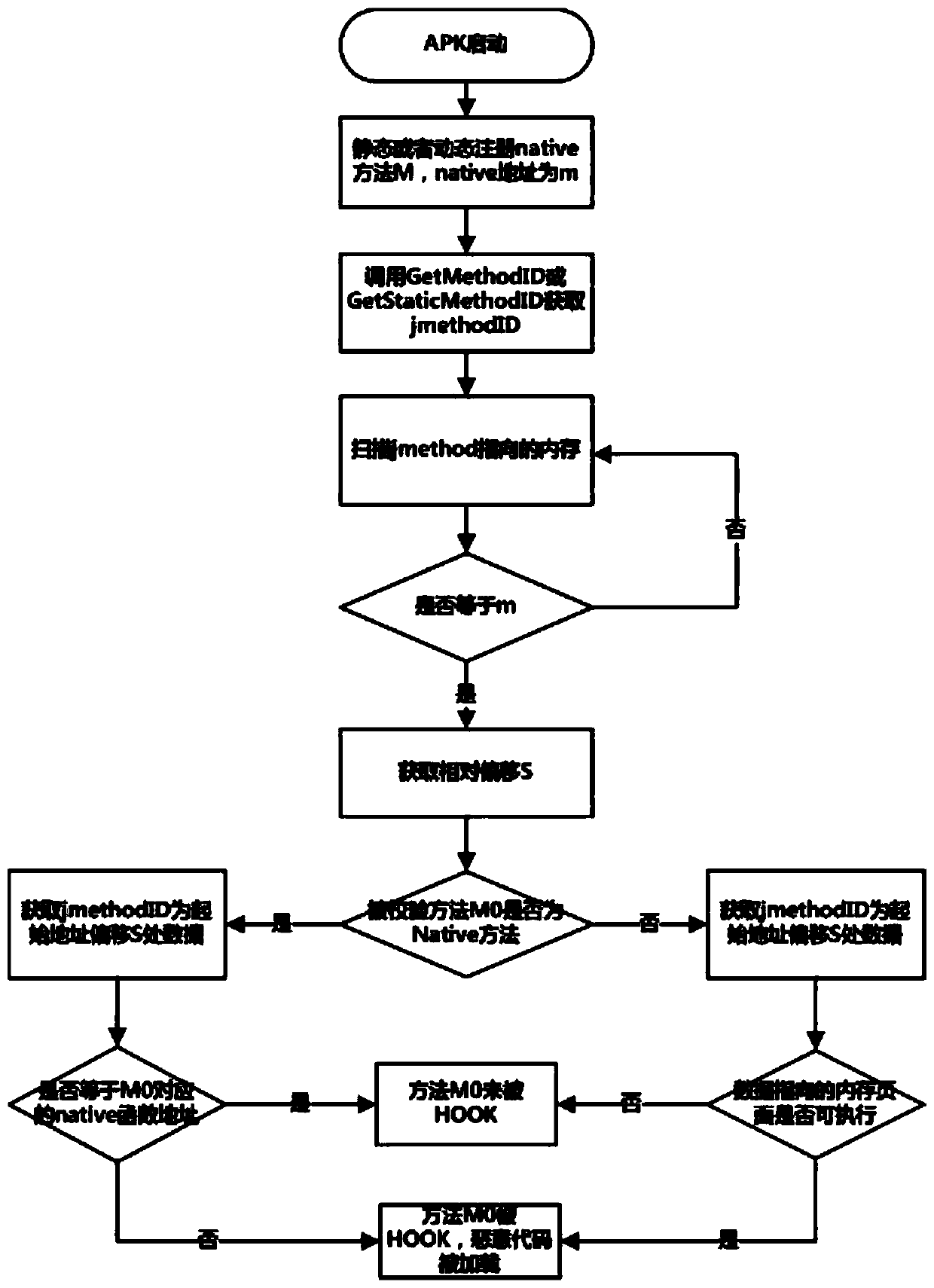
[0030] see figure 1 As shown, the present invention provides a method for detecting malicious code injected into the Android installation package during operation, which can effectively detect whether the APK is injected with malicious code by hook frameworks such as xposed during the running process.
[0031] The concrete process of the method described in the present invention is as follows:
[0032] S1: start the Android installation package (APK), and enter the step S2;
[0033] S2: Generate a native method M through static registration or dynamic registration, whose memory address is m, and enter step S3;
[0034] S3: Obtain the storage start address of M: In the native code of M, by calling the java native interface (jni) function, the jmethodID of the method is obtained, where jmethodID is the storage start address of the corresponding data structure of the method in the java virtual machine , specifically, the java native interface (jni) function to be called is the ...
Embodiment 2
[0044]The present invention also provides a terminal device for detecting malicious code injected into an Android installation package during operation, including a memory, a processor, and a computer program stored in the memory and operable on the processor, and the processor executes The computer program implements the steps in the above-mentioned method embodiments of the embodiments of the present invention, for example figure 1 Method steps for steps shown.
[0045] Further, as an executable solution, the terminal device that detects that malicious code is injected into the Android installation package during operation may be computing devices such as desktop computers, notebooks, palmtop computers, and cloud servers. The terminal device that detects that the Android installation package is injected with malicious code may include, but not limited to, a processor and a memory. Those skilled in the art can understand that the composition and structure of the above-mentio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com