Self-adaptive malicious domain name detection method based on DNS (Domain Name Server) flow
A domain name detection and traffic detection technology, applied in the field of network security, can solve the problems of poor reliability, poor accuracy, and few malicious signs, and achieve the effects of low false alarm rate, high accuracy rate, and low delay.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
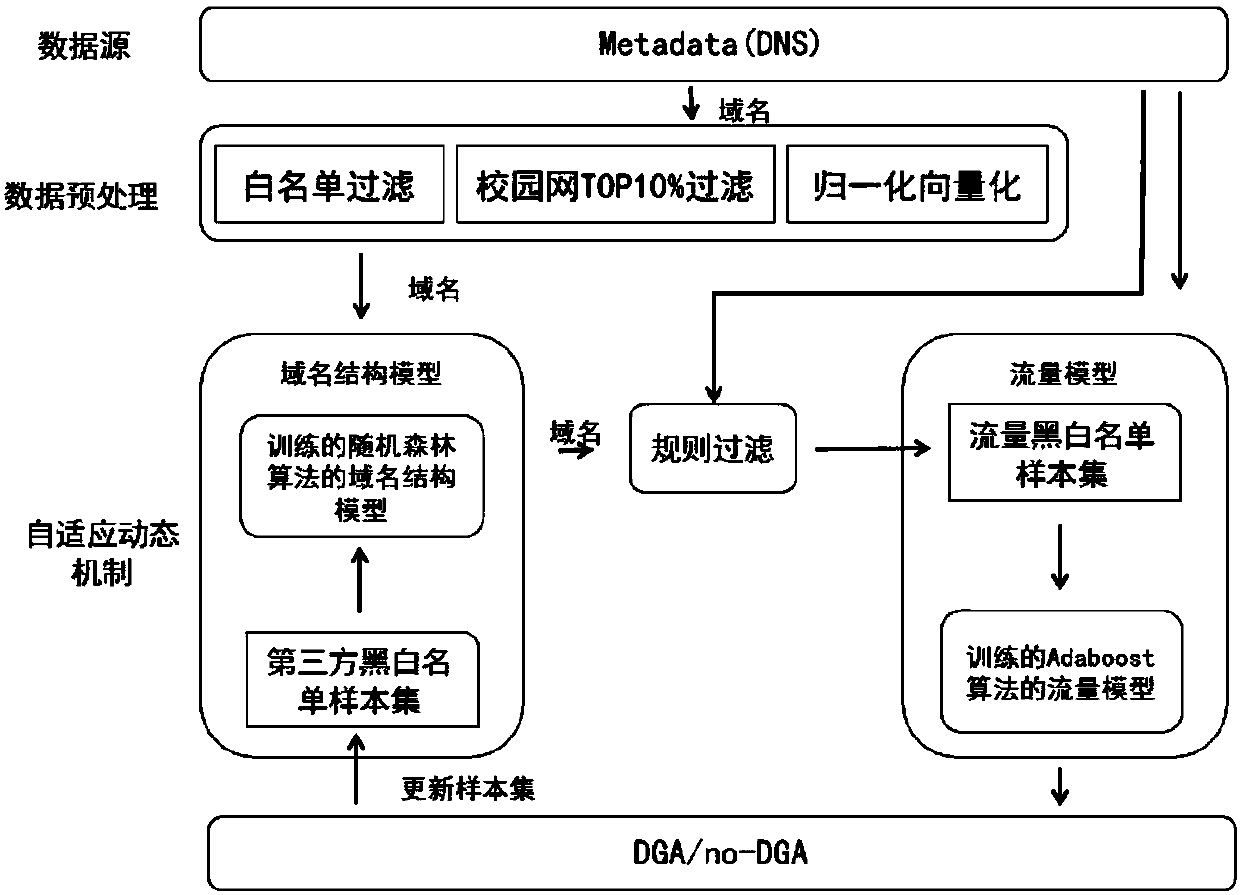
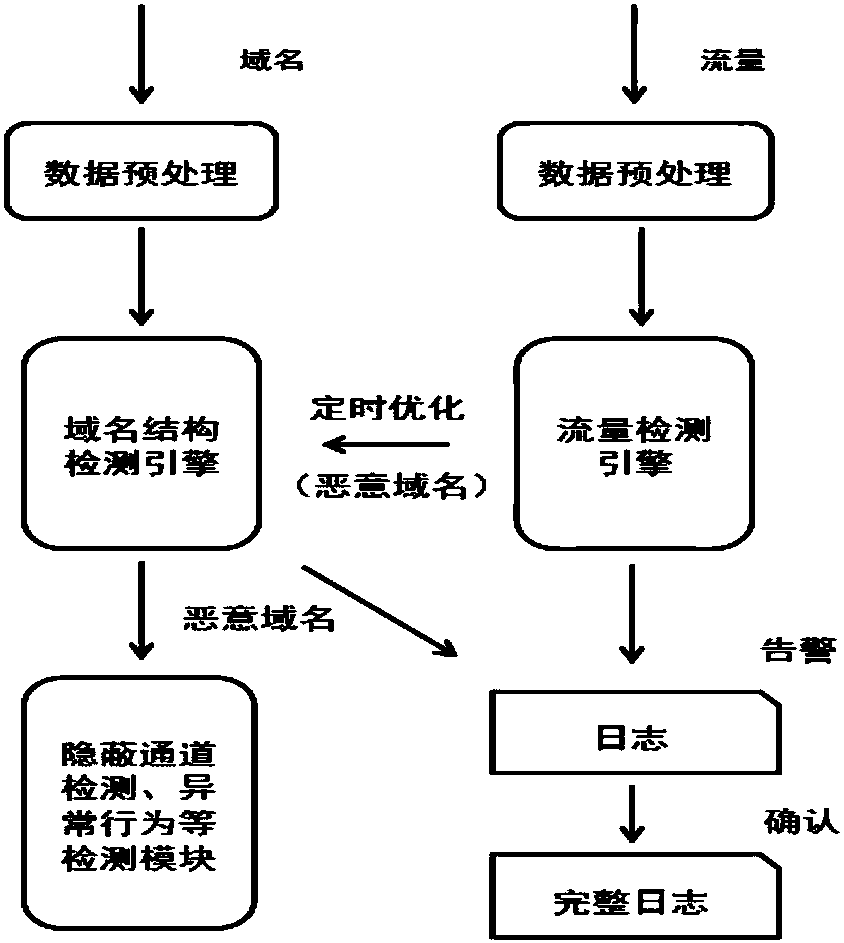
[0061] In the embodiment of the present invention, an adaptive malicious domain name detection method based on DNS traffic, in the implementation process, firstly according to the following figure 1 As shown in the training logic of malicious domain name detection, the initialization of the structure detection engine and traffic detection engine is completed. (Steps 1-4) On this basis, follow figure 2 Realize the adaptive malicious domain name detection mechanism (steps 5-6), which can be divided into the following steps:
[0062] Step 1: Collect the black-and-white list sample set provided by the third-party platform, and use the black-and-white list sample set as the baseline of the training set according to the domain name structure feature list, and select the random forest classifier to train the domain name structure detection model.
[0063] The initialization whitelist is selected from legal domain names provided by Alexa, Webmaster’s Home and other organizations. Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com