Safe and reliable transmission method based on LDPC
A technology of LDPC code and transmission method, which is applied in the field of coding and encryption fusion design based on LDPC code, can solve the problems of large key overhead, low information rate of M public key system, no consideration of disturbed channel, etc., so as to reduce the key Overhead, improve system security, reduce the effect of key overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described in detail below in conjunction with the accompanying drawings.
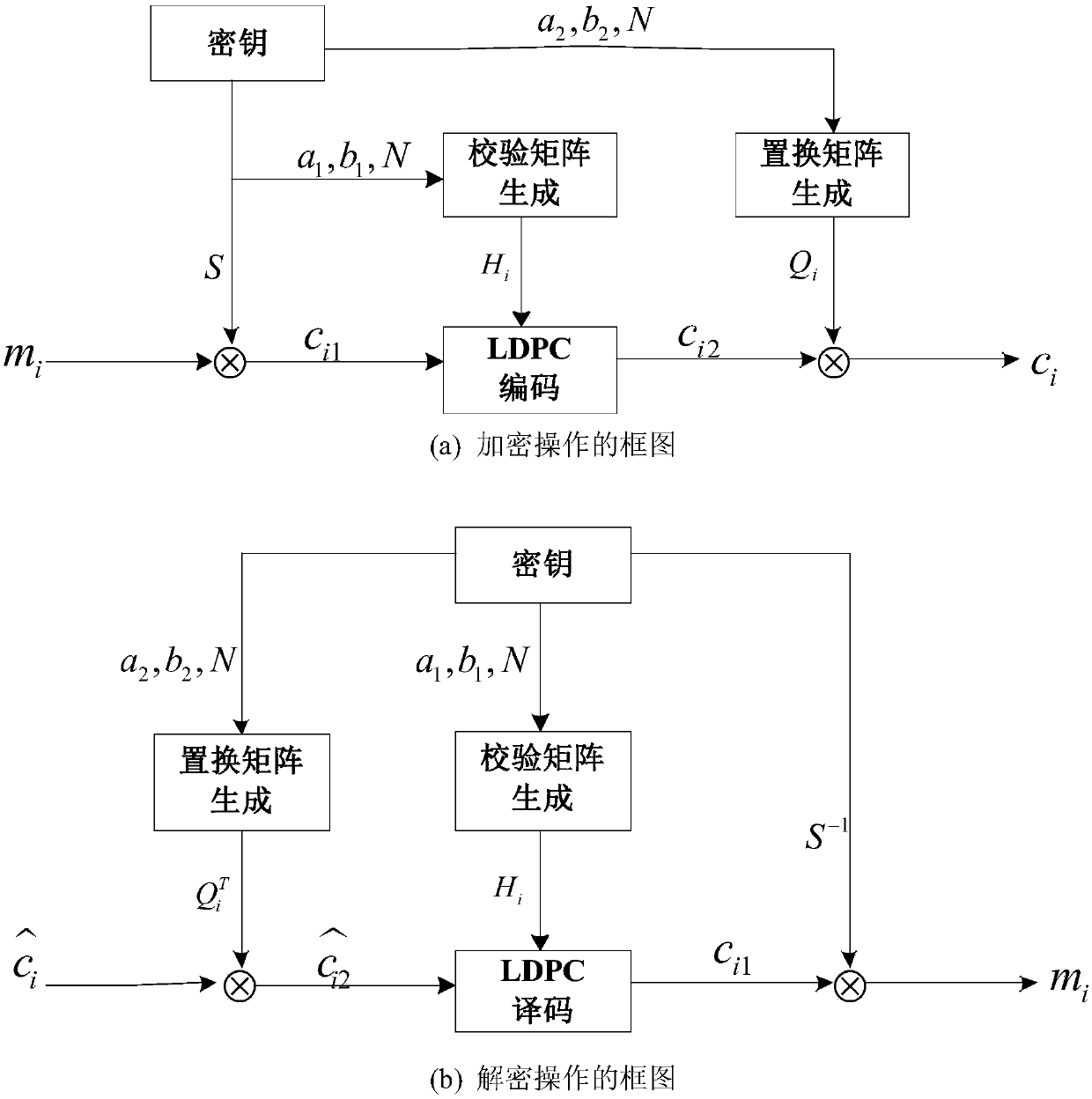
[0038] Set code length n, code rate R=1 / 2, construct LDPC code based on RDF, according to figure 1 As shown in (a), it is assumed that the k-bit plaintext information to be encrypted in this communication is m i , the specific operation of the sender is as follows:
[0039] first step:
[0040] Use k×k order key matrix S for plaintext information m i Encrypt to get c i1 =m i · S, then the sequence c i1 The length of is still k bits;
[0041] Step two:
[0042] The sender of the communication receives the key a 1 , b 1 , N, take them as the parameters of the recurrence formula of the linear congruential generator 1:
[0043] c i+1 =a 1 · c i +b 1 (mod M 1 )i=0,1,2,...,M 1 -1
[0044] where c 0 = N mod M 1 , M 1 =p, p is the block length when constructing the LDPC parity check matrix H based on the RDF method, and the integer sequence c is o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com