Method for enhancing ability of protocol to resist desynchronization attacks
A desynchronization and protocol technology, applied in the computer field, can solve the problems of protocol random number collision domain, ignoring shift and other operations, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below.
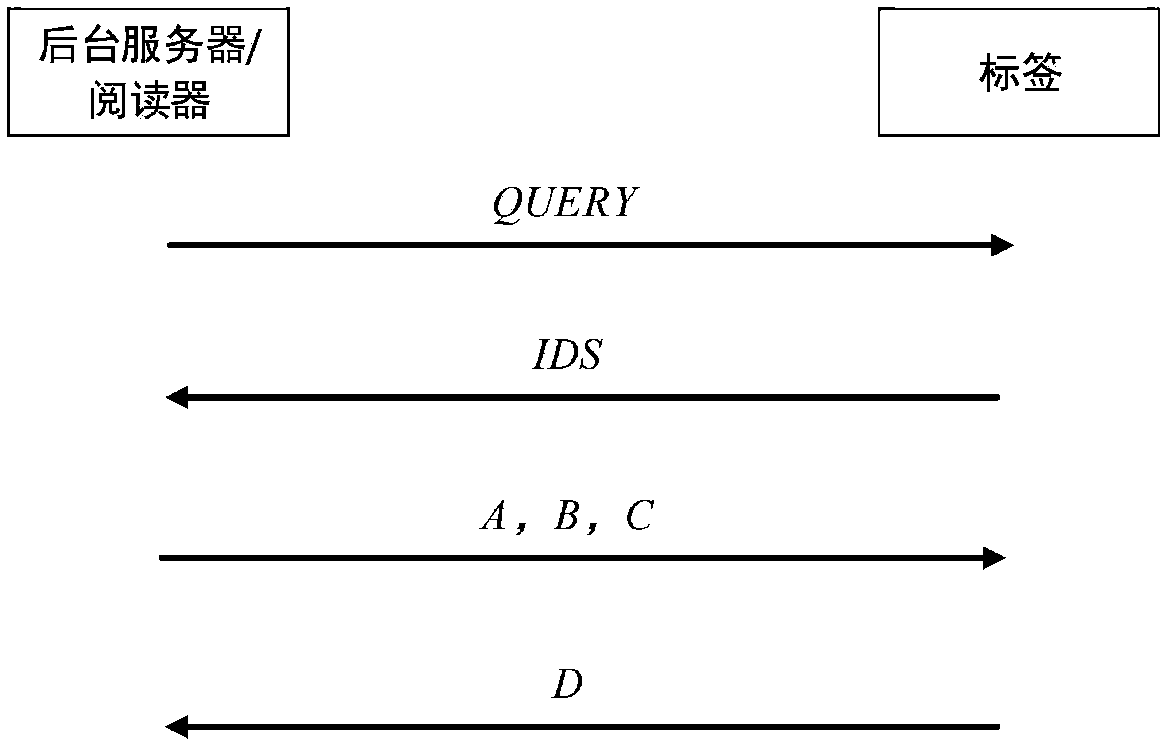
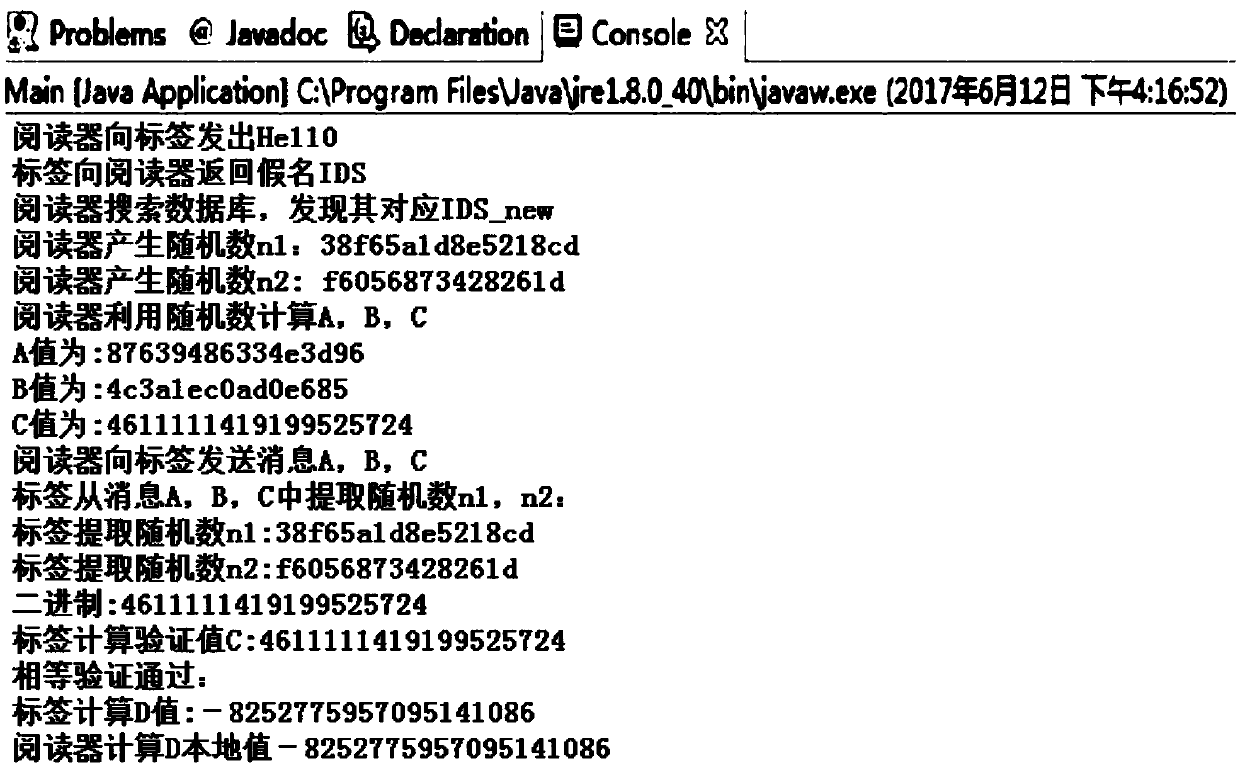
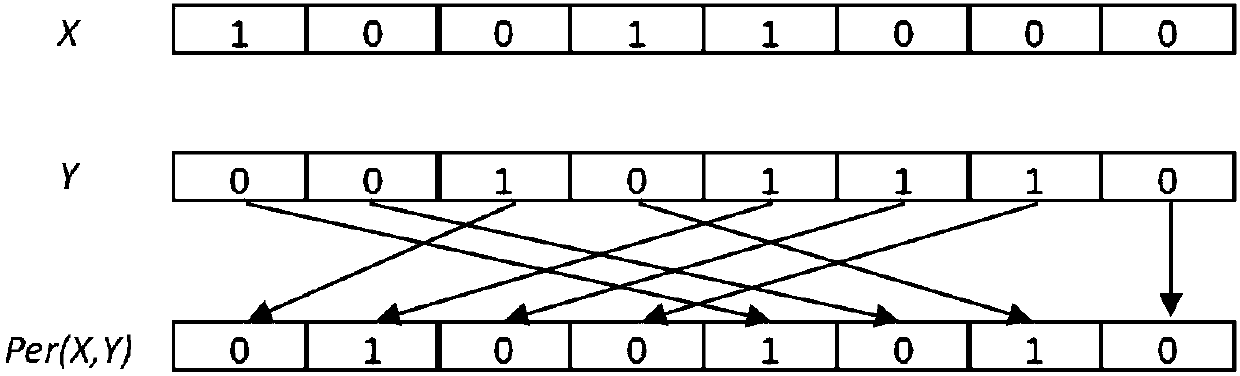
[0030] The ultra-lightweight RFID security protocol is very suitable for the constraints of limited computing power and low cost of tags. In order to ensure the high security of the RFID system under the condition of simple atomic operations, a new type of ultra-lightweight RFID two-way authentication protocol was proposed—— KMAP, the KMAP protocol can resist desynchronization attacks, replay attacks and tracking attacks to a certain extent. In essence, the KMAP protocol introduces a new ultra-lightweight primitive—the pseudo-Kasami code (K c ), which avoids the use of unbalanced logic operations, thereby enhancing the randomness of the protocol message, and making the Hamming weight of the key unpredictable, all of which enhance the security of the KMAP protocol. However, in the desynchronization attack of the KMAP protocol, there are still zero pseudo-Kasami codes, secondary interception, replay attacks, and de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com