Hardware-assisted code-reuse-attack-resistant defence system and method
An attack defense system and code reuse technology, applied in the field of hardware-assisted anti-code reuse attack defense system, can solve the problems of high performance overhead of defense mechanism, security problems, secret key leakage, etc., and achieve low performance overhead and versatility. Good and safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
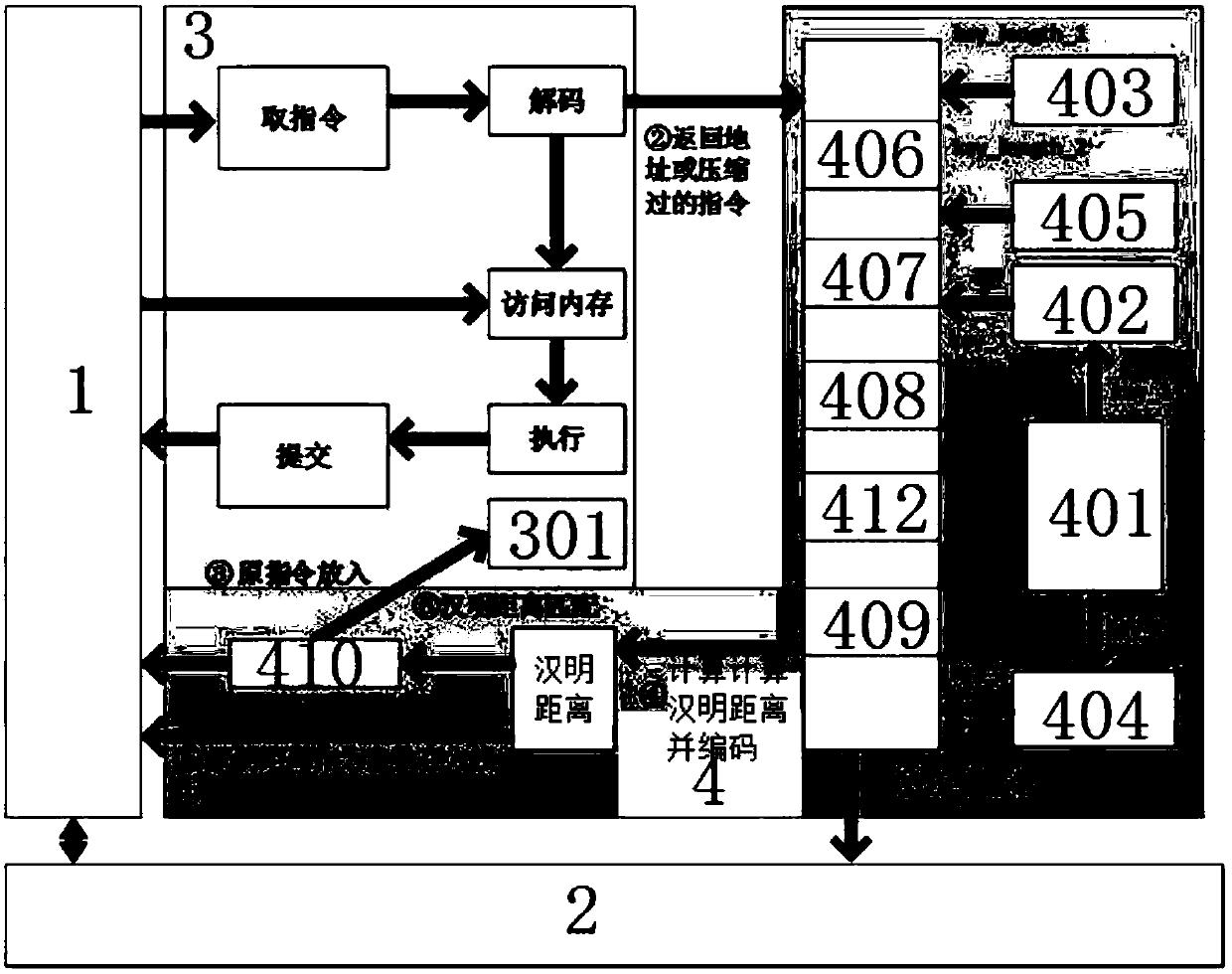
[0048] Such as figure 1 As shown, the hardware-assisted anti-code reuse attack defense system of the present invention includes a preprocessing module, a cache 1, a memory 2, a CPU 3, and an encryption and decryption framework 4, wherein,
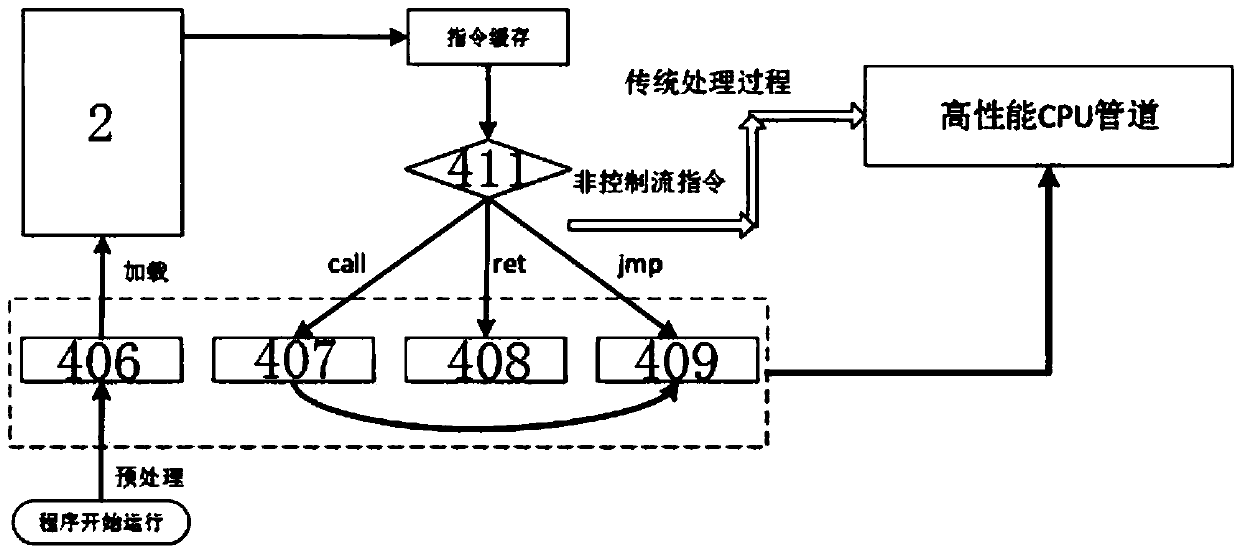
[0049] Preprocessing module: before the program is loaded into the memory 2, the instructions at the destination address of all jmp instructions in the program source code and the instructions at the destination address of all call instructions are transmitted to the encryption and decryption framework 4; Read instructions in;
[0050] Memory 2: Transfer program instructions to cache 1 in real time during program execution;
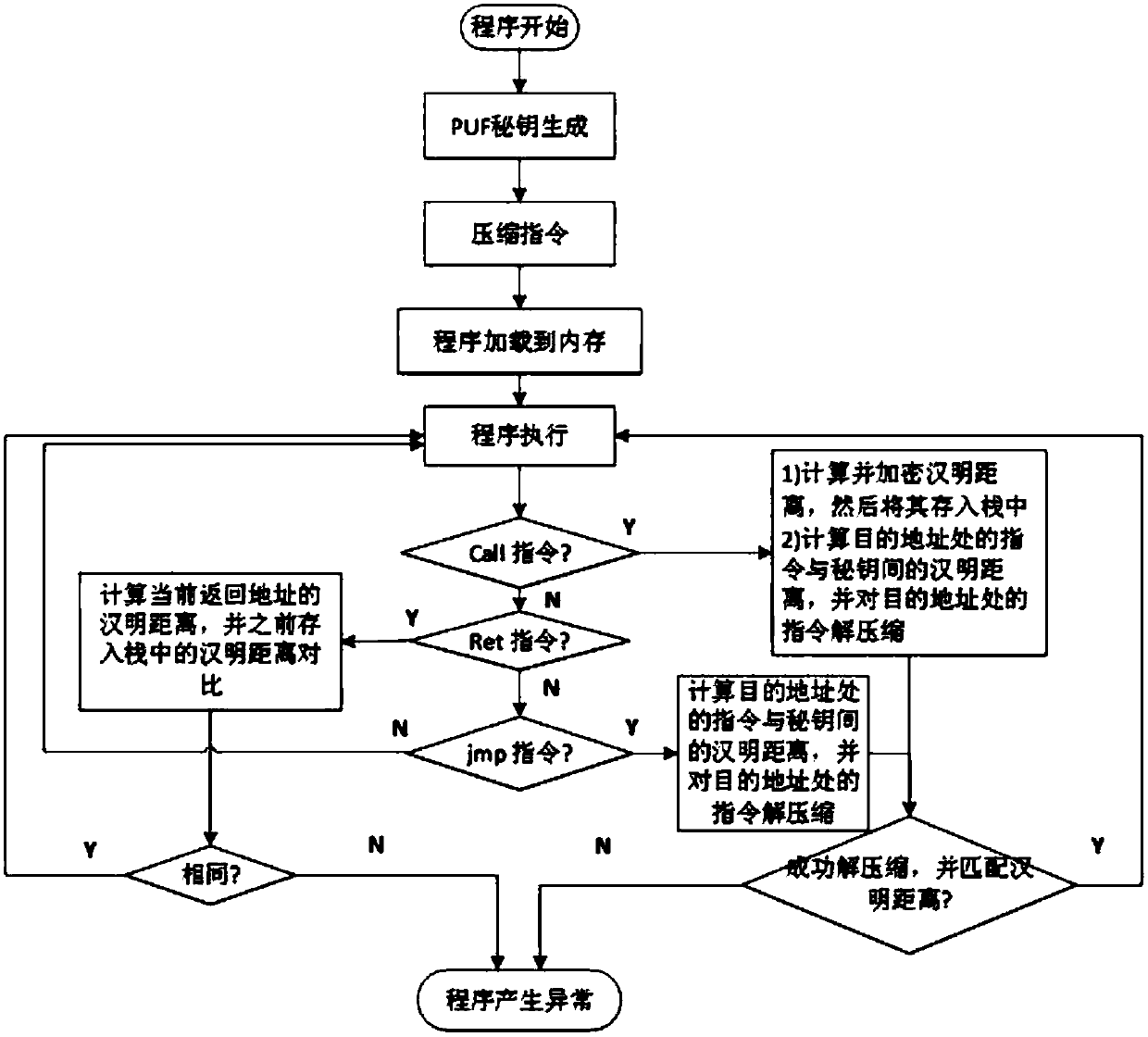
[0051] The encryption and decryption framework 4 performs the following operations before the program is loaded into the memory 2: the first key key_1 and the second key key_2 are generated when the instruction at the destination address of the jmp instruction and the instruction at the destination address of the call...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com