DDoS attack defense method and equipment
A technology with a device and a preset time period, applied in the field of network security, can solve the problems of economic loss of service providers, unsatisfactory protection effect of protection algorithm, and stripping of broiler users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] In order to make the purpose, technical solutions and advantages of the present invention clearer, the following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
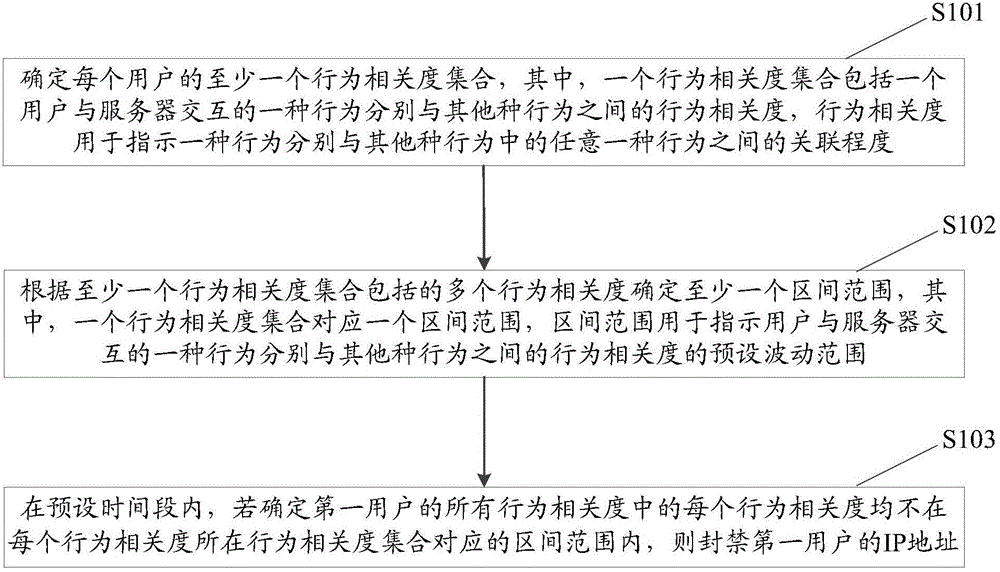
[0067] Due to the certain similarity between the broiler flock and the normal users or the infected normal users, the data packets sent by them are no different from the normal traffic, so that the general defense methods cannot identify the DDoS attack, and thus cannot defend against the DDoS attack in time
[0068] In view of this, the embodiment of the present invention provides a new defense method for DDoS attacks. The defense method determines the behavior correlation between a behavior of a user interacting with the server and other behaviors. If a certain behavior of the user is related If the degree is within the corresponding preset fluctuation range, it can be considere...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com