Image encryption method based on cellular automata and partition compression perception
A block compressive sensing, cellular automaton technology, applied in the field of information security, can solve the problems of unfavorable data transmission, large data volume, and high information redundancy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
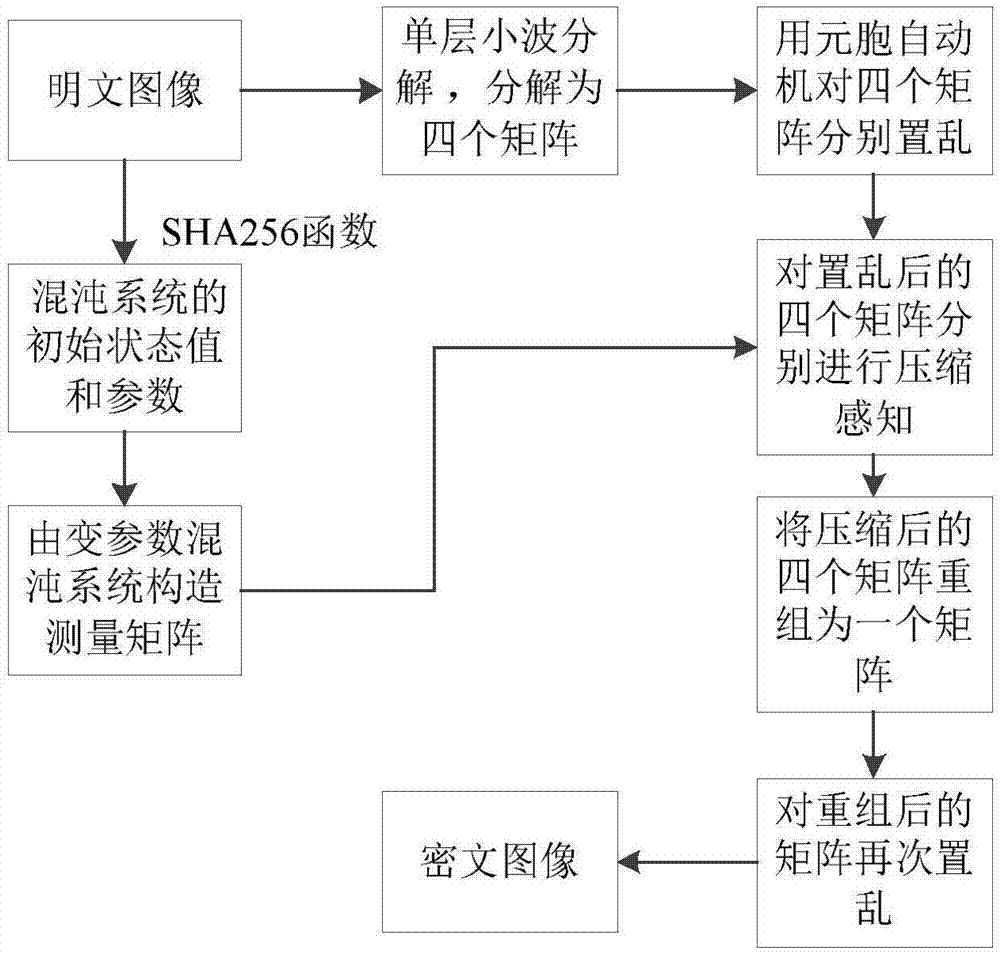
[0072] Embodiment 1. Due to the large amount of image data, high information redundancy, and unfavorable data transmission, etc., in information security image encryption, in order to reduce the amount of network transmission data, the image needs to be compressed for transmission, and the image compression and Encrypted efficient fusion, see figure 1 As shown, an image encryption method based on cellular automata and block compressed sensing is provided, which includes the following content: the plaintext image obtains the initial state value and parameters of the variable parameter chaotic system through the SHA256 function; the plaintext image is decomposed by single-layer wavelet Decompose into three high-frequency component matrices and one low-frequency component matrix, and use elementary cellular automata to scramble the four component matrices; bring the initial state values and parameters of the variable parameter chaotic system into the variable parameter chaotic s...
Embodiment 2
[0073] Embodiment two, see figure 2 As shown, combining the compressed sensing and the cellular automata, using the elementary cellular automata to scramble the image, and compressing and encrypting the image through the compressed sensing, the specific implementation steps are as follows:
[0074] Step 1: Use the SHA256 function to calculate the plaintext image P with a size of M×N, obtain a set of 256-bit hash values and use it as the image key Key, and convert the 256-bit image key Key into 32 decimals number k 1 , k 2 ,...,k 32 , to calculate the initial state value and parameters of the variable parameter chaotic system. The variable parameter chaotic system is composed of a one-dimensional piecewise linear iterative chaotic map (PLCM) and a Logistic chaotic map with good random statistical properties. PLCM is used to generate chaotic sequences. Logistic chaotic map to generate the parameters of PLCM, the expression of PLCM is:
[0075]
[0076] , whose output s...
Embodiment 3
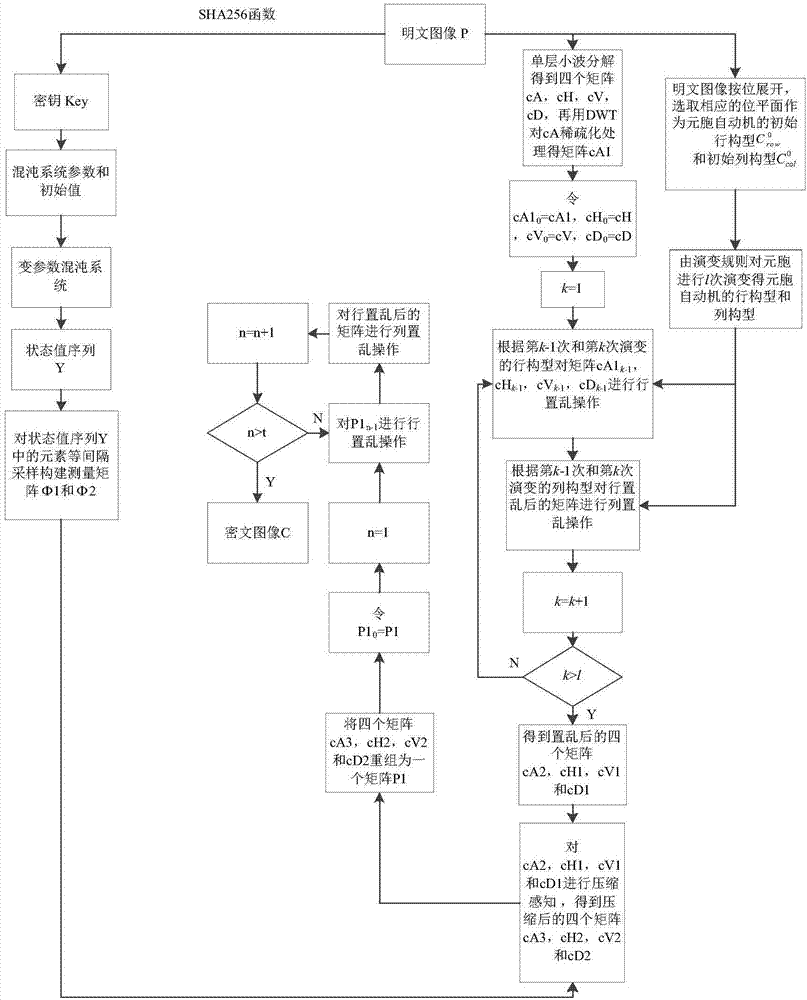
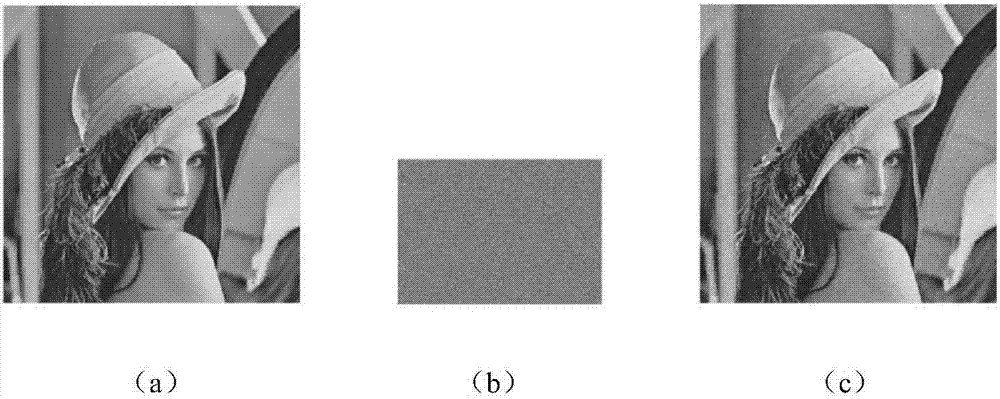
[0125] Embodiment three, see Figure 3-7 As shown, in this embodiment, the programming software used is Matlab R2016b, and the Lena grayscale image with a size of 512×512 is selected as the experimental object. The specific encryption process is as follows:
[0126] Step 1: Input the Lena grayscale image with the original size of 512×512, use P=imread('Lena.bmp') to read the image information, use the SHA256 function to calculate the plaintext image P, and obtain a set of 256-bit hashes Value and use it as the image key Key, and then convert the 256-bit Key to 32 decimal numbers k 1 , k 2 ,...,k 32 , the specific steps used to calculate the initial state value of the variable parameter chaotic system are as follows:
[0127] 1.1) A variable parameter chaotic system is adopted, which is composed of a one-dimensional piecewise linear iterative chaotic map (PLCM) and a Logistic chaotic map with good random statistical properties. The PLCM is used to generate a chaotic sequence...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com