Database access control method and system
An access control and data access technology, applied in the field of data security, can solve the problems of potential safety hazards, the inability of the user rights management system to fuzzy process sensitive data, and the inability to process sensitive information mutations, etc., to achieve advanced architecture, high compatibility, and flexible configuration Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
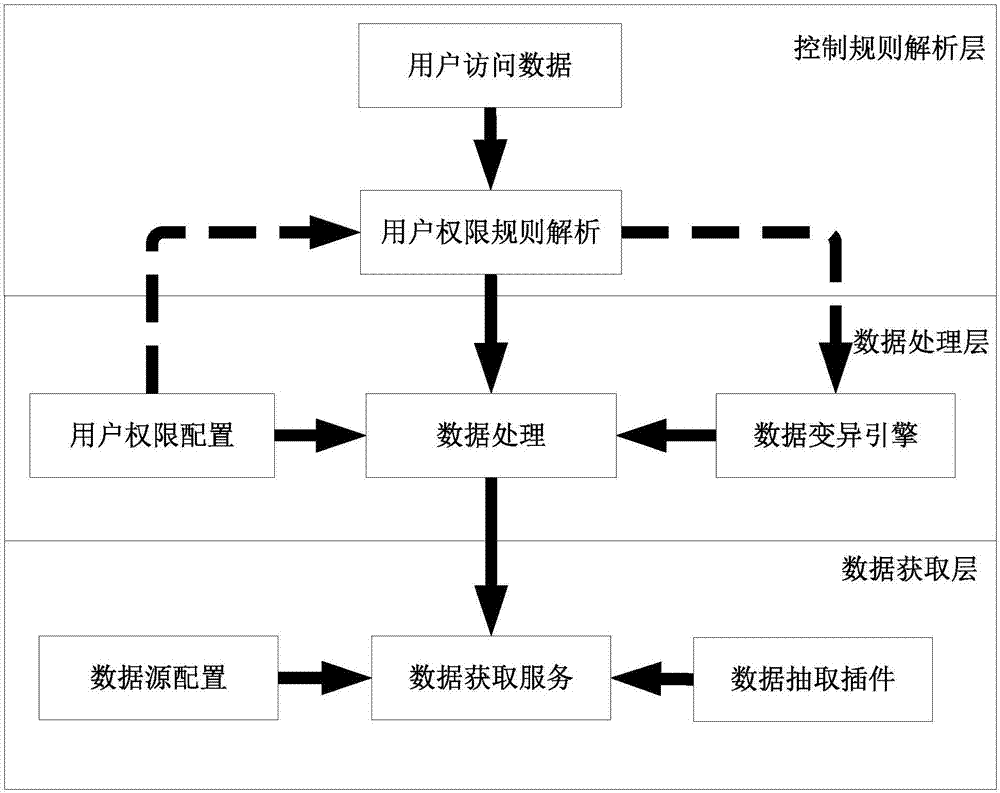
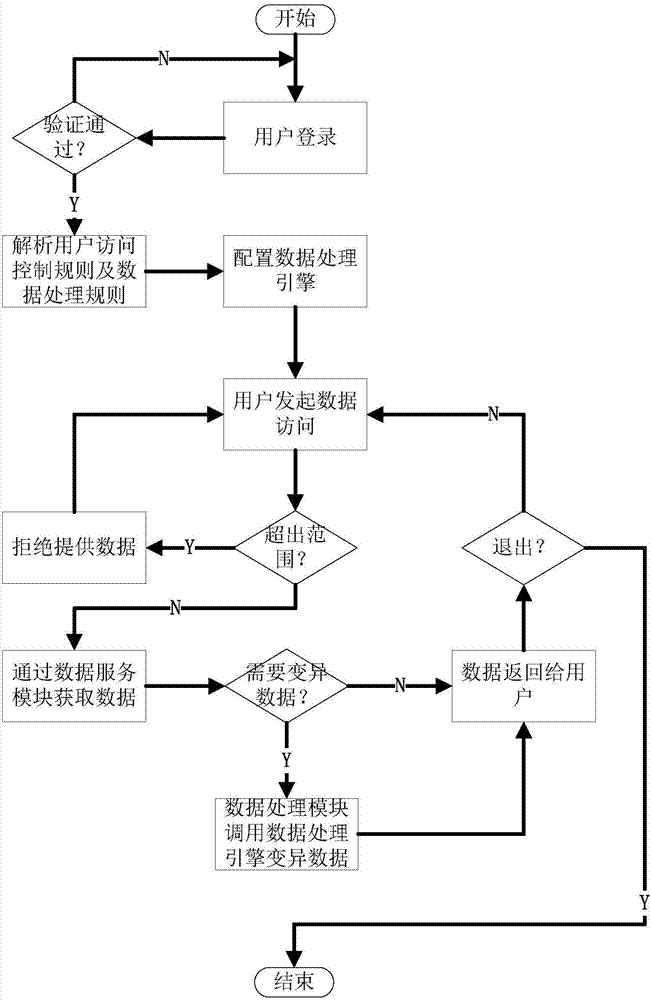
[0074] attached Figure 4 Describes the data processing steps of the company's database desensitization system.
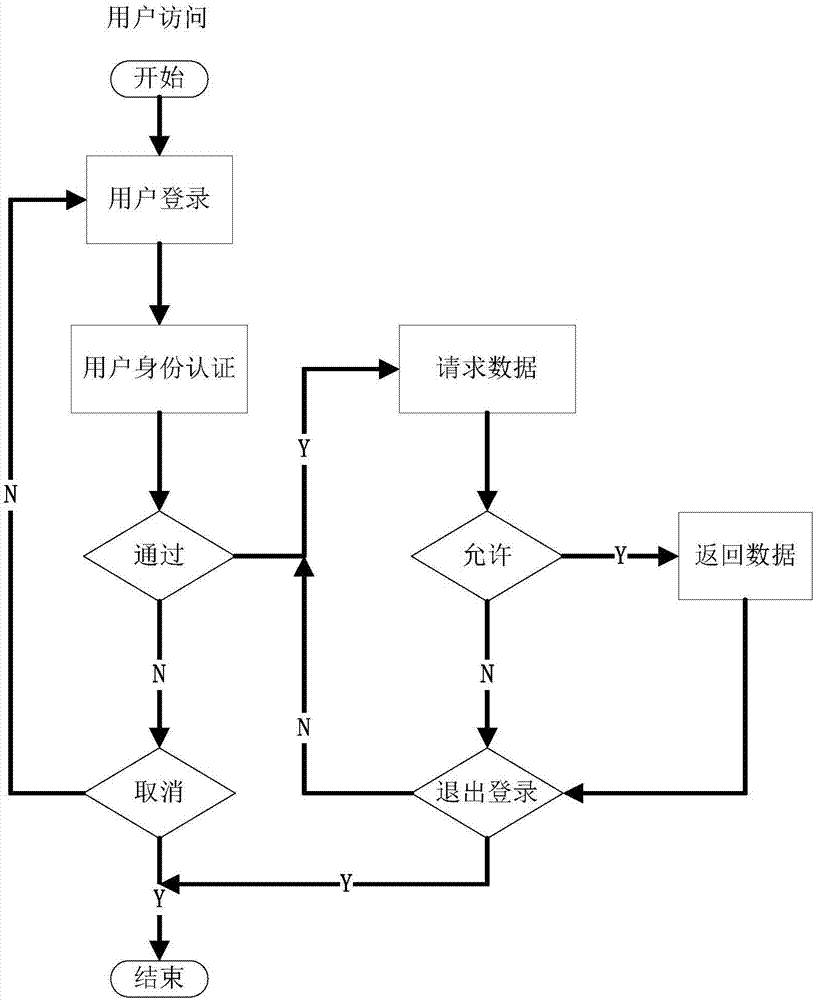
[0075] 1. After logging in to the computer system, log in to the database desensitization system (that is, according to the configured user access and data processing rules, the key information in the obtained data can be blurred and replaced, such as ID number, bank card number, etc.), after the verification is passed Go to step 2 for processing.
[0076] 2. The system analyzes user rights and initializes the data processing engine. After completion, go to step 3 for processing.
[0077] 3. The user accesses the data in the database, and then proceeds to step 4 for processing.
[0078] 4. The system responds to user requests, acquires data, and proceeds to step 5 for processing.
[0079] 5. Based on the configured user access control rules, determine whether content cleaning is required for the acquired data. If necessary, go to step 6 for processing, otherwise...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com