Security trust processing method and device
A technology of a processing device and a processing method, applied in the field of communication, can solve the problems of loss, the collapse of the authentication system, etc., and achieve the effect of solving the problem of insufficient security and safe and reliable Internet services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
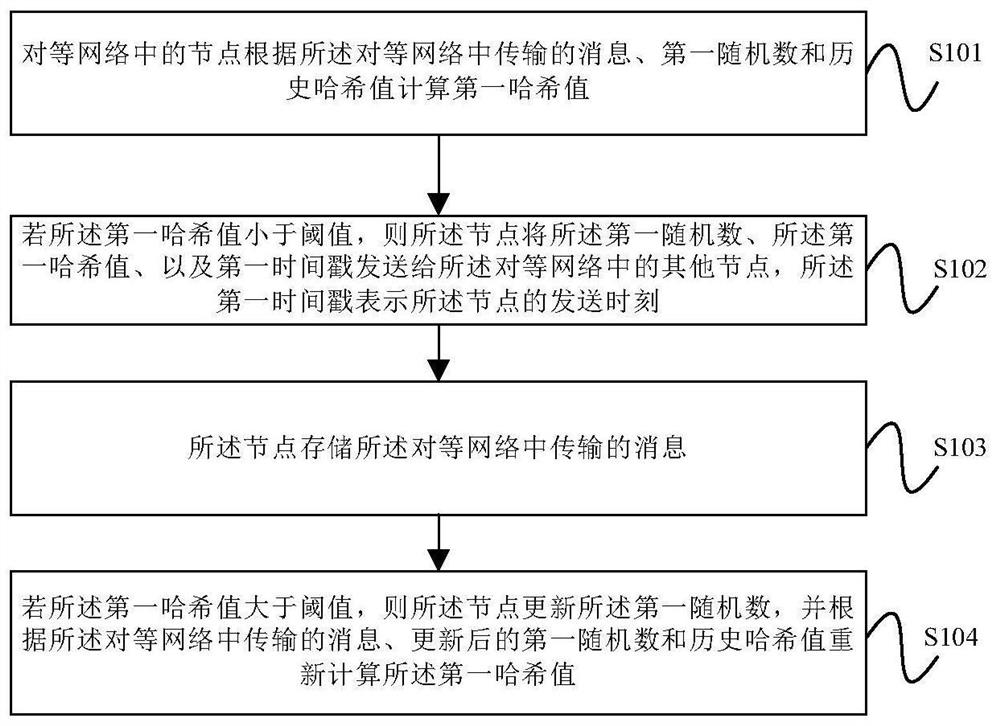
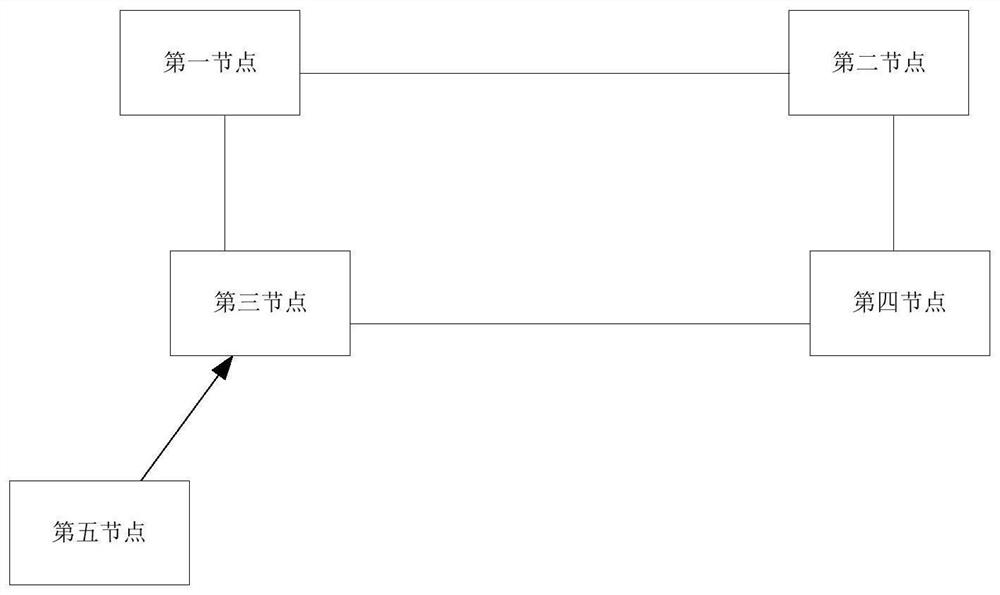
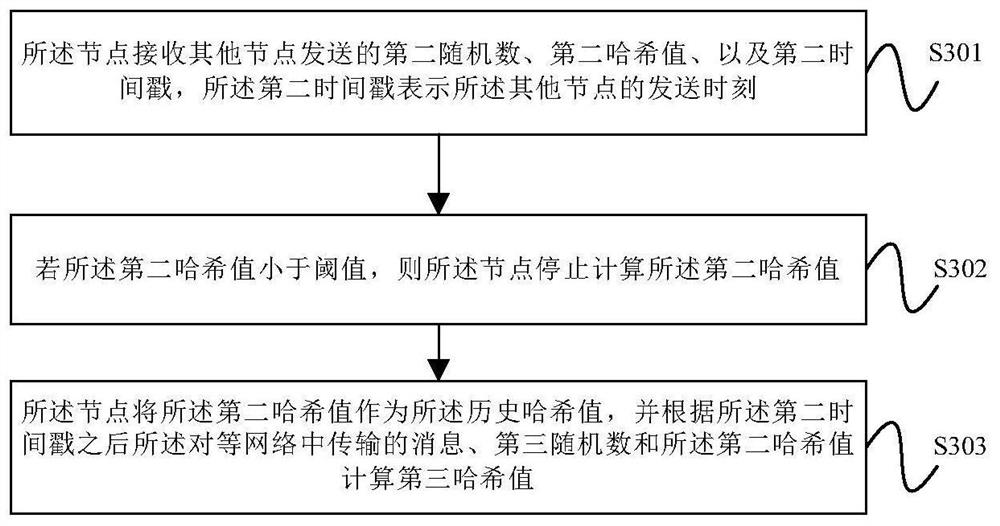
[0022] figure 1 A flowchart of a security trust processing method provided by an embodiment of the present invention; figure 2 A network architecture diagram applicable to the security trust processing method provided by the embodiment of the present invention. The specific security trust processing method steps are as follows:
[0023] Step S101 , nodes in the peer-to-peer network calculate a first hash value according to messages transmitted in the peer-to-peer network, first random numbers and historical hash values.
[0024] Such as figure 2 As shown, the first node, the second node, the third node, and the fourth node form a peer-to-peer network (Peer to Peer, P2P). equal to the number of nodes in the network. Each node is peer-to-peer in the peer-to-peer network, and their respective messages can be synchronized. Specifically, each node can be a user terminal, server, server cluster, and other devices. Each node is installed with an Internet security trust P2P pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com