Safety processing method, device and system for virtual resources
A resource processing and virtual resource technology, applied in secure communication devices, transmission systems, digital transmission systems, etc., can solve problems such as poor security in processing virtual resources, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
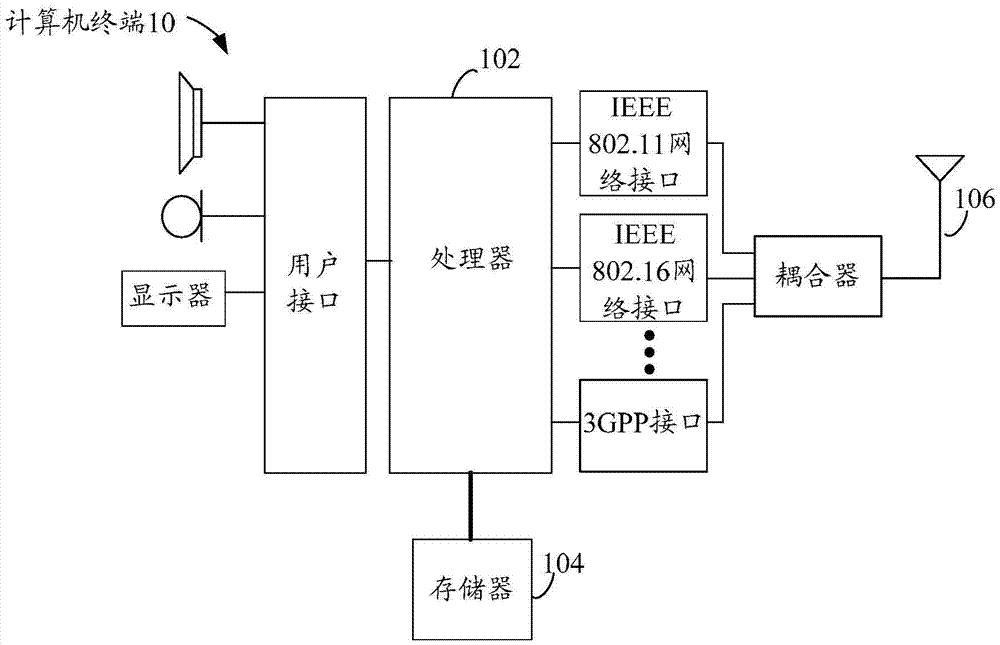
[0027] The method embodiment provided in Embodiment 1 of the present invention may be executed in a mobile terminal, a computer terminal or a similar computing device. Take running on a computer terminal as an example, figure 1 It is a structural block diagram of a computer terminal according to a method for safely processing virtual resources according to an embodiment of the present invention. Such as figure 1 As shown, the computer terminal 10 of the safe processing method for virtual resources may include one or more (only one is shown in the figure) processors 102 (the processors 102 may include but not limited to microprocessor MCU or programmable logic device FPGA, etc. processing means), memory 104 for storing data, and transmission means 106 for communication functions. Those of ordinary skill in the art can understand that, figure 1 The shown structure is only for illustration, and it does not limit the structure of the above-mentioned electronic device. For exam...
Embodiment 2
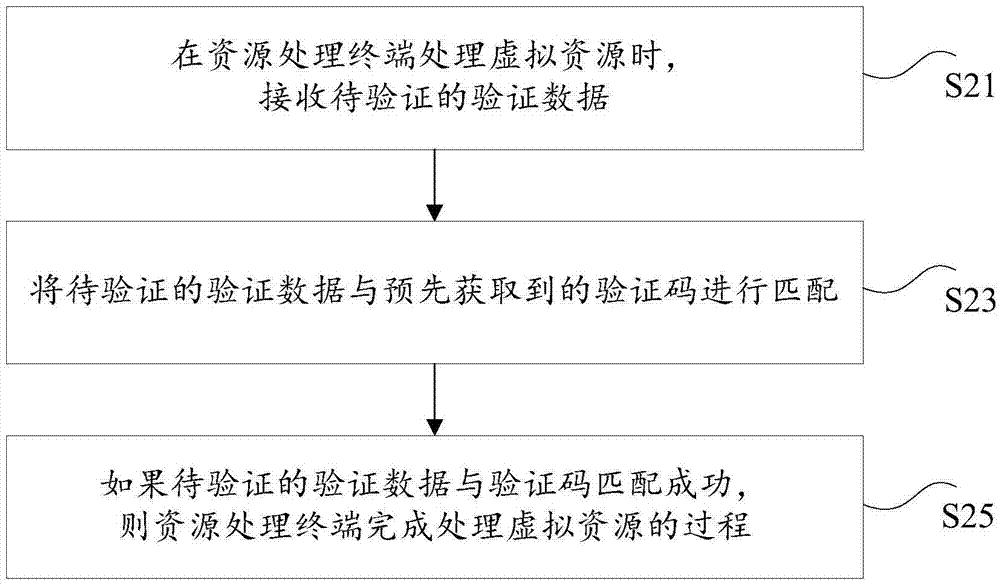
[0102] According to an embodiment of the present invention, a method for safely processing virtual resources is also provided, such as Figure 4 , the method may include:
[0103] Step S41, receiving verification data to be verified when the resource processing terminal processes virtual resources.
[0104] Specifically, the above-mentioned resource processing terminal may be an intelligent terminal such as a mobile phone, an iPad, a tablet computer, etc., the above-mentioned virtual resources may be virtual currency, virtual goods, virtual books, etc., and the above-mentioned verification data to be verified may be a verification password to be verified.
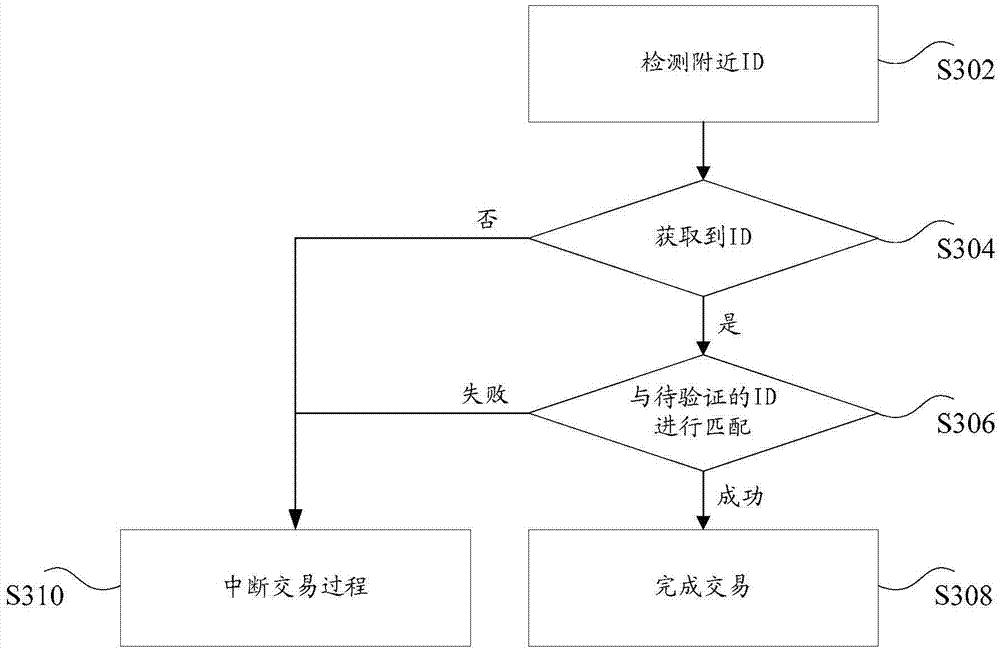
[0105] For example, the above embodiments of the present invention will be described by taking virtual resources as virtual currency, resource processing terminals as mobile phones, and verification data to be verified as verification passwords as examples. When the user uses the mobile phone to conduct virtual currency tr...
Embodiment 3
[0120] According to an embodiment of the present invention, a virtual resource security processing device for implementing the above virtual resource security processing method is also provided, such as Figure 5 As shown, the device includes: a receiving module 51 , a matching module 53 and a processing module 55 .
[0121] Wherein, the receiving module 51 is configured to receive verification data to be verified when the resource processing terminal processes virtual resources.
[0122] Specifically, the above-mentioned resource processing terminal can be smart terminals such as mobile phones, iPads, and tablet computers, and the above-mentioned virtual resources can be virtual currency, virtual goods, virtual books, etc., and the above-mentioned verification data to be verified can be the verification code input by the user. Identification (ID).
[0123] For example, the above embodiments of the present invention will be described by taking virtual resources as virtual cur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com