Wireless communication encryption method based on angular momentums
An encryption method and wireless communication technology, which is applied in the field of wireless communication encryption based on angular momentum, can solve problems such as the difficulty of implementing encryption technology, and achieve the effects of improving security, ensuring security, and realizing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
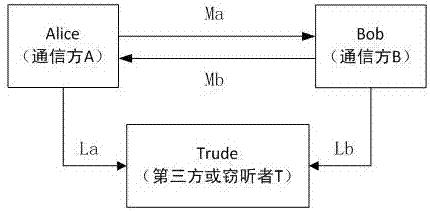
[0043] Such as figure 1As shown, communication party A (assumed to be Alice) and communication party B (assumed to be Bob) are normal communication users, where Alice is the sender of information transmission, Bob is the receiver of information transmission, and is also the expected user, illegal third party T (eavesdropper) is assumed to be Trude. The expected user, eavesdropper and normal communication user may be any device capable of wireless transmission such as a mobile phone, a sensor, or a person or thing using the device.
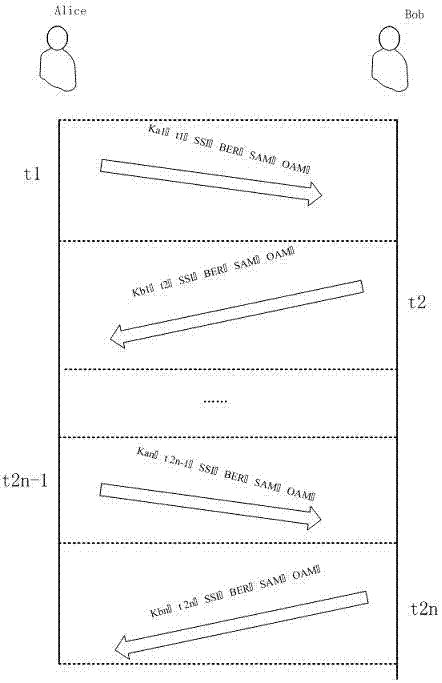
[0044] Such as figure 2 As shown, the complete data transmission includes three stages: the password negotiation phase, the password serial number announcement phase (according to the setting method of the encryption packet sorting rules, this phase may or may not be present) and the encrypted data transmission phase. During the encryption negotiation process, Alice and Bob alternately send cipher packets (that is, data packets containing cipher...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com