A vehicle-mounted t-box and user mobile phone information interaction security authentication system and method
A technology of security authentication and information interaction, which is applied in the field of information security during the communication process between the vehicle T-Box and the corresponding mobile app, which can solve problems such as loss, neglect of information security, and weak information protection, so as to protect information security and avoid dangerous behaviors , the effect of simplifying the design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with accompanying drawing:
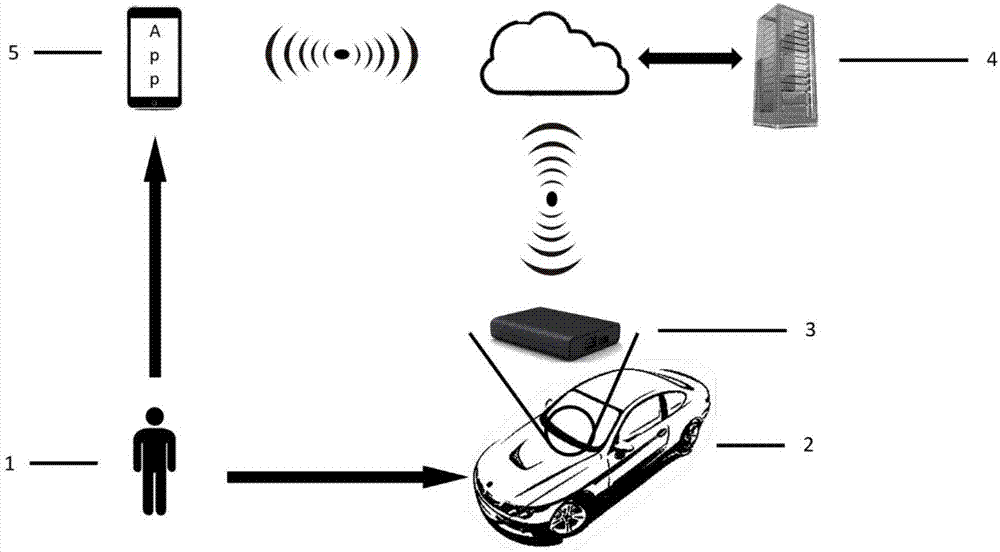
[0026] Such as figure 1 As shown, the present invention provides a new vehicle T-Box architecture system, including: vehicle 2, vehicle T-Box3, T-Box cloud server 4 and mobile terminal App5.
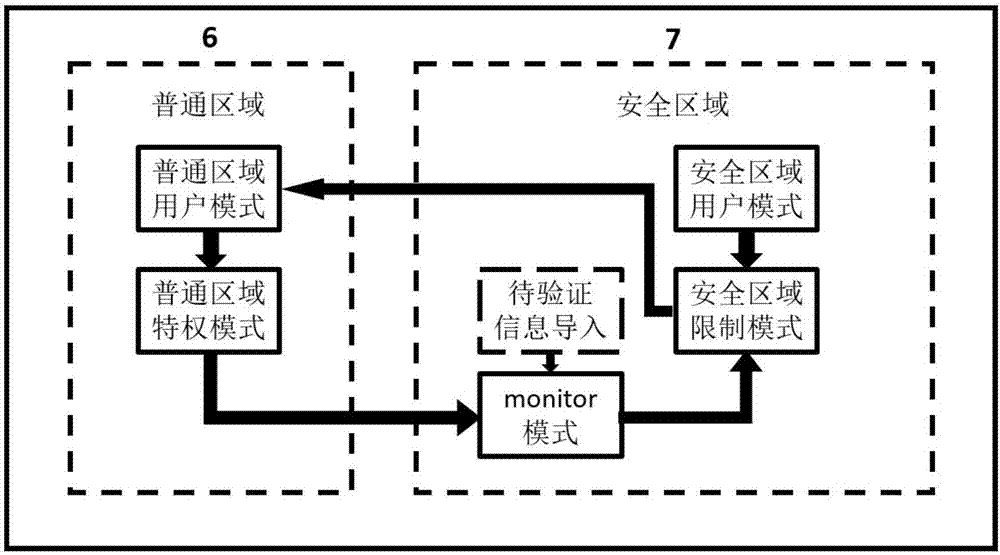
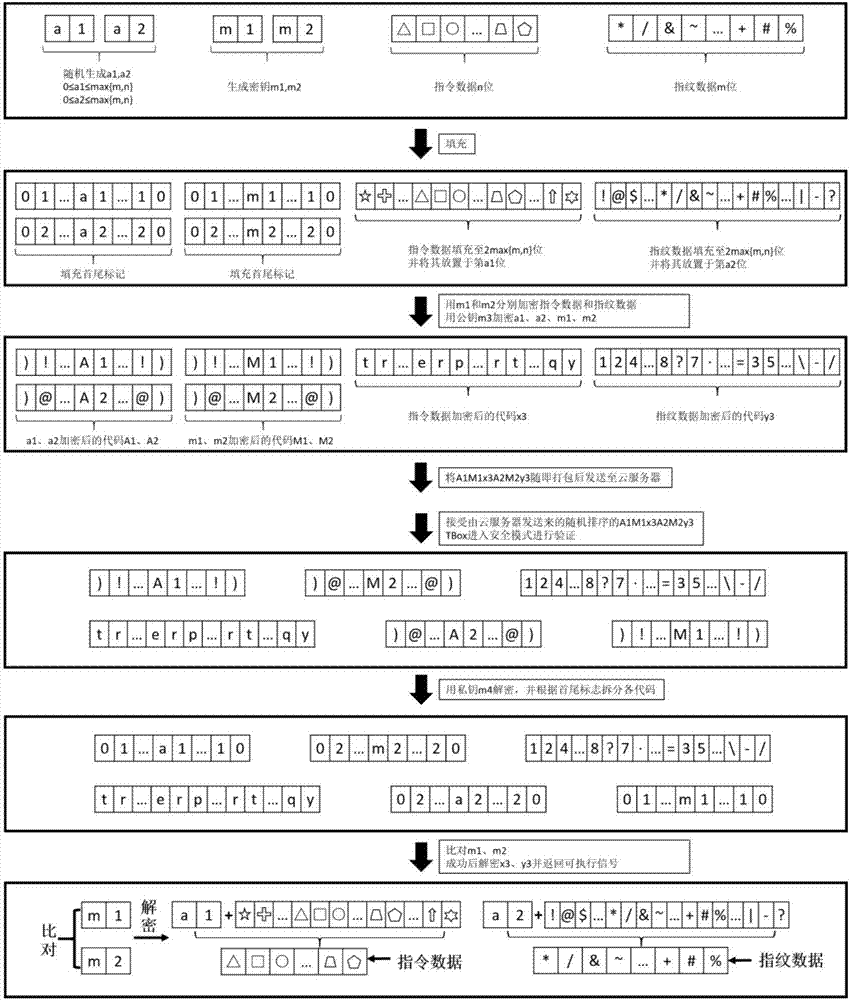
[0027] Among them, the vehicle-mounted T-Box3 has a built-in 4G communication network card for communicating with the T-Box cloud server 4; the vehicle-mounted T-Box3 is connected to the air conditioner and entertainment equipment in the vehicle 2, and as a control terminal, it can send instructions to these devices to Realize the control function; the vehicle T-Box3 is connected with the vehicle computer control system, and communicates through the CAN bus protocol. The automotive computer control system is isolated from the air conditioner and entertainment system at T-Box3. T-Box3 communicates with the two systems using different protocols to prevent information security threats t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com