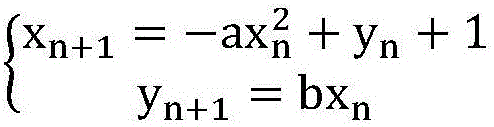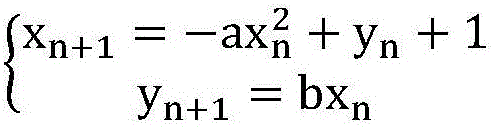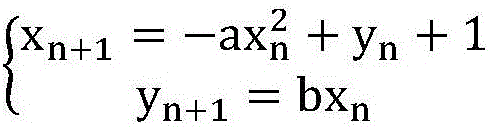Charging pile communication system encryption/decryption method
An encryption, decryption, and communication system technology, which is applied in the field of message encryption and decryption of charging piles, can solve problems such as poor security, weak attack capabilities, and easy interception and cracking. The effect of poor differential attack capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The invention discloses an encryption and decryption method for a charging pile communication system, which includes asymmetric encryption based on a transfer key and symmetric encryption for transferring real-time data. The symmetric encryption method is used to transfer real-time data; the asymmetric encryption method is used for information encryption and decryption. In, the public key and the private key pair are used, and the server sends the public key to the charging pile. The public key encrypts the information, and the charging pile saves the private key required for decryption and passes the private key. The key decrypts the information encrypted by the public key, the public key cannot infer the private key; the asymmetric encryption method uses the improved RSA algorithm to transfer the key.
[0021] The asymmetric encryption method uses a "public key" and a "private key" pair in the encryption and decryption of information. In the present invention, the server ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com