Cloud platform malicious behavior detecting system and method
A detection method and cloud platform technology, applied in transmission systems, electrical components, etc., can solve the problems of false positives and false negatives of detection systems or methods, the ability to limit malicious behavior identification, and the limited computing power and storage capacity of client systems. , to achieve the effect of reliable identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] Below in conjunction with accompanying drawing and embodiment describe in detail:
[0058] 1. System
[0059] 1. Overall
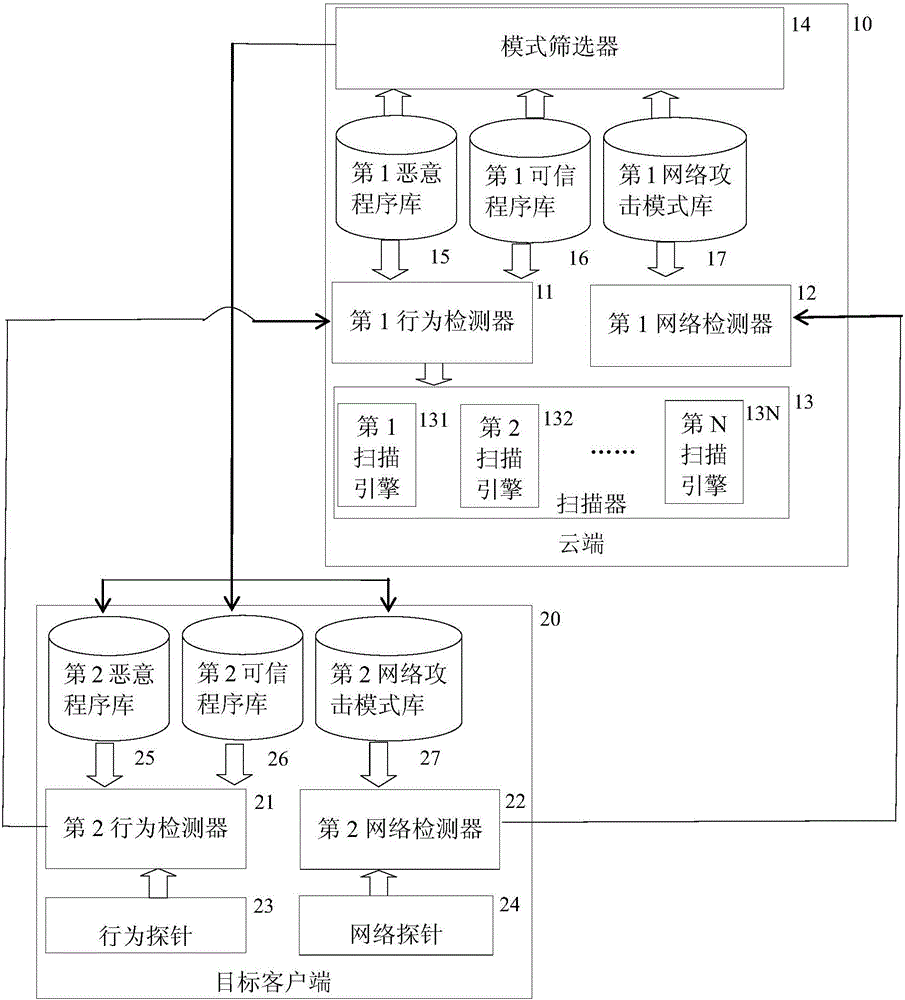
[0060] Such as figure 1 , the system includes a cloud 10 and a target client 20; wherein the cloud 10 includes a first behavior detector 11, a first network detector 12, a scanner 13, a pattern filter 14, a first malicious program library 15, a first trusted Program library 16 and the first network attack mode library 17; Wherein target client 20 comprises the 2nd behavior detector 21, the 2nd network detector 22, behavior probe 23, network probe 24, the 2nd malicious program library 25, the 2nd 2 trusted program library 26 and the second network attack pattern library 27;
[0061] Its interaction relationship is:
[0062] The second behavior detector 21 interacts with the behavior probe 23, the second malicious program library 25, the second trusted program library 26 and the first behavior detector 11 respectively, so as to realize the extract...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com