Android-based Handler memory leakage prevention device and method
A memory leak and message technology, applied in the field of Android system security, can solve problems such as application crashes and system freezes, and achieve the effect of improving efficiency and eliminating memory leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
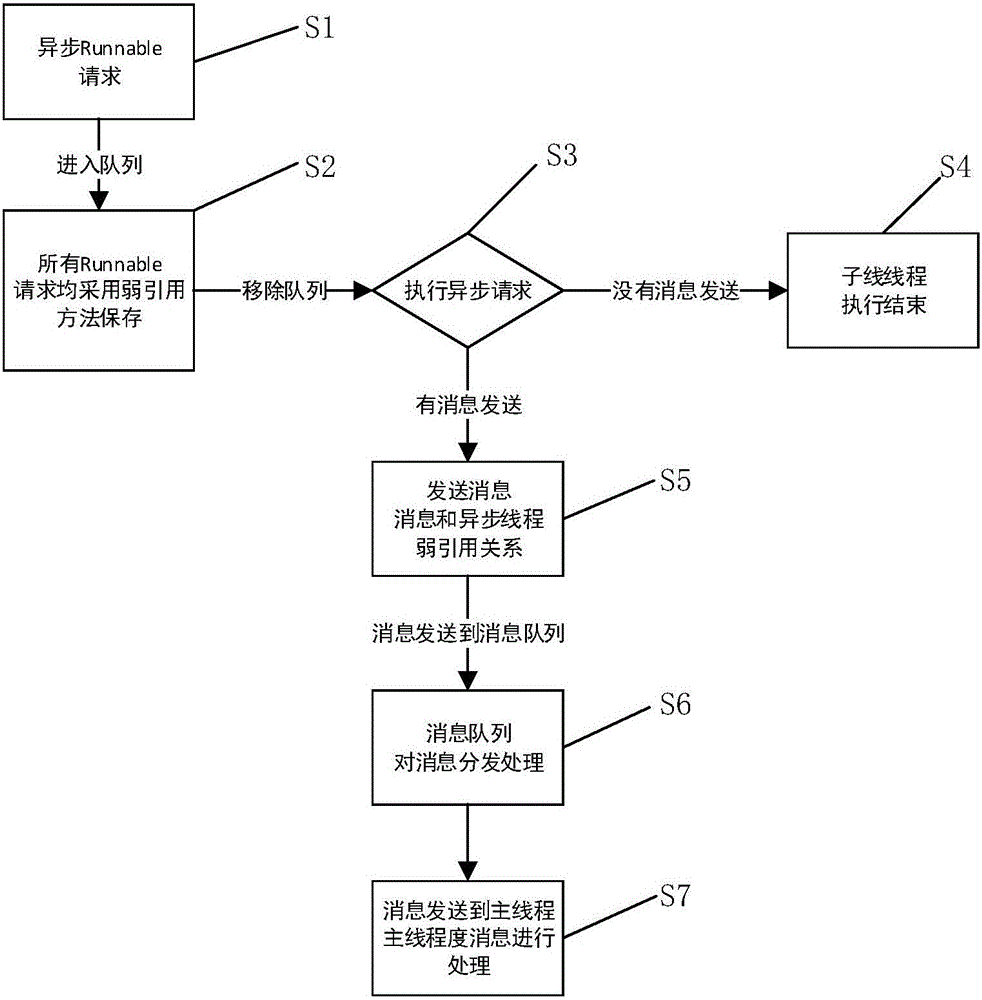
[0050] This embodiment provides an Android-based Handler memory leak prevention device, which includes: an asynchronous Runnable request receiving module, configured to receive a Runnable request of an asynchronous task. The synchronization module is used to store all received Runnable requests of asynchronous tasks synchronously by using the weak reference method. The asynchronous request execution module is used to execute the Runnable request of the asynchronous task, and judges whether there is a message to be sent; the sub-thread execution end module is used to end the sub-thread when there is no message to send. The message sending module is used for sending a message and the weak reference relationship between the message and the asynchronous thread when there is a message to be sent. The message distribution module is used to store the message and the weak reference relationship between the message and the asynchronous thread, and send the message to the main thread fo...
Embodiment 2
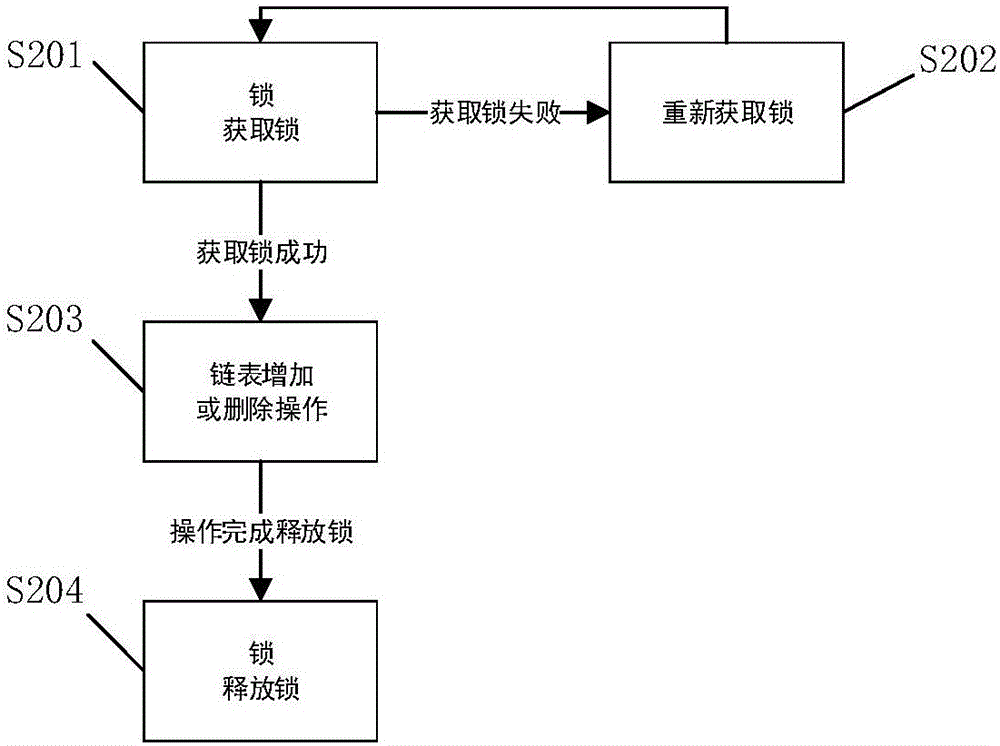
[0067] In this embodiment, on the basis of the first embodiment, the device: a doubly linked list is set in the synchronization module to store the Runnable request of the asynchronous task. Method: Store the Runnable request of the asynchronous task in the form of a doubly linked list.
[0068] Each data node of the doubly linked list contains a reference relationship prior to the previous node and a reference relationship next to the next node. Only the first node and the last node will have something special. The prior of the first node is empty because the first node has no previous node. The next of the last node is empty, because the last node has no following node data. All other nodes are saved with prior and next information. The main reason for using a doubly linked list to store all asynchronous tasks is the unique feature of the doubly linked list, which can quickly delete and add data. It is also because of this feature that we chose a doubly linked list fo...
Embodiment 3
[0070] In this embodiment, on the basis of Embodiment 1 or 2, the device: the priority of the thread is also stored in the synchronization module, which is used to remove the Runnable request of the asynchronous task according to the priority. Method: After storing the Runnable request of the asynchronous task, remove the Runnable request of the asynchronous task according to the priority. Such high-priority tasks can be prioritized. After grading, it can guarantee the priority scheduling of urgent tasks.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com