Software vulnerability discovery method and system
A software vulnerability and discovery method technology, applied in the field of network security, can solve the problems of easy omission of manual processing, large workload of software vulnerability identification, hidden dangers of enterprise network security, etc., to save workload, speed up processing, and avoid harm. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] like figure 1 As shown, a method for discovering software vulnerabilities includes the following steps:
[0026] 101. Preset vulnerability information database. The vulnerability information database is used to store vulnerability information records. Each vulnerability information record includes the name of the vulnerability, the name and software version of the software affected by the vulnerability, and whether it is a new vulnerability. The vulnerability information is executed once a day. Crawling bots to update the vulnerability repository.
[0027] 102. Regularly query whether there are new vulnerabilities in the vulnerability information database, and if so, perform step 103;
[0028] 103. Obtain vulnerability-related software information in the vulnerability information base according to the new vulnerability, where the vulnerability-related software information includes the name and software version of the software affected by the new vulnerability.
[0029...
Embodiment 2
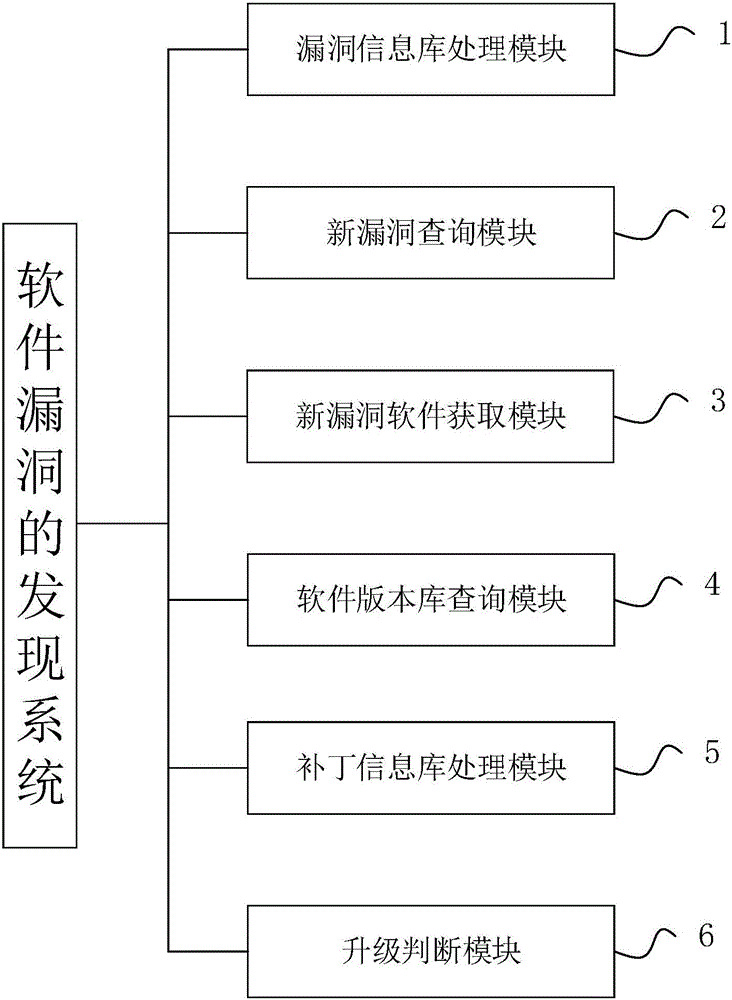
[0037] like figure 2 As shown, a software vulnerability discovery system includes a vulnerability information database processing module 1, a new vulnerability query module 2, a new vulnerability software acquisition module 3, a software version database query module 4, a patch information database processing module 5 and an upgrade judgment module 6 .
[0038] Wherein, the vulnerability information database processing module 1 is used to preset the vulnerability information database, and the vulnerability information database is used to store vulnerability information records, and each vulnerability information record includes the name of the vulnerability, the name and software version of the software affected by the vulnerability, and whether it is New vulnerability. The vulnerability information database processing module 1 updates the vulnerability information database once a day.
[0039] The new vulnerability query module 2 is used to periodically query whether there...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com