Method for implementing distributed architecture through soft routing
A distributed architecture and routing technology, applied in the computer field, achieves the effects of reduced complexity, improved efficiency, fast distribution and distributed business processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
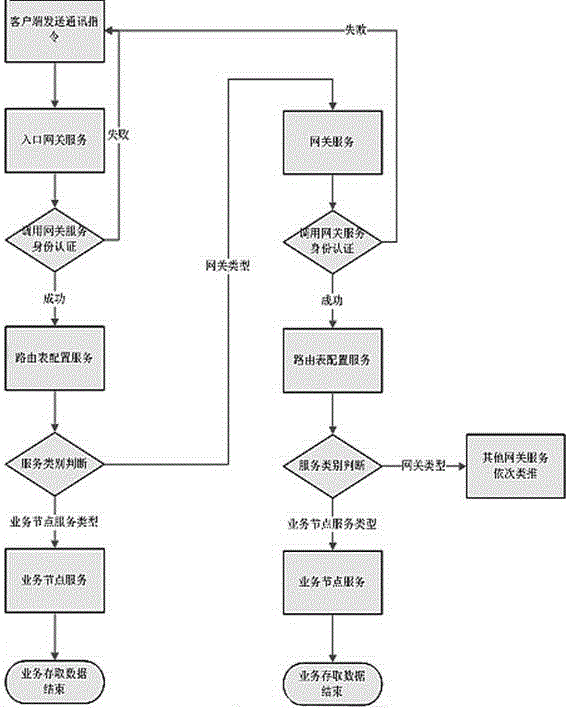
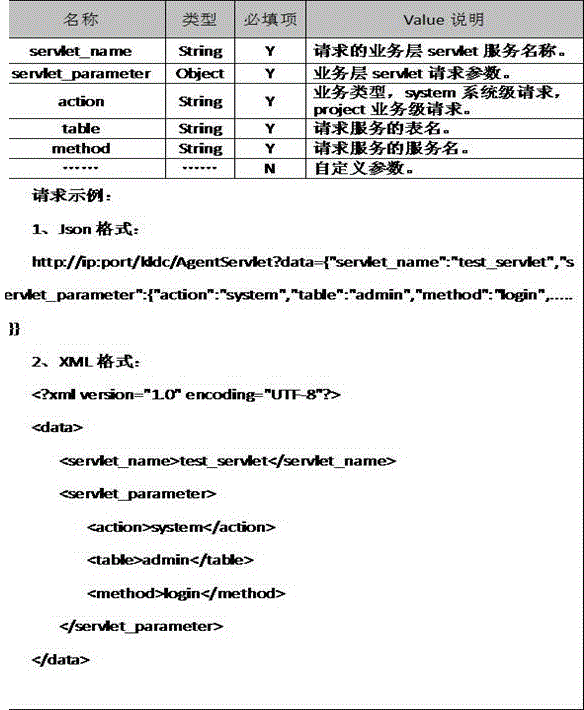
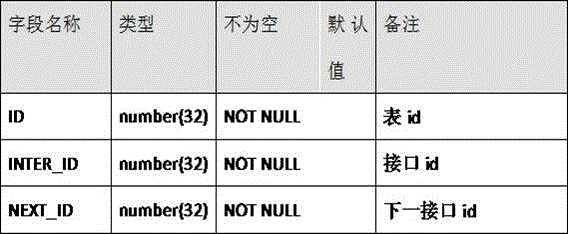
[0043] A method for implementing a distributed architecture with soft routing; the problem to be solved by the present invention is: use this technology to reduce deployment costs, reduce deployment complexity and reusability, etc., realize a reliable distributed architecture, and manage and distribute through the soft routing method Resources, to achieve the effect of the distributed architecture of the hybrid server; establish a safe access method to protect the security of internal services, only allowing the gateway to be accessed directly, and the internal node service is intelligently authorized to access safely; it is completed by the following steps: the client will communicate The command is sent to the ingress gateway, and the ingress gateway calls the gateway service for identity authentication. If the identity authentication succeeds, it will enter the routing table configuration service. If the identity authentication fails, it will return to the client. Fetch data...
Embodiment 2
[0045] In the field of public security security, Internet cloud computing is used to protect internal services through gateways, so that core services are not detected by external systems, thereby protecting the security of services. For example, in the public security inspection system, we use this service to It provides reliable and correct services for legitimate users at the same time.
Embodiment 3
[0047]In the field of operator's SMS interface service, the internal service mechanism is established by connecting the operator's SMS interface service, and the service routing is performed by the gateway to provide SMS sending and management services for authorized users.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com