Method and device for detecting malicious address in attack based on DDOS
A kind of address and malicious technology, applied in the field of network security, can solve the problems of normal user influence, multi-resource consumption, increase the difficulty of protocol stack analysis, etc., and achieve the effect of simple operation and strong versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
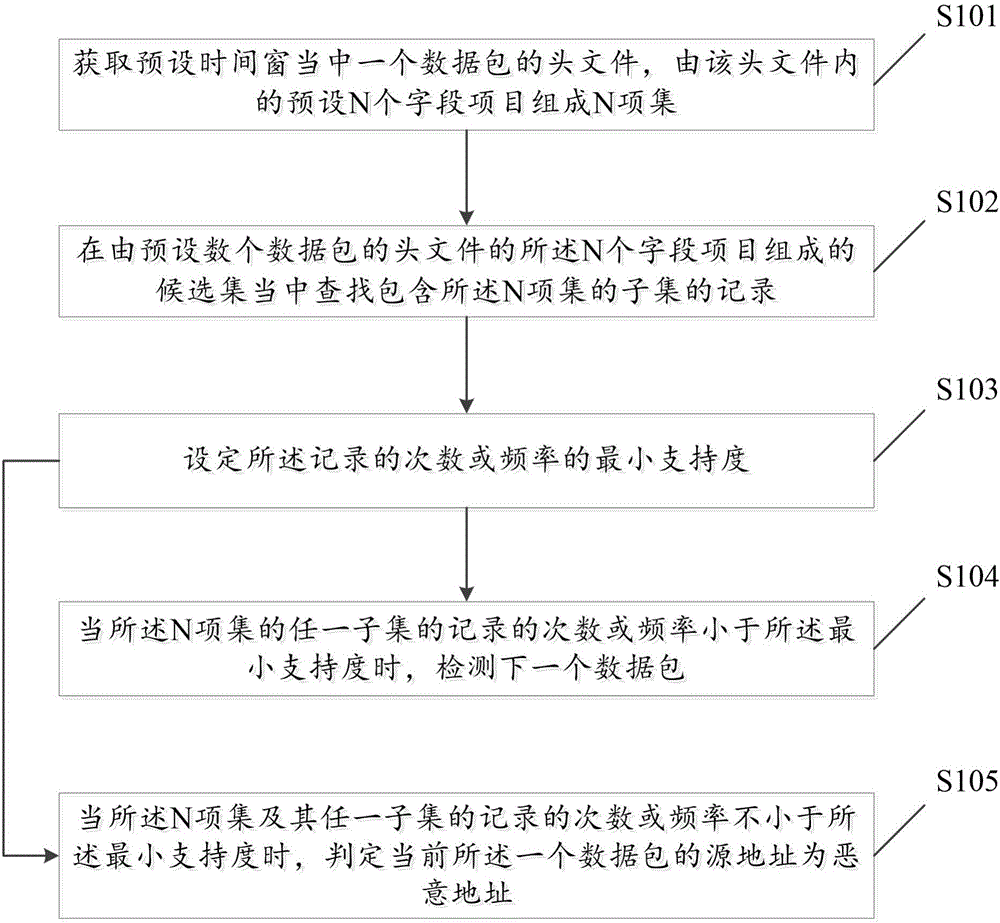
[0069] figure 2 It is a flow chart of the first embodiment of a detection method based on a malicious address in a DDOS attack of the present invention, including:
[0070] S101: Obtain a header file of a data packet in a preset time window, and form an N item set from preset N field items in the header file;
[0071] S102: Search for a record containing a subset of the N item set among the candidate sets consisting of the N field items of the header files of several preset data packets;
[0072] S103: Set the minimum support for the number of times or frequencies of the records;
[0073] S104: When the number or frequency of records of any subset of the N-itemset is less than the minimum support, detect the next data packet;
[0074]S105: When the number or frequency of records of the N-itemset and any subset thereof is not less than the minimum support, determine that the current source address of the one data packet is a malicious address.
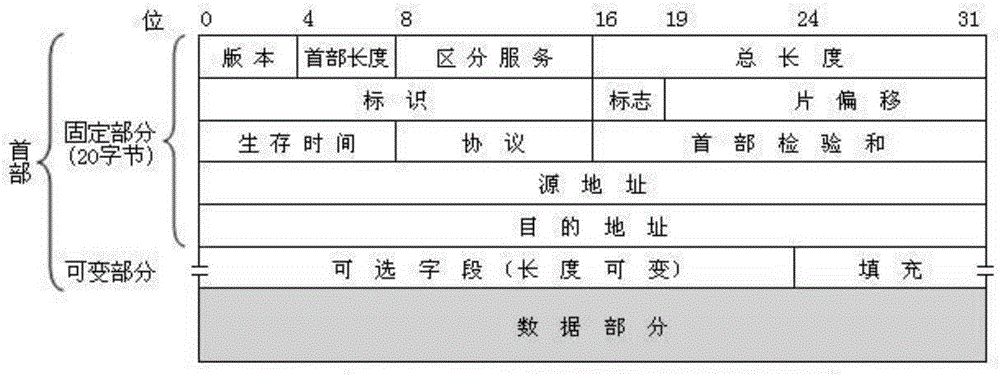
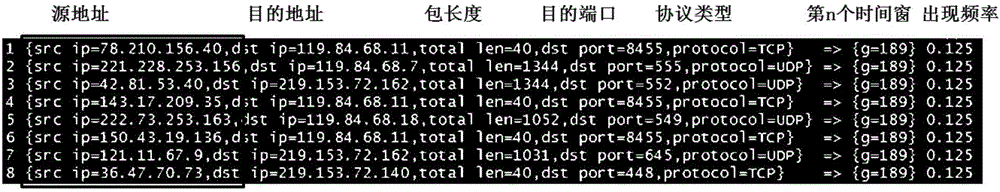
[0075] image 3 It is a sch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com