A method for active detection and vulnerability warning of assets
An active detection and asset technology, applied in the field of Internet security, can solve problems such as regulatory asset loopholes, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in further detail below in conjunction with the accompanying drawings, but it is not intended to limit the present invention.
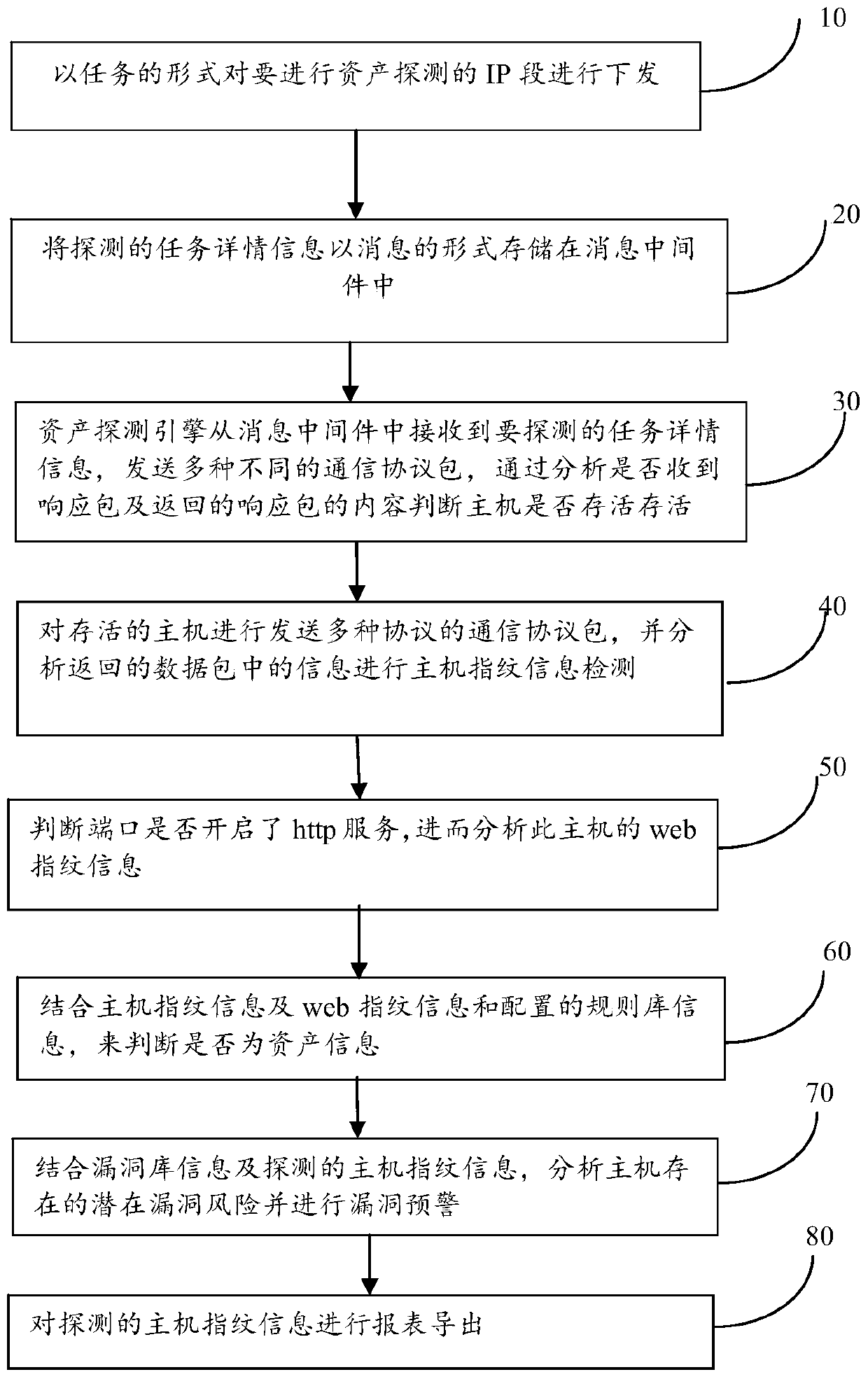
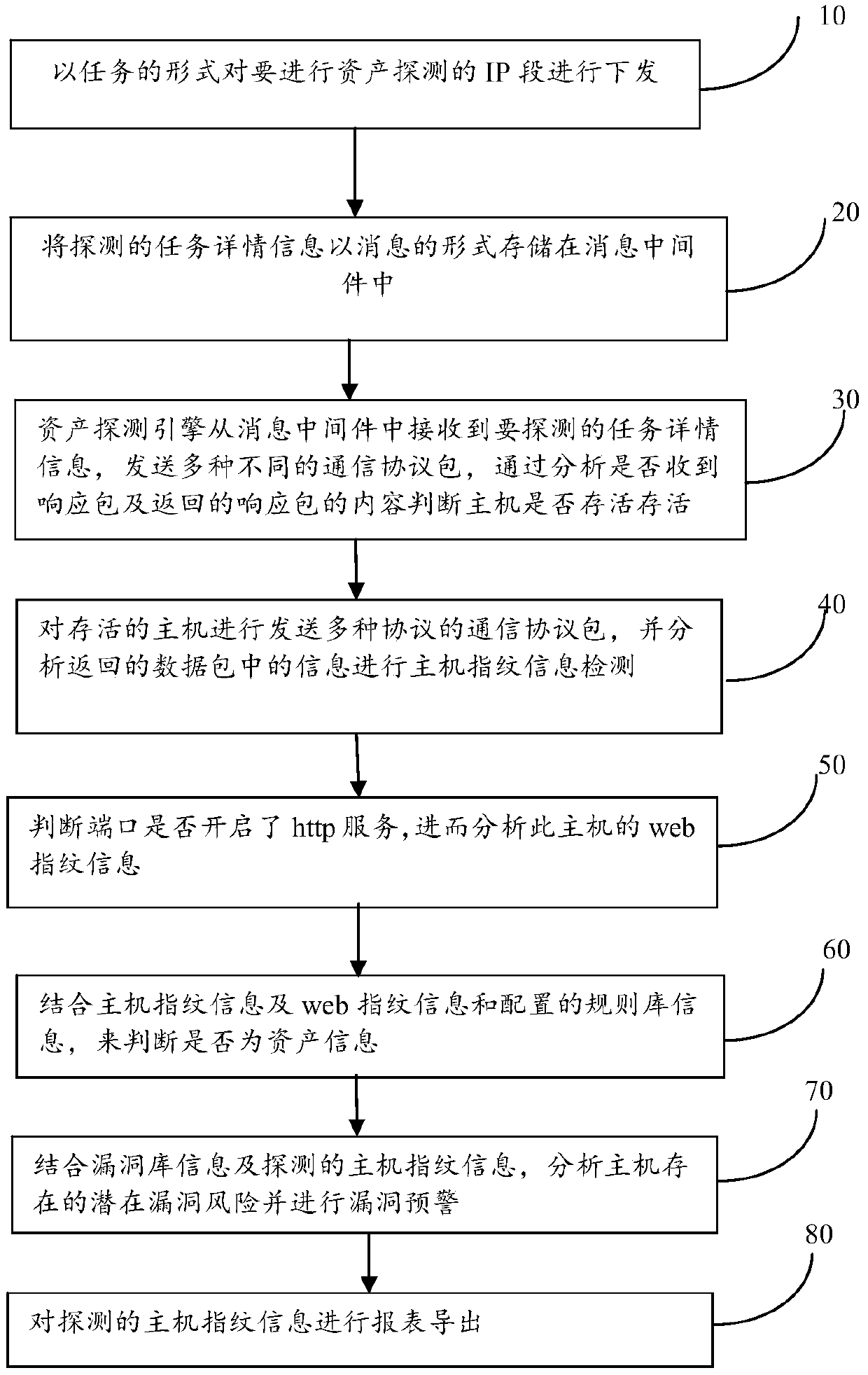
[0043] A method for active asset detection and vulnerability warning proposed by the present invention mainly includes the following steps:
[0044] Step 10, issue the IP segment of the asset to be detected in the form of a task;
[0045] Step 20, storing the detected task details information in the message middleware (MQ) in the form of a message;
[0046] Among them, after the IP segment of the asset to be detected is issued in the form of a task in step 10, in step 20, the survivability of the IP is first detected to determine whether the IP is alive, and if it is alive, the subsequent step 30 is executed Operation and follow-up steps, if not survived, follow-up steps will not be performed.
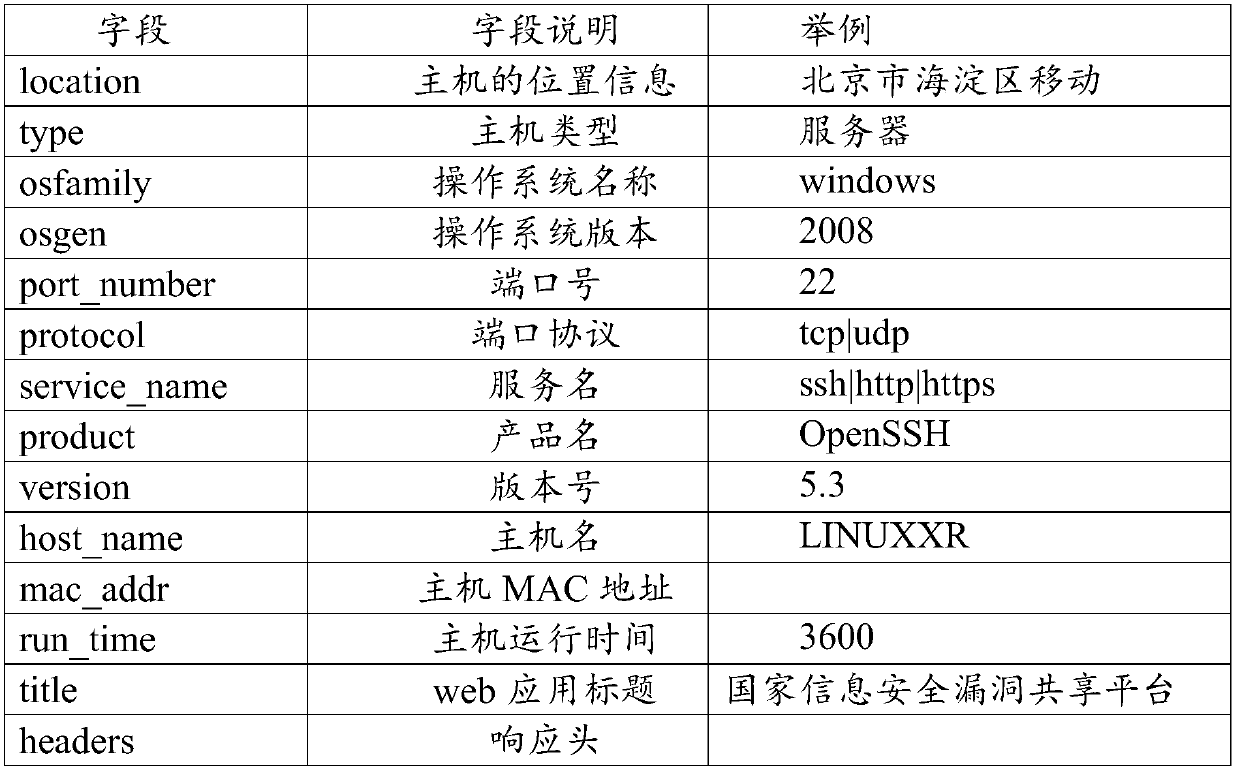
[0047] Step 30, the asset detection engine receives the task details information to be detected from the mess...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com