Network security processing method and device
A network security and processing method technology, applied in the field of network security processing methods and devices, capable of solving problems such as intranet host attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
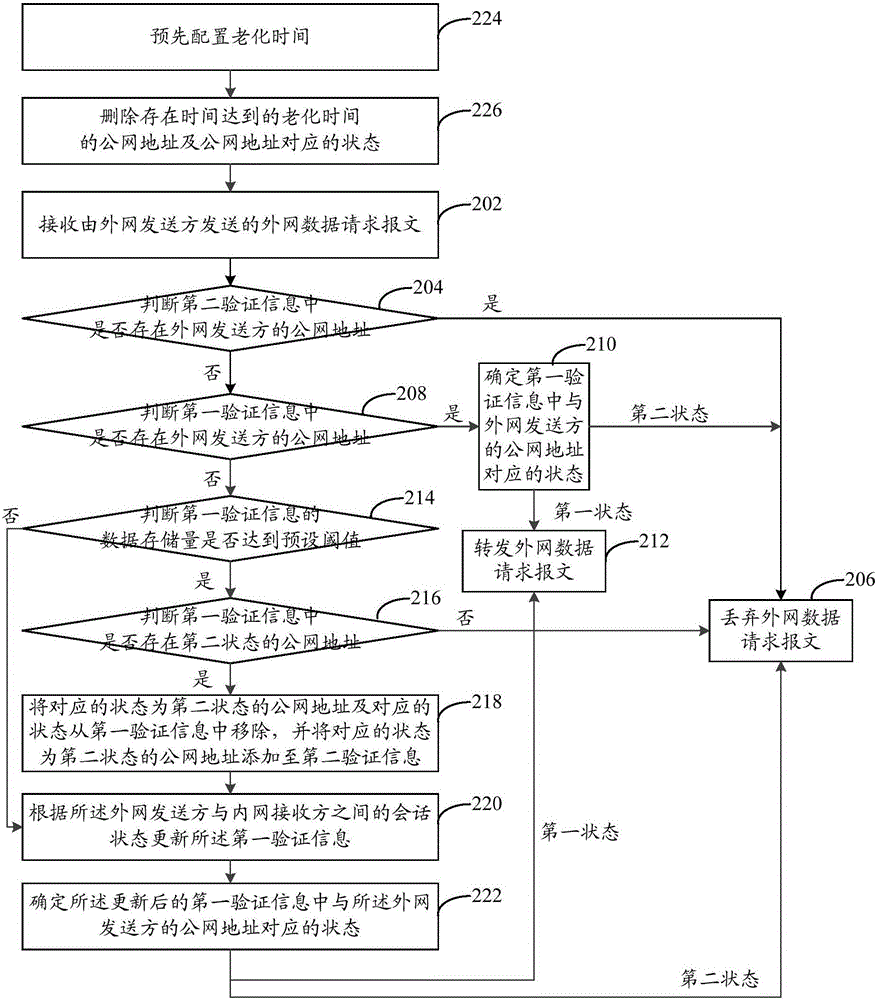
[0025] refer to figure 1 , shows a flow chart of steps of a network security processing method in the embodiment of the present application. In this embodiment, the network security processing method may be, but not limited to, applied to data interaction between an external network device (external network sender) and internal and external devices (intranet receiver).
[0026] Wherein, the network security processing method includes:
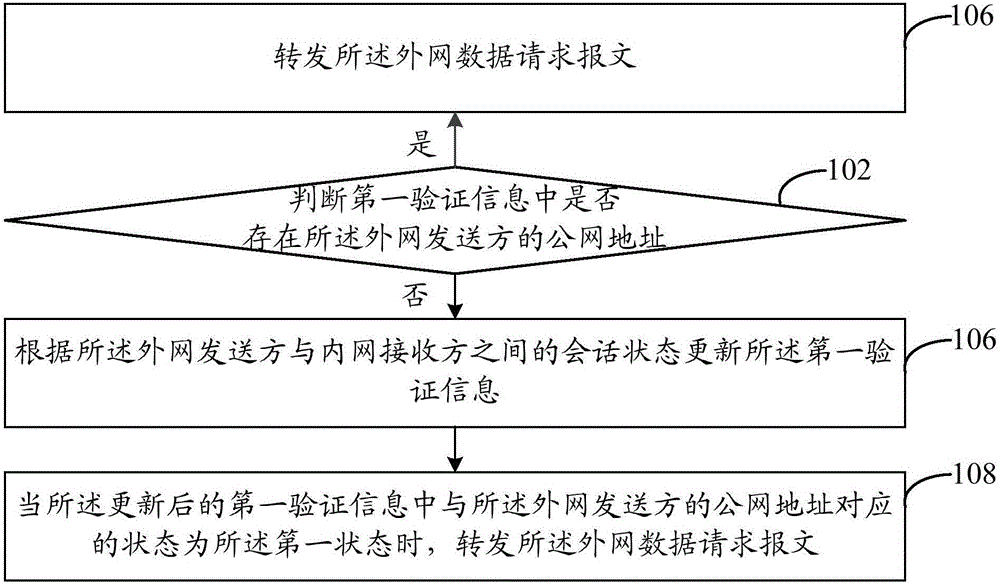
[0027] Step 102, when receiving the external network data request message sent by the external network sender, determine whether the public network address of the external network sender exists in the first verification information.
[0028] Generally, the data exchange...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com