Virtualization software protecting method having data stream confusion function
A technology of virtualization software and data flow, applied in the field of computer security, can solve problems such as inability to resist reverse analysis well, achieve the effect of increasing the difficulty of semantic analysis and wide applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
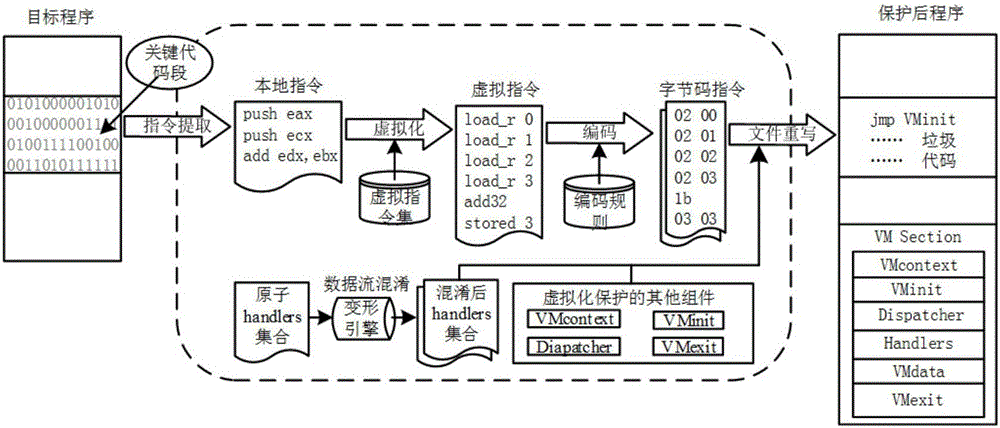
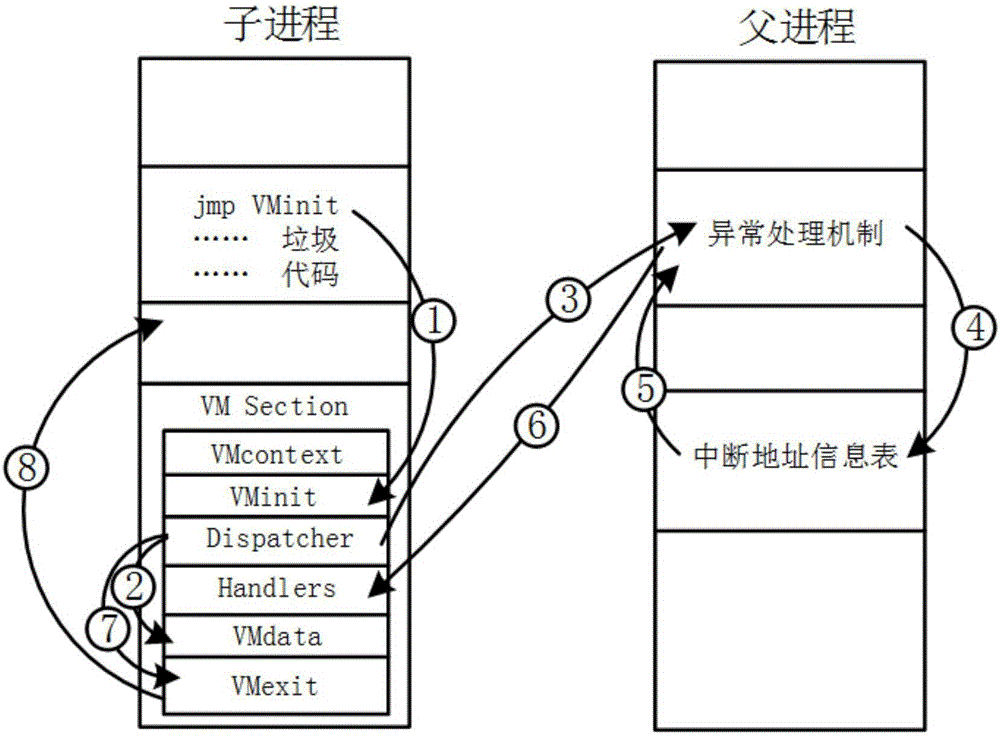
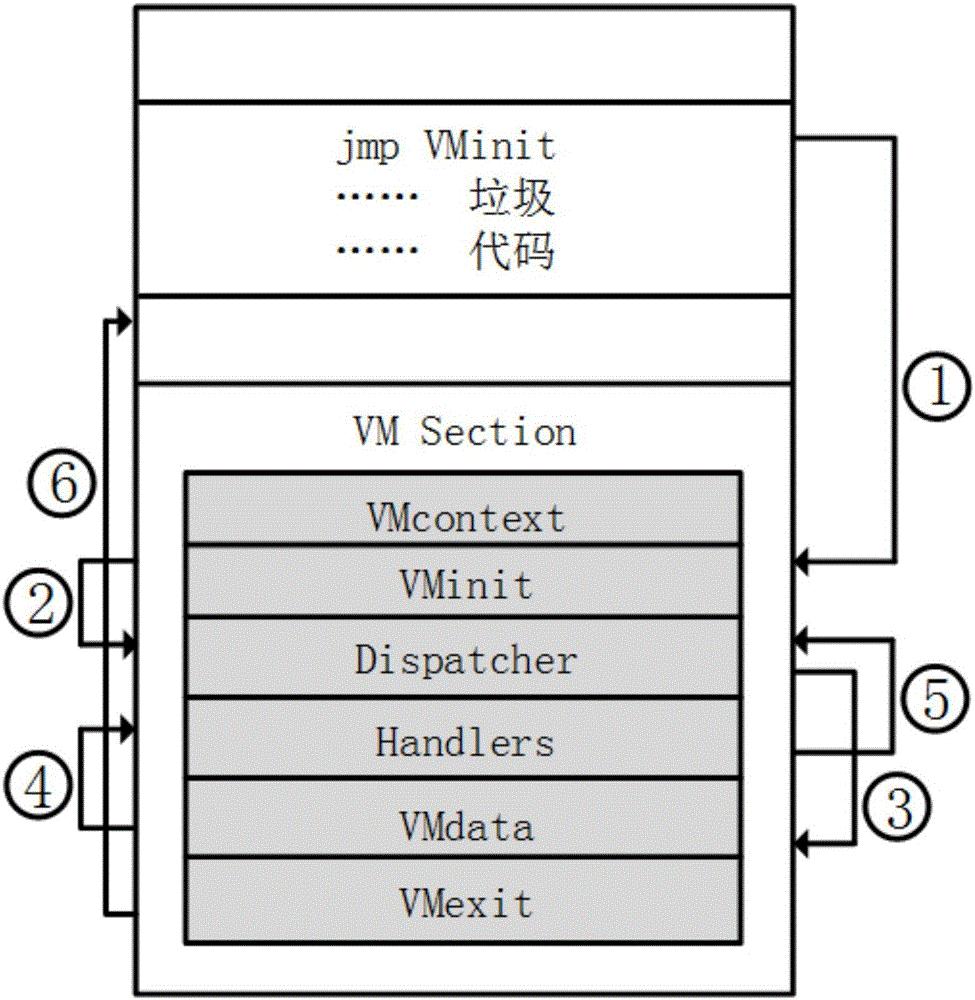
[0037] The present invention proposes a virtualization software protection method with data flow confusion, comprising the following steps:
[0038] Step 1, verify whether the file to be protected loaded is a PE file, if so, proceed to the next step; PE file in the present invention refers to the mainstream executable file format on the windows platform, such as: .exe file.dll file etc.
[0039] Step 2, specify the key code segment that needs to be protected on the source code segment of the file to be protected, and disassemble the key code segment to obtain the x86 instruction set of the key code segment;
[0040] The key code segment refers to the key code that needs to be protected specified by the user on the source code. The SDK start tag is embedded at the beginning of the key code segment, and the SDK end tag is embedded at the end. SDK is DFO-VMP (A Virtual Software Protection Method with Data Flow Obfuscation) defines a set of start and end markers. After the PE fil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com