Data security abnormity monitoring method and system in public information platform
A technology for data security and public information, applied in the field of data security, it can solve problems such as frequent changes, difficult real-time response of algorithms, and difficulty in identifying data categories.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
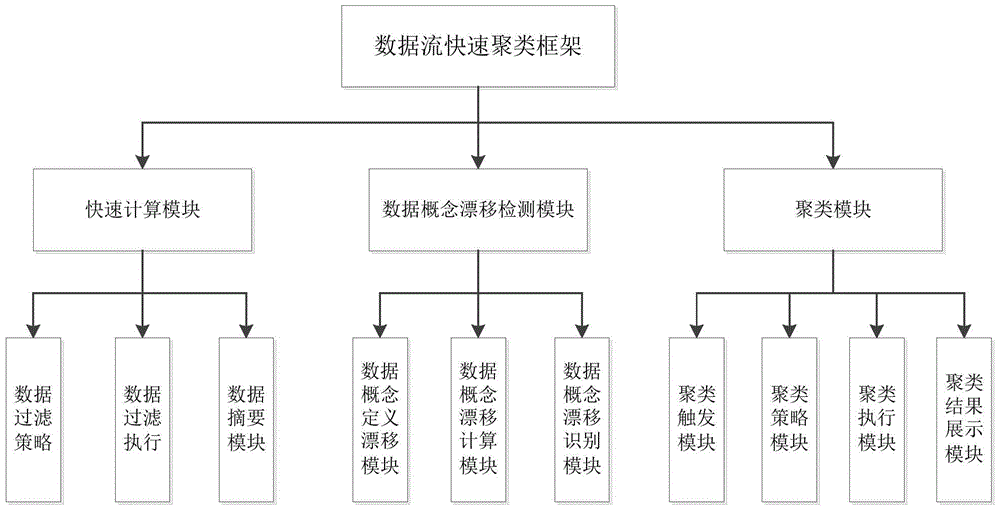
[0035] Example: see figure 1 , figure 2 , image 3 with Figure 4 ,
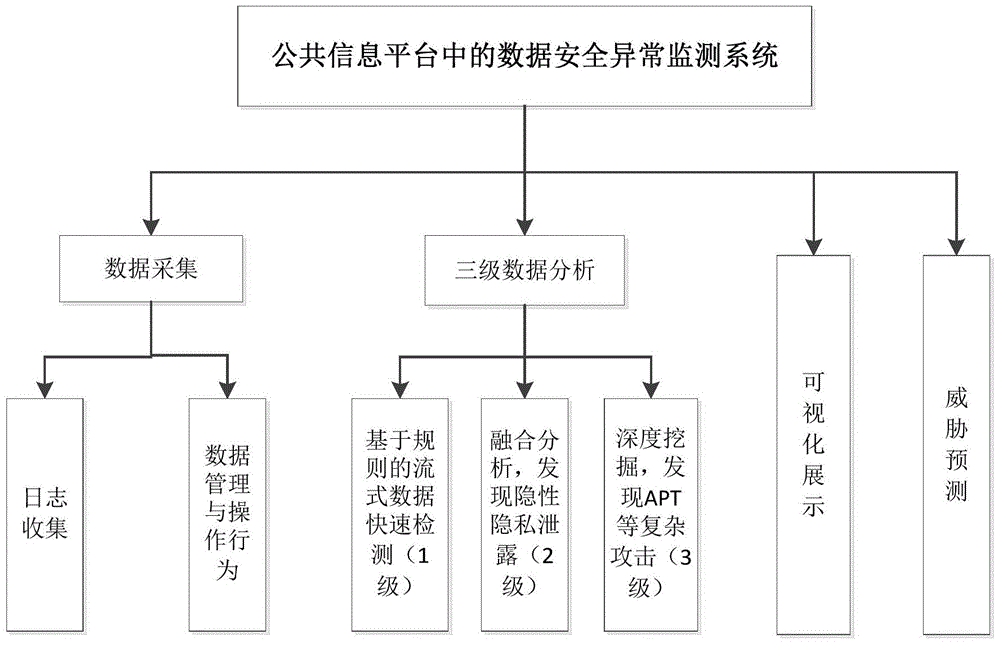
[0036] This patent adopts the idea of "three-level analysis and detection" to construct the data security anomaly monitoring system architecture in the public information platform, and uses different methods to analyze whether there is abnormal behavior in the system according to different scenarios. framework such as figure 1 Shown:
[0037] The system is divided into data layer, analysis layer and display layer. The basic data mainly comes from: ①The operation behavior of the bypass shunt to the data, and the protocol analysis to obtain its behavior data; ②Obtain system logs, device logs, application logs and database logs, etc.; ③Collect intranet security log information at the same time. The analysis layer adopts a three-level analysis method to analyze the data at different granularities. The presentation layer mainly uses visualization technology to visually display security threats to help d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com